1. Introduction
Victor Hugo once wrote, ‘No army can withstand the strength of an idea whose time has come.’ In 2006, law professor Tim Wu put forward an idea about the trade regime and the internet. Stressing the internet is built on global data flows, he noted the global internet allows everyone to potentially become an importer or exporter of services and goods, and thus, ‘almost by accident, the WTO has put itself in an oversight position for most of the national laws and practices that regulate the Internet’ (Wu, Reference Wu2006: 263–264). Wu concluded that WTO members would have to decide how much control of the internet is legitimate domestic regulation and how much is a barrier to trade (Wu, Reference Wu2006: 287).
The WTO and other trade agreements say nothing about the internet or censoring (Burri, Reference Burri2013) and very little about human rights on or offline (Aaronson with Townes, Reference Aaronson and Townes2012). Nonetheless, Wu's idea gained traction. In 2007, Google asked the United States Trade Representative (USTR) to fight censorship as a trade barrier (Rugaber, Reference Rugaber2007). Google's Andrew McLaughlin noted, ‘We take seriously Google's mission ‘to organize the world's information and make it universally accessible and useful’, but government efforts to censor the internet makes that task much harder’ (McLaughlin, Reference McLaughlin2007).
Journalists, business associations, and scholars picked up on the notion that censorship, blocking, and redirection of internet traffic constituted a barrier to trade and new form of protectionism (Riley, Reference Riley2007; Biggs, Reference Biggs2007; Beaumont, Reference Beaumont2010; Calinoff, Reference Calinoff2010; Computer and Communications Industry Association, 2008; NFTC, 2010; Swedish Board of Trade, 2016; Gao, Reference Gao2011; Erixon and Lee-Makiyama, Reference Erixon and Lee-Makiyama2010, Chander, 2011). The United States explored challenging censorship. In 2011, USTR sent a letter to the Chinese Ministry of Commerce requesting information on the trade impact of Chinese policies that may block US companies’ websites in China (USTR, 2011). The Chinese government never responded, and the United States did not launch a trade dispute. Without clarity from a trade agreement or dispute, policymakers do not know if censorship is distorting trade in data.
Moreover, when governments have attempted to make rules to govern data flows, they have placed such language in e-commerce chapters, which the United States and EU have recently renamed ‘digital trade chapters’ (USTR, 2017b; European Commission, 2017c). But policymakers still do not agree on how to define digital trade. According to the Organisation for Economic Co-operation and Development (OECD), digital trade is all cross-border trade transactions that are either digitally ordered, facilitated, or delivered (OECD and IMF, 2017: 4). The United States defines digital trade as goods and services delivered via the internet and/or associated technologies (Fefer et al., Reference Fefer, Akhtar and Morrison2017). Hence, without shared norms and definitions, policymakers will struggle to develop rules to limit barriers to data flows.
Herein, I examine how policymakers (and others) talk about and define barriers to cross-border data flows. I use process tracing to examine how policies towards digital protectionism, particularly in the United States and the EU, have evolved over time. Scholars use process-tracing in social science to study causal mechanisms and to link causes with outcomes (Beach and Pederson, Reference Beach and Pedersen2013). Although individuals, firms and governments are quick to describe a policy as ‘protectionist’; these same individuals, firms, and governments have not found common ground on defining or regulating such practices.
Herein I will put forward a clear terminology. First, many analysts use ‘data’ and ‘information’ interchangeably, equating cross-border data flows with information flows. But they are not the same. I define data as unprocessed facts or details, whereas information is processed, organized, or structured data. Thus, information is a subset of data and in many trade agreements put forward by countries such as the US, EU, and Canada, they include language regarding such data flows in their e-commerce chapters. However, when describing barriers to data flows, scholars and policymakers often rely on ‘digital protectionism’ more than ‘data protectionism’.Footnote 1 They may recognize that the term data protectionism can easily be confused with personal data protection (regulations to protect individuals’ privacy online.) Yet digital protectionism is a broad term that refers to a wide range of barriers both to e-commerce and to cross-border data flows. In this article, I focus only on barriers to cross-border data flows.
I make five points:
1. Digital protectionism differs from traditional protectionism, because trade in data is different from trade in goods and other services. Data are intangible, highly tradeable, and some types of data, when processed, are a public good, which governments must provide and regulate effectively.
2. It will not be easy to set international rules to limit digital protectionism without a shared set of norms and definitions. We have not yet achieved those shared norms and definitions.
3. Many allegations of digital protectionism are concerns about different approaches to regulating the data flows that underpin the internet within national borders. Although the United States and the EU are trying to create shared rules, the two trade giants have also been the most vociferous in describing other countries’ approaches as ‘protectionist’.
4. China provides a good example of how the failure to achieve shared norms before achieving clear regulations may lead to trade disputes. China allegedly has used a wide range of cyber strategies, including DDoS attacks (bombarding a website with service requests), to censor data flows and impede online market access beyond its borders. But nations have not yet openly discussed whether such practices distort trade, although they clearly destabilize all or parts of the internet.
5. Digital protectionism can lead to unanticipated side effects, including reduced internet stability, generativity, and access to information (Hill, Reference Hill2014; Clark et al., Reference Clark, Faris, Morrison-Westphal, Noman, Tilton and Zittrain2017). Such actions could also disrupt communications, increase costs, and reduce data security. These effects will not just be felt in the nation that relies on such protectionism. When one or more governments censor the internet, it can reduce the platform's openness and stability (Bildt, Reference Bildt2012; Box, Reference Box2016). Additionally, digital protectionism may also undermine human rights and scientific progress. (Swedish Board of Trade, 2016: 52; OECD, 2016; Aaronson, Reference Aaronson2016a).
This article proceeds as follows. To begin with, I discuss the importance of data to economic growth and trade. Next, I define ‘protectionism’ and ‘digital protectionism’ and illuminate the relationship between digital protectionism, domestic regulations, and trade/market distortions. I then examine what trade agreements say about digital protectionism and explain why it is so difficult to develop shared rules without shared definitions and norms. I discuss what the United States and EU say about digital protectionism and show that their practices, at times, appear confusing and/or contradictory. I argue that as technologies and public opinion about privacy and security evolve, citizens will demand greater regulation (e.g. regulation of artificial intelligence, which is built on cross-border data flows). In so doing, I examine perceptions of what is legitimate regulation. Furthermore, I focus on Chinese digital protectionism and how it may distort trade not only in the home market but other countries as well, which is a challenge for trade policymakers. Finally, I provide policy recommendations.
2. The role of data in trade
Data and information have long been a key component of trade, but recently data have created new forms of trade. However, all forms of data-driven trade are not all the same. We define-e-commerce as sales of physical goods both among businesses and between businesses and consumers. Digital trade is a broader term that encompasses goods and services delivered via the internet and associated technologies (such as cloud computing services and voice-over-internet calls. Firms and individuals have built on cloud computing to create brand new online services such as apps, internet-connected devices (Internet of Things [IoT]), and services built on artificial intelligence (AI) such as personal assistants.Footnote 2
Data flows move across borders when individuals, companies, or governments authorize data to be transferred from one country (the source of data) to another country where the data may be processed (e.g. payroll) or used (e.g. to better counteract criminal patterns) (USITC, 2013, 2014; Nicholson and Noonan, Reference Nicholson and Noonan2014). Additionally, once the data have crossed from one country to another the source country may not control it.
Policymakers are just beginning to come up with ways to measure the impact of digital technologies upon trade (OECD and IMF, 2017: 15). In 2016, the McKinsey Global Institute estimated around 50% of the world's traded services were in digital form, while e-commerce accounted for approximately 12% of all goods traded across borders (Manyika et al., Reference Manyika, Lund, Bughin, Woetzel, Stamenov and Dhingra2016). The UN and OECD note the lack of shared definitions and ever-changing technologies make it difficult to effectively measure e-commerce, let alone digital trade (OECD, 2016, 2017; Barefoot et al., Reference Barefoot, Curtis, Joliff, Nicholson and Omohundro2018). Likewise, in 2017, the International Monetary Fund (IMF) and OECD observed:
the intangible nature of digitalized services has created strong fiscal incentives for their source (country of origin) to be located wherever that may be most advantageous, which poses new challenges for the way international trade and investment policy-making is made as well as how international trade … is measured. In addition, significant income streams can now be generated through data itself, the collection and dissemination of which is subject to myriad national laws, for example, governing privacy … Barriers to data flows can give rise to barriers to trade. (OECD and IMF, 2017: 3)
Researchers and policymakers cannot even agree on an appropriate taxonomy. The US government distinguishes among categories of transactional data flows based on the relationship between the sender and recipient and the type of transaction that connects them (Nicholson and Noonan, Reference Nicholson and Noonan2014). In contrast, the OECD focuses on three attributes: (1) whether data are digitally ordered, (2) whether data are a good, a service, or information, and (3) who is engaged in the transaction: businesses, consumers, or government (OECD, 2017). Ciuriak and Ptashkina (Reference Ciuriak and Ptashkina2018) suggest a third taxonomy based on delivery modes and the nature of the parties to the transactions. Sen and Aaronson take a more granular approach. Sen (Reference Sen2017) distinguishes among personal data, company data, business data, and social data, and refers to metadata as business and social data. Aaronson differentiates between personal data, public data, confidential business data, machine-to-machine data, and metadata (Aaronson and LeBlond, Reference Aaronson and LeBlond2018).
