1 Introduction
The standard framework in auction theory models bidders as strategic agents but assumes that the seller is non-strategic—i.e., that the seller can commit herself to faithfully implementing the rules of the auction. Recent theoretical work by Akbarpour and Li (Reference Akbarpour and Li2020) relaxes this assumption. In particular, they allow the seller to deviate from the auction rules in ways that have innocent explanations—i.e., in ways that cannot be detected by bidders given the information they have. They define an auction to be credible if there is no scope for the seller to break the rules without being detected.Footnote 1
As a concrete example, consider the first-price and second-price sealed-bid auctions for the sale of a single item. It is easy to see that the first-price auction is credible. The seller cannot cheat without being detected, since the winner knows her own bid and therefore knows how much she should be charged. The second-price auction, however, is not credible. After observing all the bids, the seller can exaggerate the second-highest bid and overcharge the winning bidder up to the amount of her own bid. Moreover, this type of cheating cannot be detected by the winner as long as she does not observe the second-highest bid. In the language of Akbarpour and Li (Reference Akbarpour and Li2020), the seller’s behavior is supported by the innocent explanation that the highest and second-highest bids are identical.
Credibility is not just a theoretical concern, but also a tangible property of auctions that can have significant real-world implications. Indeed, Akbarpour and Li (Reference Akbarpour and Li2020) provide anecdotal evidence of a seller taking advantage of the lack of credibility in a second-price auction:
An auctioneer running second-price auctions in Connecticut admitted, ‘After some time in the business, I ran an auction with some high mail bids from an elderly gentleman who’d been a good customer of ours and obviously trusted us. My wife Melissa, who ran the business with me, stormed into my office the day after the sale, upset that I’d used his full bid on every lot, even when it was considerably higher than the second-highest bid.’ (Lucking-Reiley, Reference Lucking-Reiley2000).
The suspicion that second-price auctions are often rigged in this fashion can affect both entry and bidding decisions. First, bidders may simply choose not to participate in second-price auctions. This would undermine the market design objective of creating sufficiently "thick" marketplaces, and also decrease the expected revenue from running these types of auctions. Second, bidders who still choose to participate may adjust their bidding strategies accordingly. This latter point undermines the common argument for the use of second-price auctions: that strategy-proof mechanisms provide a level playing field and save participants from the cognitive/monetary costs of plotting their strategies. More generally, we would expect the problems arising from non-credible auctions to be exacerbated in settings where bidders receive limited feedback (e.g., sealed-bid auctions), where bidders are not physically present when the auction is conducted (e.g., auctions that allow for online, mail, or telephone bidding), or where reputational concerns play a weaker role (e.g., markets with a single seller or a large number of homogeneous sellers).
However, there are no existing empirical studies on the performance of non-credible auctions. This is an important gap to fill. Non-credible auctions may present a challenge for bidders, who must cope with an additional dimension of strategic uncertainty: identifying optimal bidding strategies now requires considering the actions of the seller as well as other bidders. To that end, it also not obvious to what extent sellers will take advantage of the lack of credibility in auction settings.
In this paper, we bring empirical evidence to bear on these questions by providing the first direct test of how the credibility of an auction format affects bidding behavior and final outcomes. To do so, we conduct a laboratory experiment in which each subject participates in one of the following three treatments: the first-price auction (FP), the credible second-price auction (CSP), and the non-credible second-price auction (NCSP).Footnote 2 In all three treatments, the role of the seller is played by a subject who receives the revenue from the auction. In the FP and CSP treatments, the seller’s role is passive and the outcome of the auction is determined according to the prescribed rules. In the NCSP treatment, the seller has an active role. In particular, the NCSP auction is implemented as a dynamic game with two stages: bidders submit their bids in sealed envelopes (after observing their private values), and then the seller determines the outcome of the auction (after observing the bids).
To resolve equilibrium selection, we focus attention on the symmetric Perfect Bayesian equilibrium in undominated strategies. This provides a sharp theoretical prediction for both sides of the market. Sellers will select the highest bidder as the winner and choose a price equal to the highest bid. Bidders will internalize this and bid “as if” they are participating in a first-price auction. Taken together, the core theoretical prediction is the strategic equivalence of the NCSP and FP auctions.
While our results are qualitatively consistent with the theory, the main theoretical prediction is not borne out. Although sellers in the NCSP auction often break the rules of the auction and overcharge the winning bidder, they typically do not maximize revenue. Consequently, most bidders in the NCSP auction do not behave as though they are participating in a FP auction. In fact, the estimated bidding function in the NCSP auction is significantly different than the estimated bidding functions in both the FP and CSP auctions. This suggests that bidders perceive the three auctions as distinct mechanisms from a behavioral perspective.
As a next step, we consider a behavioral model in which sellers are averse to rule-breaking. We show that the model generates predictions that are consistent with our experimental results. To test the underlying mechanism of the model, we conduct an additional experimental treatment using a “no-rules” version of the NCSP auction. The new treatment provides support for aversion to rule-breaking as the driving force behind our results. In particular, we find that both bidders and sellers react to the absence of auction rules by behaving closer to the theoretical predictions for the FP auction.
