1 Introduction
Rewards programs, also known as loyalty programs, are a mechanism used by businesses and a variety of industries to collect information, retain, and create customer loyalty (Stathopoulou & Balabanis, Reference Stathopoulou and Balabanis2016). Rewards programs can be categorized as point- or level-based. Point-based programs grant points redeemable for products or services; for example, a coffee shop can give a reward for a free coffee if the customer has already bought three in the last week. Level-based programs assign a level according to the behavior of the client; for example, when accumulating purchases, the client can receive additional benefits.
Usually, a single company offers rewards to its customers; however, two or more partner companies can offer rewards; for example, a customer of restaurant ‘A’ can receive rewards in restaurant ‘B’. This strategy can provide substantial benefits to the partner companies: retain customers, mutually publicize their products, and increase their market.
The clients’ participation is fundamental for any rewards program; having a large number of members is not a guarantee for the success of the program. The 2017 Colloquy Loyalty Census shows that, despite that 3.8 billion members of loyalty programs have been identified, more than 50% of members are not actively participating in them and about 28% of consumers leave a program without having charged his rewards (Fruend, Reference Fruend2017).
The three main reasons why members actively participate in rewards programs are as follows: the program is easy to use, easy to understand, or offers useful rewards (Fruend, Reference Fruend2017). The first factor is associated with the usability of a system. Rewards programs with high usability have a positive effect on customer satisfaction (Lee et al., Reference Lee, Moon, Kim and Mun2015). If a loyalty program is difficult to use, clients will decide to abandon it (Stauss et al., Reference Stauss, Schmidt and Schoeler2005), and a high-usability system usually induces high customer satisfaction (Dowling & Uncles, Reference Dowling and Uncles1997).
This paper describes the implementation of a loyalty program based on blockchain technology and mobile phone interactions. Blockchain technology reduces the investment required and improves the security and reliability of the program. The program directly interacts with users (members and partners) by using their mobile phone which improves the usability. The user can still receive benefits if she left her phone at other location or the phone ran out of battery.
The rest of this article is organized as follows. Section 2 presents the related work. Section 3 describes some concepts about blockchain technology that will help to clarify the implementation. Section 4 describes the implementation. Section 5 discusses why the blockchain is required for the proposed loyalty program and presents the concluding remarks.
2 Related work
Contemporary loyalty programs are structured marketing strategies that encourage customers to continue to shop at or use the services of businesses associated with each program, for instance, United Airlines and the Marriot Hotels exchange points (‘miles’) for products and services (Berry, Reference Berry2015). Bijmolt and Verhoef (Reference Bijmolt, Verhoef, Wierenga and van der Lans2017) note that there are still difficulties in the companies to create real customer loyalty, but whenever there are better tools to achieve it (i.e., digitalization), the loyalty programs also foster the total customer experience.
Creating and maintaining a loyalty program is a considerable investment (Dowling & Uncles, Reference Dowling and Uncles1997; Stauss et al., Reference Stauss, Schmidt and Schoeler2005); the expenses of running a loyalty program include extra marketing work, finances, training the associates, technology, and the rewards themselves (Lee et al., Reference Lee, Capella, Taylor, Luo and Gabler2014); furthermore, before starting a rewards program, companies do not have the certainty that it will be successful. Many factors must be considered; for instance, consumers are increasingly careful to choose the program that is most compatible with their life stages, their lifestyle, and their needs (Fruend, Reference Fruend2017). According to the ‘Framework for blockchain adoption’ (Iansiti & Lakhani, Reference Iansiti and Lakhani2017), the proposal in this document falls into the replacement quadrant: it is not a very novel application, but it needs a lot of coordination and possibly changes the way reward programs work.
Small shops can offer rewards by using cards and stamps addable to them; but, this system has some disadvantages as cards cannot be tracked and profiled—for example, a customer can transfer her stamps to someone else. Cuennet et al. (Reference Cuennet, Pouly and Radomirović2015) study the problem of implementing the functionality of paper-based loyalty cards as a mobile app. They define security requirements for such a system (as unforgeability of points, no double-spending of points, customer anonymity, customer privacy, etc.); then, they suggest a simple protocol that satisfies these requirements. In the implementation presented in this paper, the phone number is used as identifier and a simple authentication protocol via SMS is performed.