The types of data matter because most trade agreements include exceptions – where governments can breach their obligations to encourage trade flows to achieve legitimate policy objectives such as protecting privacy, national security, or public morals. Both Sen and Aaronson note that who controls the data and where the data are controlled should be key factors in any taxonomy or set of rules, because such aspects influence the benefits that firms and consumers can reap from trade and the purpose and purview of regulation designed to protect individuals’ personal data, security, and other non-trade objectives.
3. How might we define digital protectionism?
To best understand digital protectionism, we first need to understand the meaning of protectionism. According to Irwin (Reference Irwin1996), protectionism is both an ideology and a government act. Despite thousands of years of trade and two centuries spent writing hundreds of trade agreements designed to limit protectionism, it has no exact definition (Swedish Board of Trade, 2016: 5; McGee, Reference McGee1996).
In 1982, the Office of the Special Trade Representative (now, the USTR) drafted a primer on trade. It defined protectionism as ‘the setting of trade barriers high enough to discourage imports or to raise their prices sufficiently to enable relatively inefficient domestic producers to compete successfully with foreigners’ (Office of the Special Trade Representative, 1982: 149). In this view, policymakers use protectionist measures to reduce the supply and/or raise the cost of imported goods or services, at the behest of some of their citizens. Protectionism is about altering market conditions and distorting trade in ways that favour domestic producers over their foreign competitors. However, this definition is outdated, since protectionism in all countries depends on a wide range of factors including the state of the economy, the political clout of interest groups dependent on trade or protection, public awareness of trade, and the strength or weakness of protectionist ideas (Aaronson, Reference Aaronson2001: 11).
For centuries, policymakers have used trade agreements to establish the rule of law in trade by obligating signatories to forbid certain types of protectionist practices. But policymakers have also long recognized that policies that may appear protectionist may not have been designed to achieve trade-distorting effects. For this reason, trade agreements include ‘exceptions’, which allow governments to breach the rules to achieve other important policy goals. As an example, many governments adopt food safety regulations to protect consumers from harm, although these measures can distort trade. While these regulations may have a protectionist effect, they may lack protectionist intent (Swedish Board of Trade, 2016: 5). And unsurprisingly, individuals have alleged that governments have distorted trade in data since the early days of computer services (Aaronson, Reference Aaronson2017a; Drake et al., Reference Drake, Cerf and Kleinwächter2016) But in the past four years, the number and allegations of digital protectionism have increased dramatically (Cory, Reference Cory2018, Reference Cory2017; Bauer et al., Reference Bauer, Lee-Makiyama, van der Marel and Verschelde2014, Reference Bauer, Ferracane and van der Marel2016; Chander and Le, Reference Chander and Le2014; USITC, 2013, 2014; Froman, Reference Froman2017).
At first glance, digital protectionism may look like other forms of protectionism. Policymakers in country A might use border measures or domestic policies such as regulations or subsidies to favour domestic providers of data or alter market conditions in country A. But protectionism in services is different from protectionism in goods, as the object of regulation is the producer, rather than the product (Hindley, Reference Hindley1988).
Digital protectionism differs from traditional protectionism in five key ways.
• First, many services from payroll to data analytics rely on access to cross-border data flows. These data flows may yield a good, a service, or both (Ariu, Reference Ariu2012). The United States and OECD characterize downloaded films or music as a good (OECD, 2016; Barefoot et al., Reference Barefoot, Curtis, Joliff, Nicholson and Omohundro2018). In contrast with physical goods, netizens can trade that same digital good simultaneously. Moreover, trade in digital services differs from trade in other services because suppliers and consumers do not need to be in the same physical location for a transaction to occur. Given these attributes, it may be hard for researchers to ascertain exactly what a government wants to protect and whether a government is acting with protectionist intent.
• Second, trade in data is fluid and frequent, and location is hard to determine on the borderless network. Trade in the same set of data can occur repeatedly in nanoseconds (e.g. when millions of people download Beyoncé’s latest song). Researchers and policymakers may find it hard to determine what is an import or export. They also struggle to ascertain when data are subject to domestic law (such as IP law) and what type of trans-border enforcement is appropriate (Goldman, Reference Goldman2011; de la Chapelle and Fehlinger, Reference de la Chapelle and Fehlinger2016). Policymakers cannot easily determine jurisdiction, because data may travel through one server to another jurisdiction. Consequently, data flows may travel through several countries before these flows reach their destination (de la Chapelle and Fehlinger, Reference de la Chapelle and Fehlinger2016).
• Third, economists generally agree that many types of data are public goods, which governments should provide and regulate effectively. Furthermore, when states restrict the free flow of data, they reduce access to information, which in turn can diminish economic growth, productivity, and innovation domestically and globally (Maskus and Reichman, Reference Maskus and Reichman2004: 284–285; Khan, Reference Khan2009; OECD, 2016). They can also affect the functioning of the internet (Hill, Reference Hill2014: 32; Daigle, Reference Daigle2015; Clark et al., Reference Clark, Faris, Morrison-Westphal, Noman, Tilton and Zittrain2017). Hence, if officials restrict cross-border data flows, they may create many unintended consequences.
• Fourth, although trade in data occurs on a shared platform (the internet) held in common, firms, users, and governments do not all have the same responsibility for its stability. Corporations run much of the internet but they can't respond to, or see many of, the threats. Meanwhile, many companies are essentially data collecting and selling firms; they provide free services to netizens in return for the use of their personal data (e.g. Google search and Facebook's social network). In this model, individuals do not understand or recognize their responsibility for internet security and stability. Recognizing this ‘tragedy of the commons’, governments are individually developing regulations to protect the safety and security of their netizens (Davidow, Reference Davidow2012). Some of these policies may, without intent, distort trade in cross-border data flows. For example, some countries may feel it necessary to regulate the data flows that fuel artificial intelligence (AI), while others may want to regulate the use of AI to delineate what news their citizens see (Aaronson, Reference Aaronson2018; McAuley, Reference McAuley2018).
• Fifth, in contrast with their efforts to define legitimate regulation for e-commerce, there is no clear model that policymakers can use to distinguish between legitimate and trade-distorting data flow regulation. In a survey of its 194 members, UNCTAD found that some 77% of its members had e-transaction laws, 50% had consumer protection laws, 58% had privacy laws, and 72% had cybercrime laws to facilitate an appropriate enabling environment (UNCTAD, 2015). But policymakers have not yet figured out whether or how to regulate data analytics, AI, and other new technologies that rely heavily on personal data (Owen, Reference Owen2018). Governments are also trying to ascertain whether and how to contest the monopoly power of the big platforms and opacity of algorithms used by many platforms to bring us news, connect us to friends, and organize and improve our lives. Responding to this lack of clarity, the OECD called for greater efforts to find common ground on non-trade-distorting regulations designed to protect privacy and security. It pointed to the Sanitary and Phytosanitary Standards (SPS) and Technical Barriers to Trade (TBT) agreements at the WTO, which are designed to ensure that such measures should not represent disguised restrictions on trade nor be more trade-restrictive than necessary (Lopez Gonzalez et al., Reference Lopez Gonzalez, Messent, Rentzhog, Flaig, Jouanjean and Walkenhorst2016: 58). While threats to public or animal health (e.g. Severe Acute Respiratory Syndrome-SARS) can be global or affect many nations, threats to data security are more frequent then animal diseases or disputes about electrical standards. Moreover, domestic regulations that allow nations to censor or filter the internet or use DDoS attacks can affect not just market access in one or three countries, but the platform's stability (West, Reference West2017). Hence, these agreements may help to describe what is or is not legitimate regulation but are probably less useful in providing guidance as to the broader effects upon the internet.