The paper that is closest to ours in terms of design is Bartling et al. (Reference Bartling, Gesche and Netzer2017), who also conduct an experimental investigation of second-price auctions in the presence of human sellers. However, since the focus of their experiment is on how social preferences affect bidding behavior, sellers only receive the revenue from the auction but do not have agency to determine the outcome of the auction (which is the novel feature of our design). Our paper also replicates and extends well-known findings from the experimental auction literature.Footnote 3 In particular, our results have a natural connection to those reported in the seminal paper of Kagel et al. (Reference Kagel, Harstad and Levin1987). Consistent with Kagel et al. (Reference Kagel, Harstad and Levin1987), we find that overbidding relative to the risk-neutral Nash equilibrium prediction is common in the FP auction and overbidding relative to the dominant-strategy prediction still occurs in the CSP auction. Our experiment also demonstrates that bidding behavior varies between two theoretically equivalent institutions (FP and NCSP auctions). This finding mirrors the more general failure of strategic equivalence between static and dynamic auction procedures that was famously reported in Kagel et al. (Reference Kagel, Harstad and Levin1987). Finally, our paper joins a significant body of experimental work on the performance of auctions in the presence of behavioral agents—e.g., regret-averse bidders in Filiz-Ozbay and Ozbay (Reference Filiz-Ozbay and Ozbay2007) and level-k bidders in Crawford and Iriberri (Reference Crawford and Iriberri2007).
Although our main contribution is experimental, our paper is also thematically related to the literature on mechanism design with limited commitment. In particular, Baliga et al. (Reference Baliga, Corchon and Sjöström1997) and Bester and Strausz (Reference Bester and Strausz2001) study environments where the designer has agency to determine the outcome of the mechanism, which is a feature that is reflected prominently in our experiment. In more general allocation problems, Hakimov and Raghavan (Reference Hakimov and Raghavan2021) introduce the related concepts of “verifiability” (i.e., mechanisms that allow participants to check if their assignments are correct) and “transparency” (i.e., mechanisms in which the designer cannot cheat without being detected). Taken together, these concepts are stronger than the notion of credibility we investigate in this paper. The issue of seller cheating has also drawn significant attention in the field of industrial organization—e.g., the practice of “shill-bidding” by sellers in second-price auctions (McAdams & Schwarz, Reference McAdams and Schwarz2007; Rothkopf & Harstad, Reference Rothkopf and Harstad1995; Porter & Shoham, Reference Porter and Shoham2005).
The rest of the paper proceeds as follows. Section 2 introduces the theoretical framework, Sect. 3 provides details of the experimental design, Sect. 4 presents the experimental results, Sect. 5 investigates the underlying mechanism driving our experimental results, and Sect. 6 concludes.
2 Theoretical background
We present a simple operationalization of the environment in Akbarpour and Li (Reference Akbarpour and Li2020). There is a single, indivisible item for sale. Let
![]() be a finite set of agents, consisting of
be a finite set of agents, consisting of
![]() bidders and a seller (player 0). Let X be a set of outcomes, where an outcome
bidders and a seller (player 0). Let X be a set of outcomes, where an outcome
![]() consists of a winner
consists of a winner
![]() and a profile of payments
and a profile of payments
![]() such that
such that
![]() for
for
![]() . A type space is
. A type space is
![]() , where
, where
![]() . Let
. Let
![]() denote a marginal distribution over types.Footnote 4 The distribution F is common knowledge. The bidding function of player i is given by
denote a marginal distribution over types.Footnote 4 The distribution F is common knowledge. The bidding function of player i is given by
![]() .
.
After observing the profile of bids
![]() , the seller selects the winner
, the seller selects the winner
![]() and the price of the item
and the price of the item
![]() .Footnote 5 The feedback that bidders receive is captured by a partition
.Footnote 5 The feedback that bidders receive is captured by a partition
![]() of X for each
of X for each
![]() , representing what bidder i directly observes about the outcome.Footnote 6 In particular,
, representing what bidder i directly observes about the outcome.Footnote 6 In particular,
![]() if and only if one of the following two conditions holds: (1)
if and only if one of the following two conditions holds: (1)
![]() and
and
![]() , or (2)
, or (2)
![]() and
and
![]() . That is, each bidder observes whether she wins the item and observes her own payment.
. That is, each bidder observes whether she wins the item and observes her own payment.
We now describe the preferences of the players. Bidders have private values:
![]() for player
for player
![]() . The seller receives the revenue from the auction:
. The seller receives the revenue from the auction:
![]() . We focus attention on the symmetric Perfect Bayesian equilibrium in undominated strategies. Let
. We focus attention on the symmetric Perfect Bayesian equilibrium in undominated strategies. Let
![]() ,
,
![]() ,
,
![]() denote the symmetric and strictly increasing equilibrium bidding functions in the first-price, non-credible second-price, and credible second-price auctions, respectively.
denote the symmetric and strictly increasing equilibrium bidding functions in the first-price, non-credible second-price, and credible second-price auctions, respectively.
Proposition 1
In equilibrium,
(i) the seller selects the highest bidder as the winner.
(ii) chooses a price equal to the highest bid. That is,

(iii) for each bidder
 and each value
and each value
 , we have that
, we have that

We omit the proof of Proposition Footnote 1 since it follows directly from the results presented in Akbarpour and Li (Reference Akbarpour and Li2020). However, we note that Proposition Footnote 1 provides a clear testable prediction that the NCSP auction is theoretically equivalent to the FP auction.
3 Experimental design
Our experiment consists of three players (two buyers and one seller) participating in a sealed bid auction for a single fictitious commodity. Each play of the auction is a round. Subjects play 10 rounds in an experimental session. At the beginning of the experiment, each subject is randomly assigned to the role of either a buyer (2/3 chance) or a seller (1/3 chance). Subjects’ roles are fixed across all 10 rounds, but subjects are randomly and anonymously re-matched into groups of three at the start of each round. We use a hypothetical currency (tokens) to keep track of subjects’ earnings throughout the experiment. Each subject starts the experiment with a token balance: buyers start with 100 tokens and sellers start with 0 tokens. At the end of a round, each subject’s earnings are added to her token balance. At the end of the experiment, each subject is paid the sum of her final token balance (where 20 tokens = £1) and her payoff from two elicitation tasks.Footnote 7
We now describe the general structure of the experiment. At the beginning of a round, each buyer is randomly given a value for the item. The values are drawn independently and uniformly from the set of integers between 0 and 100 (inclusive). The buyers’ values are private information. Each buyer independently and simultaneously submits a bid for the item.Footnote 8
The outcome of the auction depends on the treatment. We use a between-subject experimental design where each subject participates in one of the following three conditions:
(1) Credible second-price auction (CSP): The buyer who submits the highest bid wins the item. The price of the item is equal to the amount of the lowest bid.