According to the self-determination theory, blockchain loyalty programs could have positive effects on users’ participation because they cover four needs: economy, autonomy, competence, and relationship (Wang et al., Reference Wang, Luo and Xue2018).
There are several commercial efforts to implement loyalty programs based on blockchain (LoyaltyCoin, 2018). Even, some models have been proposed in the literature (Wang et al., Reference Wang, Luo and Xue2018; Choi, Reference Choi2018); for instance, Choi (Reference Choi2018) proposes an integrated program model that uses credit cards. But, as far as the authors know, this is the first paper that shows a complete implementation of a rewards program.
A local Ethereum node can be used for the transactions (Ibarra González et al., Reference Ibarra González, Dominguez Perez, Garcia Fernandez, Ruimayor and Lara-Alvarez2018); alternatively, a public node can reduce the footprint in a local system. The advantages of using a public node are introduced in the following section.
3 Blockchain technology
A blockchain is essentially a distributed database of records or public ledger of all transactions or digital events that have been executed and shared among participating parties. Each transaction in the public ledger is verified by consensus of a majority of the participants in the system. And, once entered, information can never be erased. The blockchain contains a certain and verifiable record of every single transaction ever made (Crosby et al., Reference Crosby, Pattanayak, Verma and Kalyanaraman2016).
Cryptocurrencies are digital currencies supported by a blockchain, to simulate the registration of transactions of a physical currency between users and encourage the consensus of the canonical version of the transaction history, avoiding altered transactions. Another advantage of using the blockchain is that no third parties are needed to make a transaction. At present, there are stores that accept payments with this type of currency, as well as exchanges that can exchange cryptocurrencies with other types of assets (US dollar, USD). A virtual wallet is an application that facilitates interaction with a blockchain. A wallet allows exchanging cryptocurrencies between accounts (among other things) (Dannen, Reference Dannen2017).
Smart contracts are computer programs that can be correctly executed by a network of mutually distrusting nodes, without the need of an external trusted authority (Atzei et al., Reference Atzei, Bartoletti, Cimoli, Maffei and Ryan2017). Everyone can make (deploy) a smart contract inside the Ethereum’s blockchain, but you can also create new cryptocurrencies or tokens by using smart contracts (Dannen, Reference Dannen2017). The ERC20 standard specifies an API that tokens contracts must implement to integrate with exchange libraries and user interfaces (Vogelsteller & Buterin, Reference Vogelsteller and Buterin2018).
3.1 Reasons to use the blockchain technology
You might ask, ‘why to use the blockchain technology?’ The easiest way to answer this question is to observe the five key points on blockchain usage: (a) multiple writers, (b) absence of trust, (c) central party, (d) data size, and (e) throughput and scalability. The following paragraphs describe these points and their relationship with the proposed rewards system.
Multiple writers. Blockchain technology is specially designed to have multiple writers—for example, if a system needs more than one entity to write to the database, then it may need the use of blockchain technology. In principle, in a small Software as a Service (SaaS) scenario, there is a single instance—in the form of a central webpage— accessing the database, also managed by the same service provider. There is no doubt who is accessing the database; hence, who is accessing or altering the information may depend on the user authentication rules specific to the application.
There are, of course, cases where it is preferable to have multiple copies of the server in order to have a better performance, which is one of the main ideas of using a (elastic) cloud provider; however, they are all essentially the same entity, just different copies or instances accessing the same database, or a copy, which is quickly replicated between each other.
Absence of trust. We have a lack of trust between the parties since the idea is to have the system accessible to many partners. The technology would provide certainty to the system and that the information is valid, despite coming from different sources that are not trusted among everybody in the network, including competitors.
Central party. Since there are multiple parties that may not be trusted between each other, having no central authority provides with certainty that no one may attempt to abuse the system without this attempt being seen by the other participants. Such an attempt would need the approval of a majority or consensus of the other participants, according to whatever rules for approval are used to add data to the distributed ledger, for it to succeed in updating the ledger.
Data size. A disadvantage of the blockchain technology is that it was not intended to be a storage space for a large amount of data.
In our system, the idea is to only store the number of reward points into the chain, and this will keep it lean. As a matter of fact, reward points are valid up to a period of time since the idea is to create active client loyalty; hence, partners may want a way to expire unclaimed points every few months. For instance, we can create a new reward point chain every year.