4. The ever-expanding US definition of digital protectionism
The United States was likely the first government to define digital protectionism because digital trade is particularly important to the US economy. The US International Trade Commission (USITC) estimated that digital trade in certain digitally intensive industries resulted in a 3.4% to 4.8% increase in US GDP from 2011 to 2013, while online sales of products and services in ‘digitally intensive’ sectors were 6.3% of US GDP in 2012. USITC also asserted that the expansion of digital trade caused real wages to increase by 4.5% to 5% and boosted US aggregate employment by up to 1.8% while reducing average trade costs by 26% (USITC, 2014). This is not surprising, as the United States is home to 11 of the world's 15 largest internet businesses (Statista, Reference Statista2017).Footnote 3 The US Department of Commerce reported that digitally delivered services accounted for about half of all services trade and in 2016 the digital economy accounted for 6.5% of current dollar US GDP (Fefer et al., Reference Fefer, Akhtar and Morrison2017: 8; Barefoot et al., Reference Barefoot, Curtis, Joliff, Nicholson and Omohundro2018: 3).
The US definition of digital protectionism keeps growing, as the internet and associated services change over time. In 2013, at the behest of the US Senate Finance Committee, USITC sought to examine the extent of digital protectionism, which it defined as the erection of barriers or impediments to digital trade, including censorship, filtering, localization measures, and regulations to protect privacy (USITC, 2013). USITC also surveyed industry representatives and experts regarding what they considered major impediments to digital trade. These individuals ‘expressed concerns with respect to localization barriers, data privacy and protection, intellectual property-related issues, and online censorship,Footnote 4 as well as impediments to digitally enabled trade’ (USITC, 2013: xxi). In 2017, the Congressional Research Service, which provides policy and research information to the US Congress, issued a broader list. In the tables that follow, I use this list to examine how these measures may distort trade, how they affect markets, and whether they are covered under WTO rules. Table 1 provides an overview of policies the United States labels as protectionist and provides examples of countries that have adopted these policies.
Table 1. Listing of barriers to digital trade
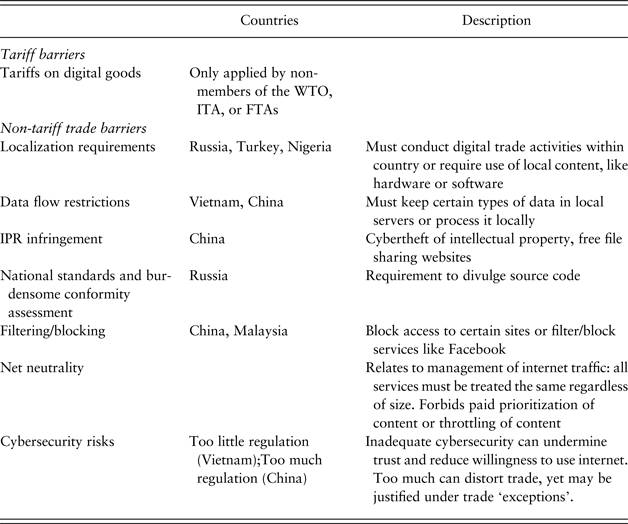
Sources: Fefer et al. (Reference Fefer, Akhtar and Morrison2017); US International Trade Commission (2013, 2014).
Table 2 below attempts to illuminate how these policies might affect markets. In column 1, I discuss market/trade effects as well as whether US experts and executives perceive that a measure is intended to distort trade. I rely on survey data collected by OECD (2016b) USITC (2013, 2014) about companies and their assessments of protectionist intent.
Table 2. How alleged barriers to digital trade might affect markets/protectionist intent
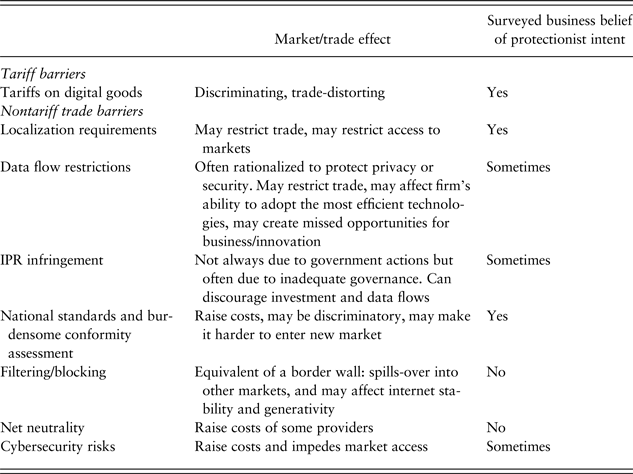
Sources: Fefer et al. (Reference Fefer, Akhtar and Morrison2017); USITC (2013, 2014); OECD (2015, 2016).
Table 3 uses the criteria of the SPS and TBT agreement to assess alleged barriers to cross-border data flows. It includes all the types mentioned in the other tables that the United States has described and new barriers such as regulations to prevent disinformation and DDoS attacks.
Table 3. SPS and TBT alleged barriers to cross-border data flows
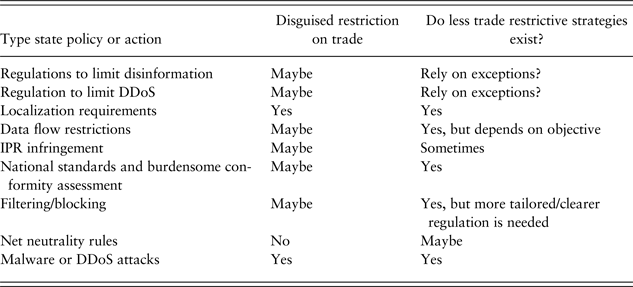
Sources: Fefer et al. (Reference Fefer, Akhtar and Morrison2017); USITC (2013, 2014); OECD (2015, 2016); World Trade Organization (2018).
The US government actively monitors digital protectionism. In 2014, US Congress asked USITC to dig deeper into the practices of major US trade partners. It found that 49 nations have adopted digital protectionist policies and justified these policies as necessary to protect privacy and cyber stability. In 2017, USTR found digital protectionism in many of its trade partners, including Indonesia, Russia, China, the EU, and Turkey (USTR, 2016b, 2017b).
The United States is not alone in finding digital protectionism. Canadian firms also allege that other countries are increasingly using digital protectionism, and they are calling for rules to regulate it (McKenna, Reference McKenna2013). A 2011 study by the Conference Board of Canada found Canada faced a multitude of digital trade barriers (Goldfarb, Reference Goldfarb2011). The EU is also concerned, because it is the world's largest exporter of digital services (WTO, 2016: 124, Table A47; Hamilton and Quinlan, Reference Hamilton and Quinlan2016). In a November 2016 speech, DG Trade Commissioner Malmström noted, ‘Restrictions on cross-border data flows inhibit trade of all kinds: digital and non-digital, products and services’ (Malmström, Reference Malmström2016). On 20 June 2017, a prominent EU Parliament member, Marietje Shaake, warned:
Governments around the world are drawing up barriers that hinder market access or create unfair advantages for domestic companies … These barriers also have negative impacts for people, whether it be higher costs, decreased access to products and content, violations of their human rights or uncertainty and distrust regarding the use or safety of certain products. If we believe the rule of law must prevail, then fair competition must be the goal in a hyper-connected world. There can be no place for digital protectionism. (Schaake, Reference Schaake2017)
In its 2015 and 2016 reports on global trade barriers, DG-Trade, the European Commission agency responsible for trade policy, reported that Russia and China were increasingly closed to digital trade. The EU criticized Russia's data localization requirements and complained that China justified protecting the internet sector as a matter of national security far beyond normal international practice (European Commission, 2015a: 6, 8). In its 2016 report, the Commission found that since 2008, some countries have adopted over 35 data protectionist measures, including localization requirements (European Commission, 2016: 8, 11). In its 2017 report, the EU only commented on China's digital protectionism and heavy internet regulation (European Commission, 2017a).
Many of the United States’ key trade partners do not agree with all aspects of the US definition or that specific policies are protectionist in effect or intent. For example, in 2015, members of the EU Parliament objected to the US government labelling EU policies, such as data protection laws, as ‘protectionist’ (Schaake, Reference Schaake2015). And as noted above, the Canadian government insists on cultural exceptions (which allows Canada to provide subsidies, quotas, and restrictive investment policies) to maintain Canadian culture in the face of US and European competition.