(2) Non-credible second-price auction (NCSP): The seller can select either buyer as the winner and can set the price of the item to be any amount that is not greater than the winner’s bid.
(3) First-price auction (FP): The buyer who submits the highest bid wins the item. The price of the item is equal to the amount of the highest bid.
In all three conditions, each buyer observes whether she won the item. Only the winner and the seller observe the price of the item. The winner receives her value for the item, minus the price of the item. The seller receives the price of the item.
There are a few important points to make about our design choices. First, since we are interested in how the credibility of an auction format affects bidding behavior, we need to eliminate seller reputation as a possible explanation for our results. Our random and anonymous re-matching protocol does precisely this: buyers are unaware of sellers’ identities and whether they have interacted with a particular seller in a previous round. Second, an important feature of our experiment is that a subject always plays the role of the seller and receives the revenue from the auction. We maintain this feature even in the two auctions with passive sellers (CSP and FP), which allows us to rule out social preferences or fairness concerns as possible explanations for differences in bidding behavior in the NCSP auction. Third, our experimental auction markets consist of one seller and only two buyers. This is the simplest possible setting in which credibility plays a role, and thus provides a clean test of the theory. We do not view this as overly restrictive or harmful to external validity, since many real-world auctions also feature a small number of active bidders.Footnote 9 Finally, we acknowledge that it is a challenge to successfully induce a non-credible auction in the laboratory. In particular, it is crucial that both the rules of the auction and the seller’s strategy space are common knowledge. Our experimental instructions emphasize both of these features.Footnote 10 We also include a quiz to verify subjects’ comprehension of the instructions. The experiment does not begin until each subject correctly answers all the quiz questions.
3.1 Implementation
The experimental sessions were run at the Laboratory for Economic and Decision Research (LEDR) at the University of East Anglia. For the main set of experiments, we recruited a total of 285 subjects across 13 sessions (with either 18, 21, or 24 subjects per session). Each session lasted approximately 60 min. The experiment was programmed and conducted with the z-Tree software (Fischbacher, Reference Fischbacher2007). Table 1 provides more detailed summary statistics.
Table 1 Overview of experimental design
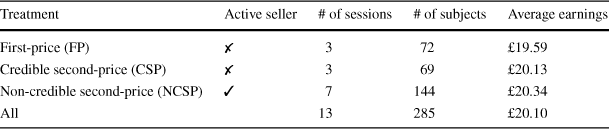
|
Treatment |
Active seller |
# of sessions |
# of subjects |
Average earnings |
|---|---|---|---|---|
|
First-price (FP) |
✗ |
3 |
72 |
£19.59 |
|
Credible second-price (CSP) |
✗ |
3 |
69 |
£20.13 |
|
Non-credible second-price (NCSP) |
|
7 |
144 |
£20.34 |
|
All |
13 |
285 |
£20.10 |
4 Experimental results
4.1 Bidder behavior
We begin by investigating bidding behavior. For the case of two risk-neutral bidders with values independently and uniformly drawn from [0, 100], the symmetric Perfect Bayesian Equilibrium (PBE) predictions in undominated strategies are given by
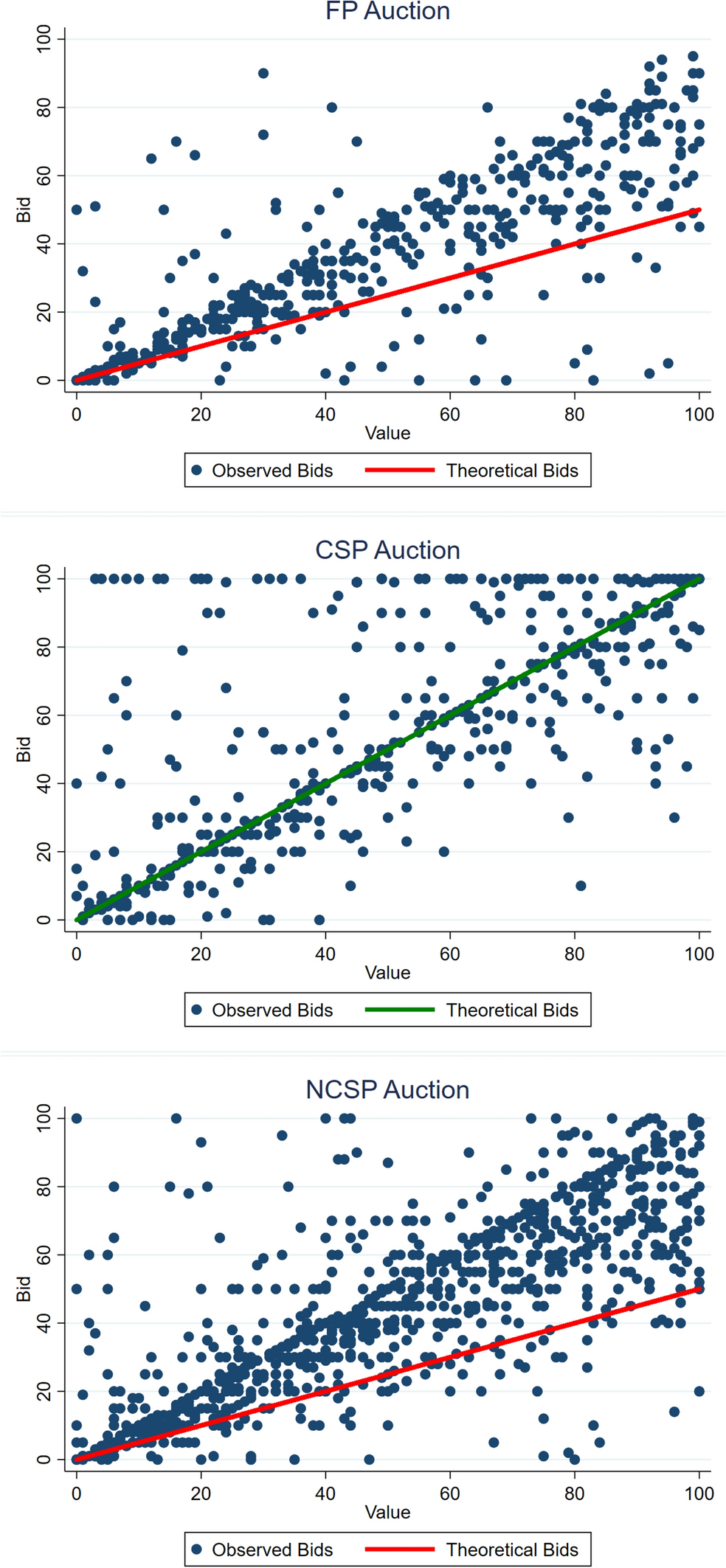
Fig. 1 Observed and theoretical bids
Figure 1 shows scatter plots of observed bids/values in the three treatments, along with the theoretical predictions in solid lines. It is clear that overbidding relative to the equilibrium prediction is common in the FP and NCSP auctions, occurring in 86% (411/480) and 89% (853/960) of bid-value pairs, respectively. In the CSP auction, however, subjects have a dominant strategy of bidding their true values. Although overbidding still occurs in 39% (181/460) of cases, 18% (85/460) of cases correspond to dominant-strategy play. If we relax this condition to include subjects who bid either 1 token below or 1 token above their true values, then 28% (127/460) of cases correspond to dominant-strategy play.
As a next step, we conduct linear estimations of the bidding functions (forcing the intercepts to pass through zero).Footnote 11 Regression 1 in Table 2 shows the estimated bidding functions for the three treatments, with the NCSP auction as the baseline. In particular, we have that
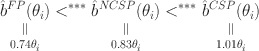
Notice that the estimated slopes of the bidding functions are significantly different at the 1% level. This generates two main insights. First, contrary to theoretical predictions, the NCSP auction fails to converge to the FP auction. Second, the NCSP auction is still behaviorally distinct from the CSP auction. Overall, bidders’ behavior is consistent with the belief that sellers in the NCSP auction are choosing an intermediate price between the highest and second-highest bids. We will return to this intuition later when we investigate seller behavior.
Table 2 Linear estimates of the bidding functions (passing through the origin). Standard errors are clustered at the subject level
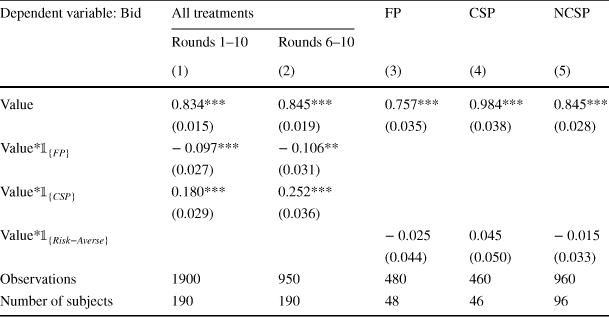
|
Dependent variable: Bid |
All treatments |
FP |
CSP |
NCSP |
|
|---|---|---|---|---|---|
|
Rounds 1–10 |
Rounds 6–10 |
||||
|
(1) |
(2) |
(3) |
(4) |
(5) |
|
|
Value |
0.834*** |
0.845*** |
0.757*** |
0.984*** |
0.845*** |
|
(0.015) |
(0.019) |
(0.035) |
(0.038) |
(0.028) |
|
|
Value*
|
− 0.097*** |
− 0.106** |
|||
|
(0.027) |
(0.031) |
||||
|
Value*
|
0.180*** |
0.252*** |
|||
|
(0.029) |
(0.036) |
||||
|
Value*
|
− 0.025 |
0.045 |
− 0.015 |
||
|
(0.044) |
(0.050) |
(0.033) |
|||
|
Observations |
1900 |
950 |
480 |
460 |
960 |
|
Number of subjects |
190 |
190 |
48 |
46 |
96 |
Significance levels are indicated as follows: **
![]() , ***
, ***
![]()
We conduct several robustness checks. First, we account for the possibility of subject learning over time. Regression 2 in Table 2 estimates the bidding functions only using data from the last five rounds of the experiment. Our qualitative results remain unchanged. Second, we investigate the effect of risk preference on bidding behavior.Footnote 12 We do this separately for each treatment, since the interplay between risk preference and bidding behavior varies across the different auction formats. The results are shown in Regressions 3–5 in Table 2. In all three auctions, we find that risk-averse subjects do not bid significantly differently than other subjects.Footnote 13 This finding is consistent with the theoretical prediction for the CSP auction (where subjects have a dominant strategy), but inconsistent with the theoretical predictions for the FP and NCSP auctions (where risk-averse subjects should bid more aggressively).