5. The need for a shared set of norms and definitions
The WTO is the best place to make rules to govern digital trade, because it covers 164 nations and is therefore global like the internet. But it is not the most up-to-date multilateral trade agreement. The WTO includes several agreements that cover issues affecting digital trade, such as: the Information Technology Agreement (ITA), which eliminates duties for trade in digital products; the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPs), which protects trade-related intellectual property pertinent to information technology; and the General Agreement on Trade in Services (GATS), which has chapters on financial services, telecommunications, and e-commerce that relate to cross-border data flows. These chapters predate the internet and associated technologies. Member states designed the GATS language to ensure it would remain relevant as technology changed, but several member states have said that they need clarification on specific points and want to update these rules to avoid misunderstanding. In 2011, the United States questioned whether WTO commitments for goods and services trade should govern digital trade and if they could cover the mobile internet and cloud computing (WTO, 2011). Academics and business leaders have also argued that the WTO's rules are incomplete, outdated, and in need of clarification (Burri, Reference Burri2013; Lee-Makiyama, Reference Lee-Makiyama2011). Since the Doha Round in 2001, WTO member states have tried to negotiate new rules to govern e-commerce and trade in computer or digital services through a new agreement called the Trade in Services Agreement (TiSA). But they have not yet found consensus (European Commission, 2018b; WTO, 2017).
According to the WTO Analytical Index,Footnote 5 the GATS e-commerce chapter sets rules governing how nations can trade electronically delivered services. The GATS has two sets of exceptions: the General Exceptions and the National Security Exception.Footnote 6 Under these exceptions, signatory nations can restrict trade in the interest of protecting public health, public morals, privacy, national security, or intellectual property, as long as such restrictions are necessary and proportionate and do not discriminate among WTO member states. The public order exception may be invoked only where a genuine and sufficiently serious threat is posed to one of the fundamental interests of society. Moreover, WTO dispute settlement bodies have found that ‘measures must be applied in a manner that does not to constitute arbitrary or unjustifiable discrimination or a disguised restriction on trade in services’. Finally, countries should ensure that they use these exceptions in a reasonable manner so as not to frustrate the rights that they have accorded to other members (Goldsmith and Wu, Reference Goldsmith and Wu2006). WTO does not have an exception to promote local culture. Table 4 shows whether practices that the United States has labelled ‘protectionist’ could be banned under existing WTO rules or viewed as practices allowed under the exceptions, if they are necessary and done in the least trade-distorting manner possible.
Table 4. Digital trade barriers and WTO rules

Sources: Fefer et al. (Reference Fefer, Akhtar and Morrison2017); USITC (2013, 2014).
Meanwhile, although the GATS states nothing explicitly about data flows, WTO members have begun to apply these obligations when settling disputes about cross-border data flows (Wunsch-Vincent, Reference Wunsch-Vincent2006; Goldsmith and Wu, Reference Goldsmith and Wu2006). The WTO Dispute Settlement Body has adjudicated two trade disputes related to data flows.Footnote 7 In the first dispute, after Antigua challenged the US ban on internet gambling, the WTO ruled that governments could restrict service exports to protect public morals if these barriers were necessary, proportionate, and non-discriminatory (i.e. not discriminating between foreign and domestic providers).Footnote 8 In the second dispute, the WTO Appellate Body examined China's restrictions on publications and audio-visual products, noting that commitments for distribution of audio-visual products must extend to the distribution of such products on the internet.Footnote 9 However, neither dispute provided clarity regarding key issues such as whether governments can, for example, restrict sales of offensive items such as Nazi memorabilia or censor and filter websites (Mattoo and Schuknecht, Reference Mattoo and Schuknecht2000: 19–20; Goldsmith and Wu, Reference Goldsmith and Wu2006). Until members challenge these policies in a trade dispute or negotiate new rules, we will not have clarity on why, how, or when governments can restrict cross-border data flows (Aaronson and Townes, Reference Aaronson and Townes2012).
Meanwhile, in the absence of progress in digital trade negotiations at the WTO, the United States, EU, Canada, and other nations have been actively pursuing FTAs both as a means of expanding trade in general and in setting rules to govern digital trade. Only two such free trade agreements (FTAs) – the Comprehensive and EU Mexico – include binding language on digital trade and limits on some types of digital protectionism. (USTR, 2016a; Aaronson, Reference Aaronson2016a).Footnote 10
Under US President Barack Obama (2008–2016), the United States and its 11 TPP partners spent years negotiating a binding and disputable e-commerce chapter in the Trans-Pacific Partnership (TPP) that requires signatories to facilitate cross-border data flows. These 12 countries also delineated clear exceptions and stated that, when nations sought to use them, they must be necessary and executed in the least trade-distorting manner. This first version of TPP (with the United States) contained transparency requirements that could bring much needed clarity, due process, and increased political participation in trade and internet-related policymaking in countries with authoritarian or secretive regimes (e.g. Vietnam or Malaysia). Finally, TPP built on a ‘carve-out’ first delineated in NAFTA (the North American Free Trade Agreement)Footnote 11 that allows the Canadian government to subsidize or otherwise favour Canadian content over US content as a way of preserving Canadian culture. ‘Cultural industries’, as defined by NAFTA Article 2107, include those involving the publication, distribution, or sale of publications or printed music; the production, distribution, sale or exhibition of film, video recordings, audio, or music video recordings; and radio communications, intended to reach the public. US companies want the United States to limit this carve-out when they renegotiate NAFTA (Fortnam, Reference Fortnam2017a).
The Obama administration wanted to create the rules and processes governing digital trade to ‘promote the digital economy through a free and open Internet’ (Obama, Reference Obama2015). As the talks progressed, US trade diplomats became increasingly concerned about digital protectionism, recognizing that it could threaten the dominance of US internet giants, which require relatively unrestricted access to operate and build new businesses like artificial intelligence (AI) and apps. Hence, TPP parties banned certain types of practices that could fragment the internet, reduce access to information, and/or increase the cost and difficulty of doing business online (Drake et al., Reference Drake, Cerf and Kleinwächter2016: 36; Aaronson, Reference Aaronson2016a). Given China's global influence as the second-largest economy and the country with the most internet users, Obama administration officials were also particularly concerned about China's efforts to enforce its concept of cyber-sovereignty, although other nations had introduced this concept in earlier debates about cross-border data flows.Footnote 12 Cyber-sovereignty, also known as information-sovereignty, can be defined as banning unwanted influences in a country's information space and shifting the governance of the internet from a multi-stakeholder forum to an international government body, such as the UN (Schia and Gjesvik, Reference Schia and Gjesvik2017; Burgman, Reference Burgman2016). From the US perspective, the TPP allowed the United States and its allies, rather than China, to set the rules regarding data flows (Froman, Reference Froman2017). However, in January 2017, in his first week in office, US President Donald Trump announced the United States’ formal withdrawal from TPP (Baker, Reference Baker2017). Hence, the United States, the leading demandeur of rules to govern digital trade and define and limit digital protectionism, gave up the only binding language regulating digital protectionism. The other 11 nations made some changes to the TPP, renamed it the CTPP, and signed it on 8 March 2018. It will take effect as soon as member states approve the agreement (Yaxley, Reference Yaxley2018).
Despite the Trump Administration ‘s criticism of CPTPP, the US government is using CPTPP as a foundation to renegotiate NAFTA. The United States aims to secure commitments not to impose customs duties on digital products and to ensure non-discriminatory treatment of digital products transmitted electronically; ‘establish rules to ensure that NAFTA countries do not impose measures that restrict cross-border data flows and do not require the use or installation of local computing facilities’; and ‘establish rules to prevent governments from mandating the disclosure of computer source code’. But in truth USTR is less ambitious for NAFTA. USTR has not included language in NAFTA that encourages countries to adopt a floor for rules protecting personal data; nor has it stated that signatories are not allowed to condition market access on the provision of source code as in CPTPP. However, in reflection of the rising import of artificial intelligence, the United States proposed that NAFTA add a ban on mandating disclosure of proprietary algorithms (Fortnam, Reference Fortnam2017a; Hoagland and Caporal, Reference Hoagland and Caporal2017; USTR, 2017b).
The EU has also not yet moved forward with binding provisions regarding digital protectionism. The EU and Japan drafted an e-commerce chapter which initially contained binding language regulating some aspects of digital protectionism, but instead of the chapter, the agreement includes a review clause that will allow the two sides to revisit the issue once the EU has a stated position (European Commission, 2017c; Fortnam, Reference Fortnam2017b and Reference Fortnam2017c). After deliberating for months, the EU announced its approach to digital trade and digital protectionism in February 2018. The strategy has personal data protection at its core. In its trade agreements (e.g. the renegotiated EU–Mexico Global Agreement), the EU will insist on three pillars: (1) a horizontal clause covering the free flow of both personal and non-personal data; (2) a ban on data and server localization requirements; and (3) language that safeguards the EU's right to regulate personal data, including language that the first two pillars cannot be subject to investor-state challenges or included in regulatory dialogues. In so doing, the EU made it clear that its vision of data protection cannot be challenged as a barrier to trade (European Commission, 2018a).
International organizations have tried to build greater understanding of the need to define and govern digital protectionism. In 2016, the OECD issued a report defining barriers to digital trade and their spillovers as well as a major study on the economic and social benefits of internet openness (OECD, 2016). In its 2016 World Development Report, Digital Dividends, the World Bank noted that, while many developing countries were beginning to take advantage of ‘the digital revolution’, they did not always have a policy or institutional environment for technology that enabled their citizens to benefit from digital technologies (World Bank, 2016). The UN Conference on Trade and Development (UNCTAD, 2015) has also tried to help countries put in place essential elements of an enabling environment and monitor national developments. In April 2017, the G-20 issued its priorities on digital trade noting the G-20 should
invite relevant International Organizations, within their respective mandates, to prepare a report … under the upcoming Argentinian G20 Presidency. This report could identify factors affecting Digital Trade readiness and propose options for reducing barriers to Digital Trade and improving the performance of developing and least developed countries in this area. (Federal Ministry for Economic Affairs and Energy, 2017)
But the G-20 ministers did not define barriers to digital trade.
In fact, we do not know if the practices that the United States and EU describe as protectionist distort trade. The United States and EU publish annual reports delineating these digital trade barriers based on business or association allegations, but we do not yet have accurate statistics to measure how such policies make it harder for US or EU firms to compete in foreign markets. The Centre for Economic Policy Research's Global Trade Alert Footnote 13 lists allegations of protectionist trade barriers, but it does not assess whether the allegations are correct or if these strategies distort trade. The European Centre for International Political Economy (ECIPE, 2018), a Brussels-based think tank, also publishes a list of barriers to digital trade and will shortly publish an index, the Digital Trade Restrictiveness Index (DTRI), that measures how countries in the world restrict digital trade. The DTRI is based on a wide spectrum of digital trade policies covering more than 100 policy measures across 64 countries worldwide. The index will be the first global initiative to provide transparency of applied digital trade restrictions and sheds light on how countries compare with each other (ECIPE, 2018). The OECD publishes the Services Trade Restrictiveness Index, which measures the trade restrictiveness of sector-specific policies such as telecommunications and computer services. The OECD is also attempting to consolidate these measures into one complete index of barriers to digital trade. Meanwhile, scholars are only just beginning to examine if measures such as those described by the United States truly distort trade (Chander and Le, Reference Chander and Le2014, Reference Chander2015; Berry and Reisman, Reference Berry and Reisman2012). Until scholars and governments find common ground on defining and measuring digital trade, we are simply listing and describing these alleged protectionist measures.
6. US and EU perspectives on what is legitimate regulation vs. trade-distorting
The United States and EU are the most vociferous in alleging digital protection. Yet, so far, the United States and EU have only been able to get their counterparts to agree to limit three protectionist measures: taxes on digital flows, data localization, and forced technology transfers (USTR, 2016a).
While both the United States and the EU condemn digital protectionism, both trade giants have policies and practices that they would target and label as trade-distorting were these policies and practices adopted by other countries. In fact, the government of Japan, which in July 2017 announced completion of its FTA with the EU, suggested the EU develop and clarify its position on the relationship between data protection and digital protectionism (Fortnam, Reference Fortnam2017c).
Censorship: Censorship allows countries to determine what data will be available within their borders and control internal dissent (Chander and Le, Reference Chander and Le2014: 1, 47–49). When governments censor and filter the internet, and ignore their citizens’ privacy rights, people may become more reluctant to engage in free speech, participate in politics, or search for information, because such activities could make them targets of government monitoring. The US Constitution sets limits on how and when individuals can censor free speech. However, various civil society groups and analysts allege that the United States allows internet service providers (ISPs) to make unfair, opaque decisions about site takedowns, often to protect online copyrights holders. These critics see such takedowns as a form of censorship. Meanwhile, in the wake of the spread of misinformation across social media platforms, a growing number of platforms practice self-censorship (Onlinecensorship.org; Chan et al., Reference Chan, Dao, Hou, Jin and Tuong2011; Epstein, Reference Epstein2016; Hulcoop et al., Reference Hulcoop, Scott-Railton, Tanchak, Brooks and Deibert2017). In addition, US policymakers may be under increasing pressure to limit access to some information posted online. In the wake of fake news and revelations that Americans who get their news from online platforms such as Facebook may have been manipulated algorithms, bots, and disinformation, there is growing pressure in the United States to regulate disinformation (Tufekci, Reference Tufekci2018; West, Reference West2017). Republican and Democratic congressmen are pressuring internet platforms such as Google, Facebook, and Twitter to do more to fight false information and stop foreign infiltration. To some observers, however, this response smells of censorship (Kravets, Reference Kravets2017; Myers and Wee, Reference Myers and Wee2017).
The US government routinely condemns censorship as a barrier to trade, although it has never challenged such behaviour in a trade dispute. However, in 2016, the United States cited China's Great Firewall as a trade barrier, which could mean that the United States is gathering evidence to challenge broad censorship (USTR, 2016b). In 2018, the United States asked the WTO services council to discuss China's cybersecurity rules as a barrier to the free flow of data (WTO, 2018).
The EU also criticizes censorship (including the Great Firewall) as a barrier to trade. Yet the EU provides its citizens with a right to request delinking of sites – the ‘right to be forgotten’. If an individual asks to be forgotten and an ISP approves the request, the information will remain online at the original site but will no longer appear under certain search engine queries. Some ISPs may interpret such requests as onerous and trade-distorting, while some human rights activists believe that delinking undermines the public's access to information (Manjoo, Reference Manjoo2015; Toobin, Reference Toobin2014).
Governments increasingly require internet firms to take down site content internet-wide that may be breach local intellectual property rules. Some observers consider such takedown requirements a form of censorship that can distort trade, especially when a government's court requires that the decision be enforced internet-wide, as occurred in a Canadian court case. In June 2017, in Google Inc. v. Equustek Solutions Inc,Footnote 14 a majority of the Supreme Court of Canada upheld a worldwide interlocutory injunction that required Google to globally de-index the webpages of a defendant in a separate intellectual property infringement proceeding. In 2016, French Data Protection Authority (CNIL) declared that search engines implementing France's Right to Be Forgotten law must de-list such links globally and not simply take down such sites within the EU (Reventlo: Reference Reventlow2017). On 19 July 2017, France's highest administrative court, the Conseil d'Etat (in English, the Council of State) referred the dispute between CNIL and Google, over the legality of applying the right to be de-indexed globally, to the Court of Justice of the European Union (CJEU). A Paris-based NGO, Internet and Jurisdiction, closely monitors such cases noting that the number and impact of such cases increasingly distort cross-border data flows (Internet and Jurisdiction, 2017). If other countries mandate similar decisions regarding site takedowns, firms such as Google would struggle to comply with potentially conflicting laws and international jurisdictional conflicts (Mackey et al., Reference Mackey, McSherry and Ranieri2017; Geist, Reference Geist2017).
Privacy and data protection: The right to privacy is an internationally accepted human right under the Universal Declaration of Human Rights. But the United States has adopted an inconsistent approach to privacy as a barrier to trade, as it considers privacy both a human right and consumer right. In 2013, USTR argued that Canada's British Columbia and Nova Scotia provinces have privacy laws that discriminate against US suppliers, because they require that personal data be stored and accessed only in Canada (USTR, 2014). In 2014, the United States also complained about Japan's uneven and Vietnam's unclear approaches to privacy and argued that China's failure to enforce its privacy laws stifled e-commerce (USTR, 2014: 96, 216). Thus, the United Sates simultaneously criticizes foreign governments for failing to develop clear or adequate approaches to enforcing privacy and categorises privacy as a trade barrier. Moreover, the US government has argued that privacy protections bolster trust in the internet and are essential to stimulating the growth of digital technologies. Although the United States has worked with other governments to establish principles on privacy, it has done little to foster bridges among these various privacy principles. As a result, we do not have a shared understanding of whether privacy regulations distort trade or are legitimate regulations designed to protect human rights (which would therefore be allowed under GATS and/or FTA exceptions).