Finally, we analyze bidding behavior at the subject level. The data for each bidder consists of 10 pairs of bids and values (one for each round of the experiment). For each bidder, we calculate her bid/value coefficient as the average of her 10 bid/value ratios. The cumulative distribution functions (CDFs) of the bid/value coefficients are shown in Fig. 2. Several patterns are clear by inspection. First, the fact that bid/value coefficients exceed 1 for many subjects reveals the prevalence of dominated strategies in the data. Second, we observe a first-order stochastic dominance relationship when comparing the CDFs of either the FP or NCSP treatments to the CSP treatment. Using a Kolmogorov–Smirnov test, we can also reject the null hypothesis that bid/value coefficients are drawn from the same underlying distribution in all three pairwise comparisons (
![]() in all cases). This further underscores the point that bidding behavior is significantly different across the three auction institutions.
in all cases). This further underscores the point that bidding behavior is significantly different across the three auction institutions.
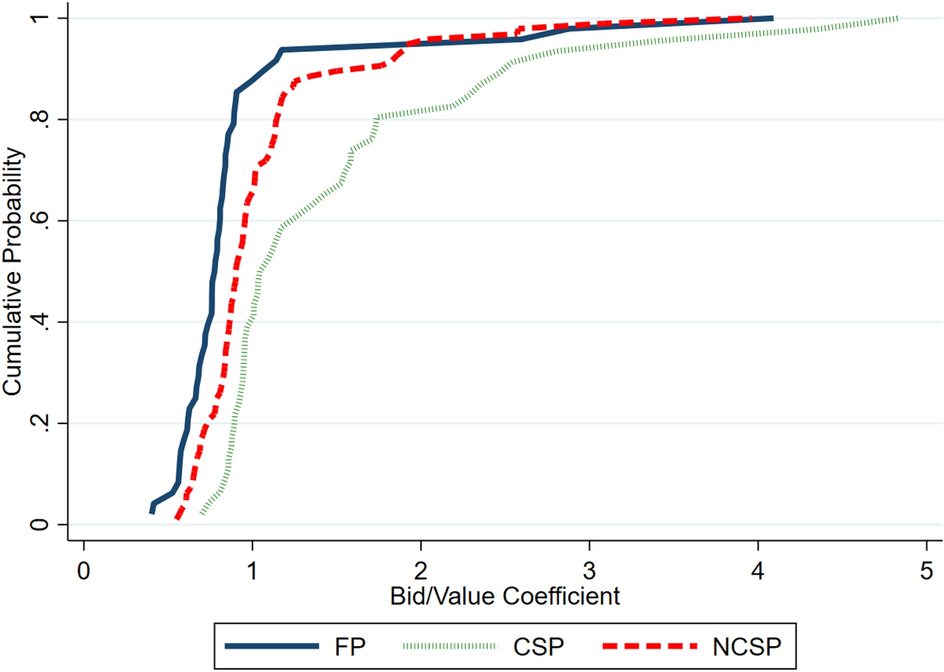
Fig. 2 CDFs of bid/value coefficients
4.2 Seller Behavior
We now investigate the behavior of sellers. In the credible auctions (FP and CSP treatments), the seller’s role is passive. Thus, our data consists only of the 48 sellers who participate in the NCSP treatment. Recall that each seller makes two choices in each round: she decides which bidder wins the item and the price of the item. We find that the seller selects the highest bidder as the winner in 99% (476/480) of cases. This behavior is consistent with both the dominant strategy of the seller and the rules of the auction. Furthermore, the fact that sellers nearly always allocate the item to the highest bidder provides a basic rationality check and rules out subject confusion as an explanation for our results.
We now explore the degree to which sellers break the rules of the auction when making pricing decisions. To do so, we define the “overcharging ratio”
![]() for seller i in round t of the experiment as
for seller i in round t of the experiment as
where
![]() is seller i’s chosen price in round t,
is seller i’s chosen price in round t,
![]() is the highest bid in seller i’s group in round t, and
is the highest bid in seller i’s group in round t, and
![]() is the lowest bid in seller i’s group in round t.Footnote 14 The ratio
is the lowest bid in seller i’s group in round t.Footnote 14 The ratio
![]() captures the share of surplus that is extracted by seller i in round t. If
captures the share of surplus that is extracted by seller i in round t. If
![]() , then the seller chooses a price equal to the lowest bid (i.e., she extracts no additional surplus beyond the amount prescribed by the rules of the auction). If
, then the seller chooses a price equal to the lowest bid (i.e., she extracts no additional surplus beyond the amount prescribed by the rules of the auction). If
![]() , then the seller chooses a price equal to the highest bid (i.e., she extracts the maximum possible surplus).Footnote 15
, then the seller chooses a price equal to the highest bid (i.e., she extracts the maximum possible surplus).Footnote 15
We first investigate whether sellers’ overcharging behavior changes with experience, and whether overcharging is correlated with a traditional measure of lying aversion taken from the literature.Footnote 16 The results are shown in Regressions 1–2 of Table 3. We find that sellers overcharge 29 percentage points more in the second half of the experiment than in the first half, and that lie-averse sellers overcharge 33 percentage points less than sellers who are not lie-averse. Although both of these results are consistent with our intuition, only the latter effect is statistically significant at conventional levels.
Table 3 OLS regressions of seller behavior in the NCSP auction. Standard errors are clustered at the subject level.