The EU's approach to data protection also presents some inconsistencies. The 27 EU member states are working to create a digital single market (DSM) where data can flow freely among them and data will be regulated under one set of EU-wide rules. The main characteristic of the EU DSM is its high commitment to protecting personal data within EU. However, as noted above, the EU's approach to privacy will not be included in EU trade agreements as a topic for negotiation. EU Trade Commissioner Cecilia Malmström argued that personal data protection is not protectionist, stating:
Let's not kid ourselves: some data restrictions out there are purely protectionist. Rules that require data to be localized in a place, or that impose limits on transferring data; often have no justification, other than to inhibit market access by overseas companies. That is not data protection, it is protectionism; that is our trade partners not playing fair. And that is a legitimate topic for trade deals. (Malmström, Reference Malmström2016)
The first iteration of the EU's commitment to online data protection was the 1998 Directive on Data Protection. It prohibits the transfer of personal data to non-EU countries that do not meet the ‘adequacy’ standard for privacy protection. To become adequate, the EU requires other countries to create independent government data protection agencies, register databases with those agencies, and, in some instances, obtain prior approval from the European Commission before personal data processing may begin (Institute for Government (UK), 2017). Hence, while the EU does not require other nations adhere to its approach, it is attempting to export its norms.
As new technologies emerged, in the EU, policymakers and the public realized their data protection framework needed updating. In 2016, the EU adopted the General Data Protection Regulation (GDPR), which replaces the Data Protection Directive. The GDPR takes effect on 25 May 2018 and provides rules on the use of data that can be attributed to a person or persons (EU Council Regulation, 2016/679).Footnote 15 In October 2017, the European Commission also proposed a new regulation ‘concerning the respect for private life and the protection of personal data in electronic communications’ to replace the outdated e-Privacy Directive, while ensuring its consistency with the GDPR (European Commission, 2017b).
However, some see the EU's stringent approach to data protection as a form of censorship by regulating what other netizens can and cannot see (Solon, Reference Solon2014; Hern, Reference Hern2014). As noted above, EU citizens have the right to demand delisting of data that breaches privacy. But this right to delist is only available on the internet within the EU.Footnote 16 Google, as example, will use geo-location to ensure residents located in each EU country cannot see the search results on any version of its platform, even as those outside the country can see them (Fleischer, Reference Fleischer2016; Pickrell, Reference Pickrell2017).
The EU's commitment to data protection has costs and benefits. On the one hand, the EU approach to elevating data protection is attractive to many countries and netizens, but, on the other hand, it is extremely costly to digital firms. Despite these costs and benefits, the EU increasingly encourages its trade partners to accept its approach to data protection. In 2017, a French court required that websites outside of France must block foreign content to enforce the EU's ‘right to be forgotten’. In so doing, the EU is imposing its values on other suppliers and consumers of data (Atkinson, Reference Atkinson2017). Because the EU is a major market, several countries are adopting EU data protection policies or working towards being deemed ‘adequate’. To date, on its website, the European Commission has recognized Andorra, Argentina, Canada, Faroe Islands, Guernsey, Israel, Isle of Man, Jersey, New Zealand, Switzerland, Uruguay, and the United States (limited to the Privacy Shield framework) as providing adequate protection, while Japan and South Korea are in discussions with the EU.Footnote 17
The EU has also introduced a new approach to regulating the use of algorithms, designed to protect the privacy of users and empower them to contest misuse. After 25 May 2018, the GDPR's Article 21 gives anyone the right to opt out of algorithm-tailored advertisements (e.g. what one finds when searching on Google). Article 22 allows EU citizens to contest legal or significant decisions made by algorithms and appeal for human intervention. In contrast, the United States is using its trade agreements to prevent such transparency, although it is unclear whether its NAFTA partners (and other nations) will agree to this language.
Cybertheft: The US government argues that companies as well as government entities are victims of cybertheft. According to the US Defence Science Board (2013), other nations use the internet to scour, penetrate, and steal data on critical technologies, including drones, robotics, communications, and surveillance technologies. The US government is increasingly concerned about China, noting that hackers working for the Chinese government or, with the government's support and encouragement, have infiltrated computer networks of US agencies and companies and stolen trade secrets. Once they have obtained these secrets, these hackers allegedly provided that data to Chinese companies. In 2015, the US China Security and Economic Commission reported that data were stolen from US government agencies, including the United States Postal Service (USPS), universities such as Penn State University, Johns Hopkins University, Carnegie Mellon University, and Massachusetts Institute of Technology, and companies such as United Airlines. All the cyberthefts are attributed to Chinese actors that appear to be aligned with the Chinese government; but this allegation is difficult to prove (USCC, 2015, 192, 198, 199–204). In 2015, China agreed with the United States that neither country's government will conduct cyber-enabled theft of intellectual property, although again cybertheft was not clearly defined (USCC, 2015, 209). Meanwhile, the US government has stressed it does not use surveillance for commercial theft. Nonetheless, in the summer of 2015, WikiLeaks provided evidence that the US government had spied on Japanese companies and policymakers to obtain prior knowledge of positions related to trade negotiations, President Obama called Japanese Prime Minister Abe to apologize. Also, in 2015, Chancellor Angela Merkel's office said it found that the US government had used Germany's top spy agency to watch European corporate targets. However, the US government still insists that it is not stealing corporate property and giving it to US companies. Thus, citizens and government officials in the United States and abroad may find it hard to distinguish between cyber monitoring to prevent crime and terrorism and cyber probing to steal technologies (Aaronson, Reference Aaronson2016a).
Regulatory Context: The United States argues that governments which fail to make an appropriate regulatory context for the free flow of data are effectively distorting trade. In 2015, it chided China, South Africa, Thailand, and the United Arab Emirates (UAE) for unclear internet rules. It criticized South Africa for failing to effectively enforce its laws online, named Vietnam and Turkey for overreaching bans on internet content, and condemned France for its proposals to tax internet activity (USTR, 2015). Meanwhile, the Trump administration has taken some steps that reduce US credibility as an advocate for the free flow of data across borders. US regulators have rejected the net neutrality principle, whereby individuals should be free to access all content and applications equally, regardless of the source and without ISPs discriminating against specific online services or websites. In 2015, the Federal Communications Commission (FCC) decided that several internet firms were dominating the market and jeopardizing access and fair pricing. The FCC agreed to regulate broadband and mobile ISPs as a utility to ensure that these providers did not achieve monopoly prices in markets where competition was limited. These rules, they argued, would promote net neutrality (Public Knowledge).Footnote 18 However, the new FCC Chair reversed that decision, stating that in so doing the United States was taking a hands-off approach to regulating the internet within its borders. Critics have contended, however, that this new approach allows US ISPs to discriminate among services, service providers, and websites (Borchers, Reference Borchers2017).
EU member states have several policies that could be considered trade-distorting. For example, EU member states have different approaches to ‘cultural protection’. Some EU members such as France have cultural exceptions (e.g. percentage of cultural goods and services that must be locally produced and broadcast), while others do not. (Blaney, Reference Blaney2015).
Cybersecurity regulations demonstrate the importance of finding common ground on the relationship between domestic regulation and cross-border data flows. Given the rise in malware, hacking, and disinformation, governments may at times seek to restrict cross-border flows to maintain political stability, trust, and personal security (Zetter, Reference Zetter2016; Poulsen, Reference Poulsen2017; Valeriano, Reference Valeriano2016; Hulcoop et al., Reference Hulcoop, Scott-Railton, Tanchak, Brooks and Deibert2017; Scott, Reference Scott2017; Mozur and Scott, Reference Mozur and Scott2016). In June 2017, WTO members debated if cybersecurity strategies could distort trade. Some members were concerned that cybersecurity regulations would negatively impact trade in information technology products, potentially discriminating against foreign companies and possibly leading to unnecessary disclosure of commercially confidential and technical data. Others argued that cybersecurity rules are needed to address national security issues and ensure consumer privacy, and that the measures in question are non-discriminatory (WTO, 2017a). In looking at the debate between China's cybersecurity regulations and US insistence that these regulations are protectionist, Director of Cato Institute's Herbert A. Stiefel Center for Trade Policy Studies Dan Ikenson concluded that the objectives of both governments have less to do with cybersecurity than with protectionism (Ikenson, Reference Ikenson2017). However, others may not believe it is so easy to ascertain protectionist intent.