|
(1) |
(2) |
(3) |
|
|---|---|---|---|
|
Overcharging ratio |
Overcharging ratio |
Decision to overcharge |
|
|
|
0.289 |
||
|
(0.210) |
|||
|
|
− 0.333** |
||
|
(0.135) |
|||
|
Bid spread |
0.004*** |
||
|
(0.001) |
|||
|
Constant |
0.456** |
0.901*** |
0.690*** |
|
(0.218) |
(0.039) |
(0.058) |
|
|
Observations |
470 |
470 |
470 |
|
Number of subjects |
48 |
48 |
48 |
Significance levels are indicated as follows: **
![]() , ***
, ***
![]()
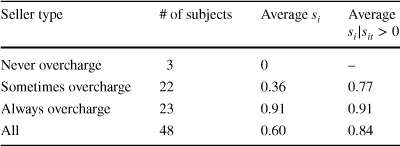
Table 4 Distribution of seller types in the NCSP auction
|
Seller type |
# of subjects |
Average
|
Average
|
|---|---|---|---|
|
Never overcharge |
3 |
0 |
– |
|
Sometimes overcharge |
22 |
0.36 |
0.77 |
|
Always overcharge |
23 |
0.91 |
0.91 |
|
All |
48 |
0.60 |
0.84 |
We now investigate the prevalence of different seller types in our experiment. In particular, we calculate the “overcharging coefficient”
![]() of seller i as the average of her 10 overcharging ratios (one for each round of the experiment). This allows us to classify sellers as one of three possible types: sellers who never overcharge, sellers who sometimes overcharge, and sellers who always overcharge. Table 4 shows the distribution of seller types in our experiment. It is clear that overcharging is the norm: only three sellers never overcharge in all rounds of the experiment (i.e.,
of seller i as the average of her 10 overcharging ratios (one for each round of the experiment). This allows us to classify sellers as one of three possible types: sellers who never overcharge, sellers who sometimes overcharge, and sellers who always overcharge. Table 4 shows the distribution of seller types in our experiment. It is clear that overcharging is the norm: only three sellers never overcharge in all rounds of the experiment (i.e.,
![]() ). We find that the 22 sellers who sometimes overcharge extract an average of 36% of the available surplus, while the 23 sellers who always overcharge extract an average of 91% of the available surplus. This difference is both economically and statistically significant (Mann–Whitney test,
). We find that the 22 sellers who sometimes overcharge extract an average of 36% of the available surplus, while the 23 sellers who always overcharge extract an average of 91% of the available surplus. This difference is both economically and statistically significant (Mann–Whitney test,
![]() ). Finally, of the 23 sellers who always overcharge, only six sellers consistently extract the maximum surplus (i.e.,
). Finally, of the 23 sellers who always overcharge, only six sellers consistently extract the maximum surplus (i.e.,
![]() ).
).
Taken together, our results suggest that most sellers in the NCSP auction are not profit-maximizing. We now analyze whether there are any systematic patterns in sellers’ deviations from profit-maximizing behavior. We focus on two main questions. First, do sellers who sometimes overcharge behave similarly to sellers who always overcharge, conditional on the decision to break the rules of the auction? We find that this is not the case. Conditional on overcharging, sellers who sometimes overcharge extract an average of 77% of the available surplus, which is still significantly different than the rate among sellers who always overcharge (Mann–Whitney test,
![]() ). Second, are sellers responsive to the size of the pecuniary gains associated with breaking the rules of the auction? In principle, the seller’s likelihood of overcharging the winner might be increasing in the difference between the maximum and minimum bids (i.e., the bid spread). To test this hypothesis, we estimate an OLS regression of a dummy variable for overcharging (i.e.,
). Second, are sellers responsive to the size of the pecuniary gains associated with breaking the rules of the auction? In principle, the seller’s likelihood of overcharging the winner might be increasing in the difference between the maximum and minimum bids (i.e., the bid spread). To test this hypothesis, we estimate an OLS regression of a dummy variable for overcharging (i.e.,
![]() ) on the bid spread.Footnote 17 The results are shown in Regression 3 of Table 3. We find a statistically significant effect: in particular, every 10 token increase in the bid spread increases the seller’s probability of overcharging the winner by four percentage points.
) on the bid spread.Footnote 17 The results are shown in Regression 3 of Table 3. We find a statistically significant effect: in particular, every 10 token increase in the bid spread increases the seller’s probability of overcharging the winner by four percentage points.
4.3 Aggregate outcomes
We now compare efficiency and revenue across the different auction formats. We use standard definitions: the outcome of an auction is efficient if the bidder with the highest value wins the item, and the revenue from an auction is the price of the item. If subjects use symmetric and strictly increasing bidding functions, then all three auctions are efficient. If these bidding functions are also an equilibrium, then all three auctions yield the same expected revenue for the seller.Footnote 18 In the case of two bidders with values independently and uniformly distributed on [0, 100], the expected revenue is 33.
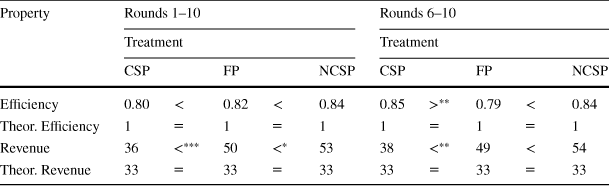
Table 5 Average efficiency and revenue
|
Property |
Rounds 1–10 |
Rounds 6–10 |
||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
Treatment |
Treatment |
|||||||||
|
CSP |
FP |
NCSP |
CSP |
FP |
NCSP |
|||||
|
Efficiency |
0.80 |
< |
0.82 |
< |
0.84 |
0.85 |
|
0.79 |
< |
0.84 |
|
Theor. Efficiency |
1 |
|
1 |
|
1 |
1 |
|
1 |
|
1 |
|
Revenue |
36 |
|
50 |
|
53 |
38 |
|
49 |
< |
54 |
|
Theor. Revenue |
33 |
|
33 |
|
33 |
33 |
|
33 |
|
33 |
Significance levels are indicated as follows: *
![]() , **
, **
![]() , ***
, ***
![]()
Table 5 documents the average efficiency and revenue in each treatment.Footnote 19 We observe high rates of efficiency in our experimental auction markets: the fraction of efficient outcomes is at least 80% in all three treatments.Footnote 20 Moreover, the differences in efficiency across the three treatments are not statistically significant. This finding is also robust to subject experience. When restricting attention to the last five rounds of the experiment, we observe similarly high rates of efficiency and only one significant treatment effect among the three pairwise comparisons.