7. China's censorship at home and abroad: new tactics and market access consequences
China's approach to regulating censorship both within and beyond its borders provides a good example of the difficulty in determining if a measure undermines market access (Krebs, Reference Krebs2016; Schneier, Reference Schneier2016). If censorship is a barrier to cross-border data flows, China has learned how to censor the internet beyond its borders. As noted above, China is one of the world's largest and fastest-growing internet markets. In 2016, only some 50% of its citizens were online, so the internet in China has plenty of room for growth (UNESCO, 2016). As a result, many firms believe they must have an online presence in China. However, the Chinese internet is also likely the world's most restrictive and monitored platform. The Open Net Initiative, a collaborative project that monitors internet censorship using both qualitative and quantitative analysis, claims that China operates ‘the most extensive, technologically sophisticated and broad-reaching system of internet filtering in the world’ (US–China Economic and Security Review Commission, 2008a: 3). The government blocks sites by internet protocol (IP) address, and blocks and filters uniform research locators (URLs) and search engine results. The country supposedly employs two million individuals to censor the internet. In 2017, Chinese officials argued that the nation must restrict the web to maintain social stability and security amid threats like terrorism (Xu and Albert, Reference Xu and Albert2017). However, China has different censorship systems for foreign and domestic sites (Erixon et al., Reference Erixon, Hindley and Lee-Makiyama2009). Most Chinese netizens cannot access websites such as Facebook and Twitter, foreign media such as the New York Times, and many Google services. In 2017, the American Chamber of Commerce in China reported that 79% of US companies in China have experienced blocked access to web tools and services, which raise their business costs (Associated Press, 2017). In addition, Chinese censorship rules lead firms to self-censor and can hobble user privacy and security (USCC, 2015: 211).
Unsurprisingly, USTR (2015: 70–72, 77–79) describes China's internet regulatory regime as restrictive and opaque. Legal scholar Henry Gao describes it as arbitrary and often unreasonable (Gao, Reference Gao2011: 371). Greatfire.org, a website monitoring Chinese censorship, found China censored 878 of 1233 Wikipedia pages and 769 of 947 Google pages.Footnote 19 Under WTO rules, China is supposed to provide a system of judicial or administrative review of such blockage, but it has not yet done so (Schruers, Reference Schruers2015; US–China Economic and Security Review Commission, 2008b).
China's approach to censorship is evolving. The government does not only rely on paid censors but also on the acquiescence of companies providing internet services within China. These companies must follow local law or withdraw from the market (e.g. Amazon, which provides cloud services to customers based in China). In July 2017, Amazon's partner in China told its customers that that VPN software (software that provides a virtual private network with which individuals in China can jump over the Great Firewall) is now banned. That same month, Apple removed several apps from its Apple store in China that allow individuals to use VPNs (Mozur, Reference Mozur2017). Furthermore, on 3 August 2017, all internet data centres and cloud companies located in China were ordered to participate in a three-hour drill to hone their ‘emergency response’ skills. They were essentially ordered to practice taking down websites that had been deemed harmful (Jiang, Reference Jiang2017). With these steps, China has made it almost impossible to get around the Great Firewall.
Since 2008, researchers have found evidence that the Chinese government has exported censorship beyond its borders. In a testimony before the US China Economic and Security Review Commission, Ron Deibert, the Director of The Citizen Lab at the University of Toronto, asserted that China used distributed denial of service (DDoS) attacks in Tibet, the United States, United Kingdom, Canada, and elsewhere since 2008. He noted that these methods deny access to information by disabling the sources of data (rather than blocking requests for data as filtering systems do). Researchers find it hard to pinpoint the source of such attacks, so governments can deny ever using such methods (US–China Economic and Security Review Commission, 2008a, 4). Moreover, with DDoS, China can censor abroad without asserting the heavy hand of government.
In 2015, researchers at The Citizen Lab and several other organizations asserted that hackers in China essentially took down two US-based websites: GitHub and GreatFire (Marczak et al., Reference Marczak, Weaver, Dalek, Ensafi, Fifield, McKune, Rey, Scott-Railton, Deibert and Paxxson2015).Footnote 20 GitHub is an open source site, which manages and stores revisions of projects using code and serves as a platform for online collaboration. GitHub hosts GreatFire.org (which monitors the Great Firewall) and the New York Times Chinese edition. In examining the attack, The Citizen Lab alleged the Chinese government used a ‘Great Cannon’ to harness internet traffic headed to China's most popular search engine Baidu and redirect it to flood these two overseas websites. The ‘Great Cannon’ cannot only shut down the connection, but apparently the hackers hijacked traffic to these web addresses and replaced benign unencrypted web content with malicious content (US China Economic and Security Review Commission, 2016: 200–201; Perlroth, Reference Perlroth2015). The researchers noted that the attacker targeted services designed to circumvent Chinese censorship. Meanwhile, Baidu denied that their servers were compromised, although the Citizen lab analysts could prove that the hackers had injected malicious JavaScript into Baidu connections (Marczak et al., Reference Marczak, Weaver, Dalek, Ensafi, Fifield, McKune, Rey, Scott-Railton, Deibert and Paxxson2015: 1, 8–9). Hence, a Chinese company, Baidu, was hijacked and victimized as part of the attack.
However, China is not the only country to use a DDoS attack to disable a website. Both the United States and the United Kingdom have allegedly tampered with internet traffic to launch attacks (Marczak et al., Reference Marczak, Weaver, Dalek, Ensafi, Fifield, McKune, Rey, Scott-Railton, Deibert and Paxxson2015). However, neither country did so to censor information. The Citizen Lab's researchers concluded that deployment of the ‘Great Cannon’ was a significant escalation in state-level data control because censorship was enforced by ‘weaponizing users’, rather than by direct government action. Moreover, China's alleged tactics create a dangerous precedent, contrary to international norms. Scholars are puzzled as to why China has chosen to act in this way (Marczak et al., Reference Marczak, Weaver, Dalek, Ensafi, Fifield, McKune, Rey, Scott-Railton, Deibert and Paxxson2015). In 2015, the South China Morning Post (2015) reported that the Chinese government had been planning the attack for over a year.
While several research organizations pinned the GitHub attack on China, we do not know who is behind the rise in DDoS attacks in the United States. Moreover, while the attacks may have come from Chinese entities that may be affiliated with the Chinese government, it is impossible to prove that the Chinese government ordered these attacks. Although several private firms and organizations have attributed these attacks to actors in China, they can't prove that China is behind these actions. Nor can we assert that China is the only country behind the increase in these DDoS attacks (Schneier, Reference Schneier2016; US–China Economic and Security Review Commission, 2016: Chapter 4; Kawanmoto, Reference Kawanmoto2017).Footnote 21 At year end 2017, the US Department of Justice determined that Dyn was not attacked by China, but by criminal elements.Footnote 22
According to William Marczak, a senior research fellow at The Citizen Lab, China has not used this tactic since 2015.Footnote 23 Yet the allegations of DDoS by Chinese-affiliated entities in the United States and United Kingdom have important implications for trade and trust in the internet. These DDoS attacks can reduce market access conditions in the attacked company's home country, since an attacked company (e.g. Twitter) cannot serve its customers if its site is unavailable. These attacks reduce market access and raise costs for firms who must hire researchers to ascertain who is responsible for these attacks while simultaneously spending money to get their sites back online. DDoS attacks also reduce internet stability and diminish the predictability of data flows (Google, 2010; Gao, Reference Gao2011; US–China Economic and Security Review Commission, 2008b). To put it differently, these tactics essentially export Chinese censorship to the United States and other countries and undermine the functioning of the internet. Yet the WTO is just beginning to examine how the Great Firewall and other Chinese policies may affect cross-border data flows (WTO, 2018).
8. The costs of digital protectionism: direct costs and unanticipated spillovers
Digital protectionism may be self-defeating. As noted above, while there is no consensus regarding how to define, measure, let alone remedy, digital protectionism, a growing number of researchers find costly spillover effects (USITC, 2013, 2014; OECD, 2017). ECIPE estimated that data localization regulations cost EU citizens about $193 billion per year, in part due to higher domestic prices (Bauer et al., Reference Bauer, Lee-Makiyama, van der Marel and Verschelde2014). However, the costs of digital protectionism are not always economic. They can also affect the stability of the internet as a whole (Bildt, Reference Bildt2012). In 2011, the OECD reported that Egypt's shutdown of the internet for five days led to ‘direct costs of at minimum USD 90 million’ (OECD, 2011). A 2016 Brookings study estimated the economic impact of internet censorship, filtering, and blocking was $2.4 billion, which was noted as an understatement of the actual economic damage of lost tax revenues, the negative impact of worker productivity, among other costs (West, Reference West2016). The OECD's Sarah Box argues that such reductions on internet openness can affect global value chains and reduce technology diffusion, thereby undermining development and trade (Box, Reference Box2016: 2). Governments that adopt digital protectionist strategies could hurt their own consumers and place their firms at a competitive disadvantage since such measures may increase costs to business (Elms, Reference Elms2017; Cory, Reference Cory2017). Digital protectionism may not only increase costs to firms, but legal disputes could escalate while individuals and firms could have fewer incentives to innovate (Hill and Noyes, Reference Hill and Noyes2018; de la Chapelle and Fehlinger, Reference de la Chapelle and Fehlinger2016). In short, digital protectionist strategies can backfire.