We do observe significant differences in revenue across the three treatments. In particular, we find that the CSP auction generates the least revenue while the NCSP auction generates the most revenue. However, the only robust finding is the revenue inferiority of the CSP auction. The additional revenue generated by the NCSP auction over the FP auction is not economically significant and also fails to be statistically significant in the last five rounds of the experiment.
5 Underlying mechanism
Our experimental results show that the NCSP auction fails to converge to the FP auction. Most sellers in the NCSP auction do not maximally overcharge the winning bidder. Consequently, most bidders in the NCSP auction do not behave as though they are participating in a FP auction.
In this section, we investigate the reason for this failure of theoretical equivalence. First, we propose an alternative specification for the seller’s preferences that includes an aversion to rule-breaking. We then show that this behavioral model generates predictions that are consistent with our experimental results. Finally, we conduct an additional experimental treatment to test the underlying mechanism of the behavioral model.
5.1 Behavioral model
We consider a behavioral seller who is averse to rule-breaking. Since we restrict attention to equilibria in undominated strategies, the seller would never choose a price below the second-highest bid. Thus, we can characterize the price
![]() by a parameter
by a parameter
![]() as follows:
as follows:
where
![]() is the highest bid and
is the highest bid and
![]() is the second-highest bid.
is the second-highest bid.
For the seller, we allow for both a fixed cost and a variable cost of rule-breaking. The fixed cost of rule-breaking is represented by the parameter
![]() . The variable cost of rule-breaking is represented by the function
. The variable cost of rule-breaking is represented by the function
where
![]() is a continuous, monotone, and concave function such that
is a continuous, monotone, and concave function such that
![]() ,
,
![]() , and
, and
![]() . Then, the seller’s utility function is as follows:
. Then, the seller’s utility function is as follows:
We can now update the theoretical predictions for the case of a behavioral seller. Recall that
![]() ,
,
![]() ,
,
![]() denote the symmetric and strictly increasing equilibrium bidding functions in the first-price, non-credible second-price, and credible second-price auctions, respectively.
denote the symmetric and strictly increasing equilibrium bidding functions in the first-price, non-credible second-price, and credible second-price auctions, respectively.
Proposition 2
In equilibrium,
(i) the seller selects the highest bidder as the winner,
(ii) there exists
 such that the seller’s optimal strategy is
where
such that the seller’s optimal strategy is
where
 .
.
(iii) for each bidder
 and each value
and each value
 , we have that
, we have that 
Proof
See Appendix 1.
![]()
Proposition Footnote 2 provides two novel testable predictions. First, it predicts that the equilibrium bidding function in the NCSP auction is nested between the equilibrium bidding functions of the FP and CSP auctions. Intuitively, the NCSP auction is a convex combination of the other two auction formats, where the precise mixture depends on the seller’s degree of rule-breaking aversion. Second, it predicts that the seller will follow the rules of the auction when there are limited pecuniary gains from rule-breaking.
5.2 Revisiting the NCSP auction
In this section, we revisit the NCSP auction to demonstrate that the main predictions of the behavioral model are consistent with our experimental results.
Prediction 1
![]() .
.
This pattern is reflected in our data. Recall from Sect. 4 that the empirical bidding functions exhibit the predicted ordering and the estimated slopes are significantly different at the 1% level. We also find that 73% (702/960) of bid-value pairs in the NCSP auction lie between the theoretical bounds of the FP and CSP auctions.
Prediction 2
For a sufficiently small bid spread
![]() ,
,
![]() . In other words, the seller chooses the price
. In other words, the seller chooses the price
![]() .
.
In the NCSP auction, sellers choose a price equal to the second-highest bid in 20% (96/480) of cases. Furthermore, we find evidence that sellers are responsive to the bid spread when making their pricing decisions. In particular, Regression 3 of Table 3 shows that sellers are less likely to overcharge the winner when the bid spread is smaller, which is consistent with the qualitative predictions of the model.
5.3 Experimental design
While the predictions of the behavioral model are consistent with our experimental results, there are other possible forces at play. For example, if the seller has other-regarding preferences, then she would also choose an intermediate price between the highest and second-highest bids. In this section, we design a new experimental treatment to directly test the mechanism proposed in the behavioral model. In particular, we define a “no-rules” auction (NR) that is procedurally identical to the NCSP auction but that differs in framing. In both auctions, the seller has agency to determine the outcome of the auction (i.e., the winner and the price of the item). However, the experimental instructions vary across the two treatments. In the NCSP auction, both the rules of the auction and the seller’s strategy space are described to subjects. In the NR auction, the rules are omitted and only the seller’s strategy space is described to subjects.Footnote 21 Comparing sellers’ pricing behavior across the NR and NCSP auctions allows us to pin down whether sellers’ aversion to rule-breaking is the driving force behind our experimental results.
5.3.1 Implementation
The NR treatment was conducted at the Laboratory for Economic and Decision Research (LEDR) at the University of East Anglia. We recruited a total of 72 subjects across four sessions (with 18 subjects per session). Each session lasted approximately 60 min and the average subject payment was £19.54. The experiment was programmed and conducted with the z-Tree software (Fischbacher, Reference Fischbacher2007).
5.4 Experimental results
We first conduct a linear estimation of the bidding function in the NR auction (forcing the intercept to pass through zero). Ordering the estimated bidding functions, we find that

Several insights emerge from these comparisons. First, bidding behavior is significantly different between the NCSP and NR auctions. This suggests that bidders believe that sellers will behave differently in the absence of auction rules. Second, there is no significant difference in bidding behavior between the FP and NR auctions. This allows us to draw a further inference: in the absence of auction rules, bidders’ behavior is consistent with the belief that sellers will extract the maximum possible surplus.
We now compare the behavior of sellers between the NCSP and NR auctions. To do so, we estimate OLS regressions of both the overcharging ratio (
![]() ) and a dummy variable for overcharging (
) and a dummy variable for overcharging (
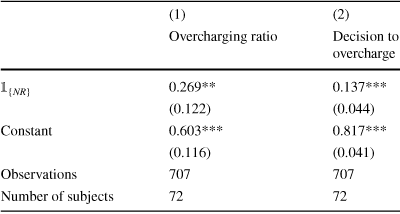
![]() ) on a treatment dummy variable for the NR auction. The results are shown in Table 6. We observe statistically significant differences in seller behavior on both the intensive and extensive margins. In particular, sellers in the NR auction extract 27 percentage points more of the available surplus and are 14 percentage points more likely to overcharge the winner than in the NCSP auction.
) on a treatment dummy variable for the NR auction. The results are shown in Table 6. We observe statistically significant differences in seller behavior on both the intensive and extensive margins. In particular, sellers in the NR auction extract 27 percentage points more of the available surplus and are 14 percentage points more likely to overcharge the winner than in the NCSP auction.
Clearly, from the perspectives of both sides of the market, the NCSP and NR auctions are distinct mechanisms. In the absence of auction rules, sellers’ pricing behavior is closer to the FP auction. Bidders, in turn, correctly anticipate this and behave as if they are participating in a FP auction. Overall, the NR treatment demonstrates that sellers’ aversion to rule-breaking plays a large role in explaining the results of the NCSP auction.
Table 6 OLS regressions of seller behavior in the NCSP and NR auctions. Standard errors are clustered at the subject level
|
(1) |
(2) |
|
|---|---|---|
|
Overcharging ratio |
Decision to overcharge |
|
|
|
0.269** |
0.137*** |
|
(0.122) |
(0.044) |
|
|
Constant |
0.603*** |
0.817*** |
|
(0.116) |
(0.041) |
|
|
Observations |
707 |
707 |
|
Number of subjects |
72 |
72 |
Significance levels are indicated as follows: **
![]() , ***
, ***
![]()
6 Conclusion
We report results from a series of laboratory experiments that compare behavior and outcomes across different auction formats that vary in their credibility. Our first main result is that, contrary to theory, the NCSP auction fails to converge to the FP auction. While sellers often break the rules of the NCSP auction, they typically do not maximize revenue. Consequently, bidders in the NCSP auction do not behave as though they are participating in a FP auction. We propose an alternative specification for sellers’ preferences that includes an aversion to rule-breaking. We show that this behavioral model generates predictions that are consistent with our experimental results. We then conduct an additional experimental treatment to test the underlying mechanism of the behavioral model. In support of the model, we find that aversion to rule-breaking is able to organize the experimental data.
Our results have important implications for market design. In particular, we have documented substantial heterogeneity in seller behavior in the NCSP auction. This novel dimension of strategic uncertainty increases the burden of participation for bidders, who must now form beliefs about the seller’s behavior in addition to considering the actions of other bidders. This is a powerful argument for the use of credible auctions in the field, since they may be widely perceived as safer or simpler for bidders than non-credible auctions.Footnote 22 In terms of practical advice, reforms that increase the transparency of auction institutions—such as requiring sellers to publicly disclose the highest and second-highest bids—could be helpful in mitigating bidders’ concerns. Indeed, Hakimov and Raghavan (Reference Hakimov and Raghavan2021) argue for the publication of priority score cutoffs to improve the verifiability of school choice mechanisms. They also provide empirical support for the effectiveness of their suggestions in a laboratory experiment.
Finally, our experiment abstracts from participation decisions by randomly assigning each subject to a single auction format. In real-life settings, bidders are likely to face a choice over auction formats and may exhibit a preference for credible auctions. We believe that studying credible and non-credible auctions with endogenous entry is a promising area for future experimental research.
Supplementary Information
The online version contains supplementary material available at https://doi.org/10.1007/s10683-023-09802-0.
Appendix: Proofs
Proof of Proposition 2
(i) This part follows trivially from the fact that sellers do not use dominated strategies.
(ii) Taking the first-order conditions for the seller, we have that
Given that
 ,
,
 , and
, and
 , there exists However, the seller would only choose
, there exists However, the seller would only choose
 if the utility under this decision is at least as large as the utility under
if the utility under this decision is at least as large as the utility under
 . That is, Simplifying the above expression, we can see that the inequality is satisfied if and only if
. That is, Simplifying the above expression, we can see that the inequality is satisfied if and only if Given our assumptions on
Given our assumptions on
 and the fact that
and the fact that
 , this guarantees that
, this guarantees that
 .
.
(iii) For this purpose, we need to calculate the expected price in the NCSP auction. The expected price can be expressed as follows:
where is the threshold value at which the seller stops overcharging the winner.
is the threshold value at which the seller stops overcharging the winner.
(
![]() ) Since
) Since
![]() , we have that
, we have that

At the same time, the revenue equivalence theorem implies that
Therefore,
which yields
(
![]() ) The revenue equivalence theorem implies that
) The revenue equivalence theorem implies that
![]() . That is,
. That is,
Since
![]() and
and
![]() is an increasing function, we have that
is an increasing function, we have that
Therefore,
Finally, if
![]() is sufficiently low, then
is sufficiently low, then
![]() and we are able to conclude that
and we are able to conclude that
![]()