Analysts recognize that there is no easy way to measure internet openness or closure, or the effects of digital protectionism upon the internet. Nevertheless, they agree that ‘the dynamism of the internet depends in large part upon its openness’ and that variants of protectionism, like censorship or data localization, can reduce that openness (Bildt, Reference Bildt2012; Box, Reference Box2016; OECD, 2016). As an example, some Chinese officials admit that the Great Firewall is not only costly to maintain (with staff and constant vigilance), but also that it may deter foreign investment and innovation. On 4 March 2017, Luo Fuhe, the vice-chairman of the Chinese People's Political Consultative Conference, the top advisory body to China's parliament, stated that China's sprawling internet censorship regime is harming the country's economic and scientific progress and discouraging foreign investment. Fuhe and a few other Chinese leaders acknowledged the Great Firewall may make it harder for China to become an innovation-driven economy (Gao, 2017; Chu, Reference Chu2017; Haas, Reference Haas2017).
Some scholars also assert that digital protectionism undermines internet stability and interoperability. Data localization policies, filtering, or censorship can alter the architecture of the internet, which has long favoured technical efficiency over state politics. When officials place limitations on which firms can participate in the network, they may reduce the overall size of the network and once again potentially raise costs (Hill, Reference Hill2014: 32; Daigle, Reference Daigle2015; Drake et al., Reference Drake, Cerf and Kleinwächter2016). Finally, digital protectionism can undermine access to information, reducing innovation and the ability of citizens to monitor and hold their governments to account (OECD, 2016; Aaronson, Reference Aaronson2016a, Reference Aaronson2016b).
9. Conclusion: the need for common ground
The idea of using trade agreements to regulate digital protectionism may well be the idea whose time has arrived. Digital protectionism is both increasingly visible and contested. Trade policymakers are struggling to define it, develop shared norms, and regulate it. For example, some corporate officials consider EU efforts to establish the Digital Single Market as an EU-wide approach to protectionism. On 13 September 2016 in a New York Times article, Mark Scott noted, ‘The latest digital reforms – either on purpose or by coincidence, depending on people's viewpoints – take aim at that dominance, and potentially give European publishers and telecom companies a helping hand to compete head-on with their American rivals.’.In contrast, Nicky Stewart, a former internet strategist for the UK Cabinet asserted the EU was simply trying to develop rules that conformed to EU values (Stewart, Reference Stewart2017).
Digital protectionism has some commonalities with traditional protectionist objectives and strategies. Government officials have a wide range of legitimate reasons for why they may seek to limit cross-border data flows. For example, many of them want to develop an indigenous tech sector, requiring them to develop an effective enabling environment that includes competition, digital literacy, and infrastructure policies. In this pursuit, officials might sometimes take steps that discriminate against foreign market actors and, in so doing, distort trade, even though it may not be their original intent. Policymakers also want to encourage the rule of law online and prevent unlawful behaviour, such as the dissemination of hate speech or child pornography, fraud, identity theft, cyberattacks, and money laundering. These policies, too, may be necessary to achieve important domestic objectives, yet they may discriminate against foreign firms (Aaronson, Reference Aaronson2016b). Finally, what may appear protectionist to one country could be seen as legitimate and necessary regulation in another country (Financial Times, 2018).
Digital protectionism also differs from traditional protectionism because data are both a good and service and, at times, a public good. But some policymakers who seek protectionism are developing new tactics to protect such data beyond tariffs, quotas, and exchanged controls. China's alleged efforts to use DDoS attacks to censor global websites also seems to make it harder and more expensive for firms to access their home (and other) markets. Although these attacks are increasingly visible and numerous, trade officials have yet to openly discuss their implications for market access and rules-based trade.
Countries need to find common ground regarding which practices truly distort digital trade, what should be banned, and what should be limited and clarified under the exceptions. Hence, in developing norms and rules, decision-makers must first define how and when governments can control data and limit their flows. They must ensure that these rules are internationally accepted and transparent to ensure predictability and accountability. With shared understanding, the internet would be less likely to fragment, more people would have greater access to information, and individuals could create and share more data (Tietje, Reference Tietje2011).
To address these issues, policymakers must work multilaterally. Specifically, policymakers should ask the WTO Secretariat to:
1. Examine whether domestic policies that restrict data (short of exceptions for national security, privacy, and public morals) constitute barriers to cross-border data flows that could be challenged in a trade dispute.
2. Convene a study group to examine the trade implications of malware and DDoS attacks as a means of distorting trade. These tactics should be banned, although the WTO may not be the best forum to discuss these problems.
3. Monitor each other's digital trade practices during the WTO trade policy review process.
4. Policymakers should rethink how we regulate data internationally in trade agreements. A forward-looking approach would distinguish among the five types of data, who controls the data, and where the data are controlled (see Figure 1) (Aaronson, Reference Aaronson2017b). Control of data is important to any taxonomy or set of rules, because it influences the benefits that firms and consumers can gain from trade and it can build trust online (Aaronson and LeBlond, Reference Aaronson and LeBlond2018).
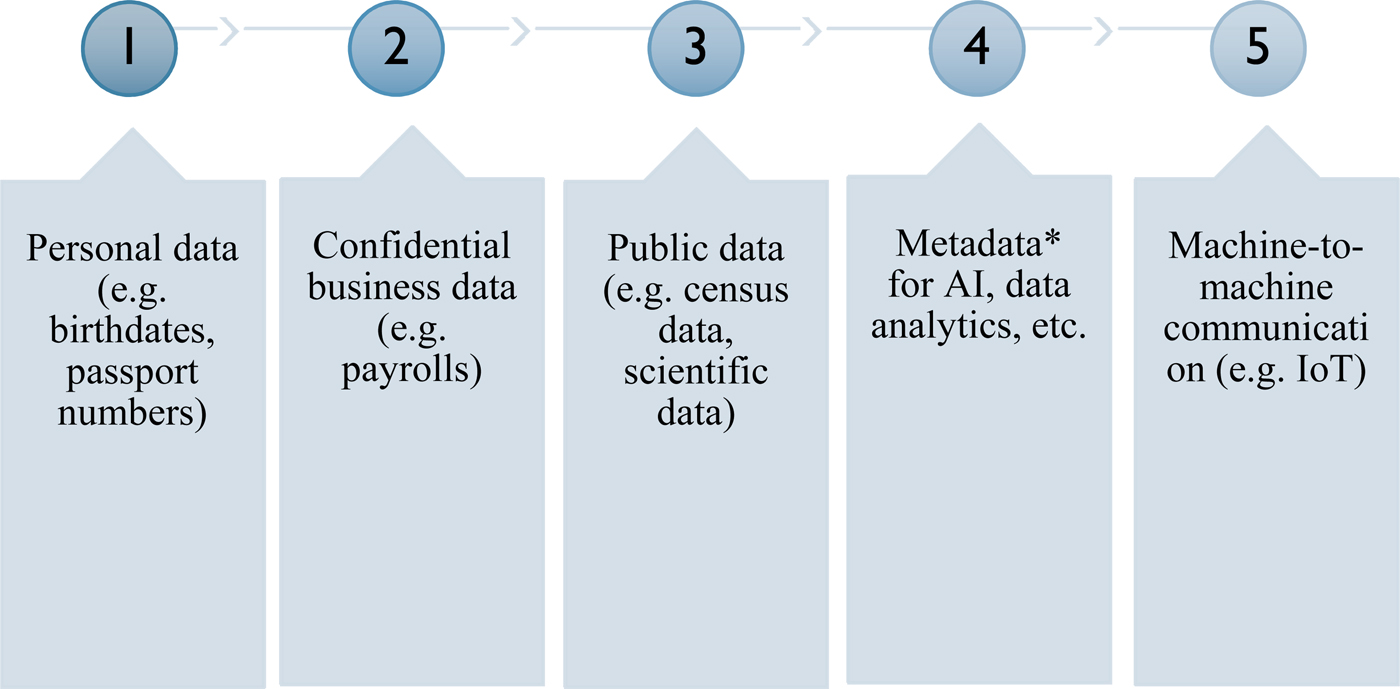
Figure 1. Types of data traded across borders
A new approach built on data type might allow policymakers to better distinguish between regulations designed to control the use of certain types of data and trade-distorting rules. Moreover, it could empower users in the developing world. Netizens in developing countries may be suppliers of personal data, but their firms probably do not control or process data. Policymakers from these states can decide to shape their own markets by developing rules that require companies to pay their citizens for their personal data. Developing countries with large populations are likely to have the most leverage to adopt regulations that require firms to pay rents for their citizens’ data. In so doing, they may be able to upend the market power of huge internet firms. Hence, it could create new demandeurs for trade as a tool to regulate data flows.