Throughput and scalability. Finally, the key indicator to not use this technology is that despite the technology was designed to be robust, and a heavy framework for multiple transactions, the ever increasing number of transactions would make it a slow solution in a future if the system is heavily used.
Another way to decide if a blockchain fits the requirement is with the use of a decisional model; several such models have been proposed in the literature, but some of them are sponsored by companies in order to attract sponsors. The model proposed by Wüst & Gervais (Reference Wüst and Gervais2017) was selected because it is simple and probably independent—as it comes from the academy.
As shown in Figure 1, one of the key stages where the system proposed here may seem that does not need a blockchain is where it asks for if we need or want a trusted third party (TTP) to control the information.

Figure 1 Decisional model for blockchain usage (Wüst & Gervais, Reference Wüst and Gervais2017)
3.2 Reasons to use the Waves blockchain
There are two different algorithms that help on choosing the node that will validate the next block in a blockchain, Proof of Work (PoW) and Proof of Stake (PoS). The former selects the first node that solves a challenge, known as a ‘puzzle’; for example, in Bitcoin, the challenge is to calculate a hash with a specific format, consuming a very large amount of resources (O’Dwyer & Malone, Reference O’Dwyer and Malone2014). In the latter, the node is selected by its amount of stake, the more stake you have, the more likely is to be selected as the generator of the next block.
The ‘puzzle’ in the PoW strategy is a hard mathematical problem that usually does not have a known solution in subexponential time; then, the problem is solved by random guessing. The main issue with PoW is that it requires a large amount of real-world resources, such as electricity and computing power. Since the number of possible solutions is gigantic, a professional miner would invest in computer infrastructure to calculate a larger amount of possible answers than a casual participant. This leads to a large energy cost, which in turn presents a sensible ecological footprint.
PoS requires that a miner places a stake, locking up that amount of their own coins in order to be allowed to verify a block of transactions. The miner only needs to prove that it owns a certain percentage of all coins available in a given currency in order to mine. For example, if you own 2% of all Ether (ETH), you would be limited to mine up to 2% of all transactions across the Ethereum blockchain. This way, PoS would be a more fair system than PoW, since anyone could become a miner. PoW allows winning miners to continuously get more computer power to continue mining. PoS limits the blocks a miner could confirm, since it is based on that persons stake in the cryptocurrency.
In principle, Ethereum is the most known Smart Contracts Platform and may switch in a future to the PoS paradigm, but there are some other technologies that let us run smart contracts with different characteristics; for instance, Waves exposes an API in which we can perform requests, and it uses a small variant of PoS algorithm called leased PoS, which was unique at the time of writing this article. Additionally, the Waves platform permits the customization of tokens since 2017, while providing extensive documentation.
Table 1 User stories for the rewards points system

Table 2 Test cases for the rewards points system. Where  $\mathcal{M}_1$
and
$\mathcal{M}_1$
and  $\mathcal{M}_2$
are the members,
$\mathcal{M}_2$
are the members,  ${\mathcal{M}}$
is a false member, and
${\mathcal{M}}$
is a false member, and  $\mathcal{P}_1$
and
$\mathcal{P}_1$
and  $\mathcal{P}_2$
are the partners
$\mathcal{P}_2$
are the partners
In Ibarra González et al. (Reference Ibarra González, Dominguez Perez, Garcia Fernandez, Ruimayor and Lara-Alvarez2018), we proposed a scenario in which each partner is writing directly to the blockchain. This was needed in order to avoid using a central database, described previously, that keeps track of all of the transactions and to only use an SMS for data exchange. This came with the privacy benefit, since only an interested partner would be able to keep track of the transaction in its premise.
The Ethereum requirements to run a local node are ever increasing in terms of storage and broadband use, making it expensive for today’s simple PoS terminals to handle it. We propose using the Waves blockchain, and its public blockchain node services, as a light and fast alternative to Ethereum, since it uses the PoS technology, and a public node.

Figure 2 Flow for the first two user stories: (a)  $\textrm{US}_{\text{01}}$
and (b)
$\textrm{US}_{\text{01}}$
and (b)  $\textrm{US}_{\text{02}}$
$\textrm{US}_{\text{02}}$
4 Loyalty program implementation
The following paragraphs describe the software development cycle phases (analysis, design, and implementation) performed to implement the reward system.
4.1 Analysis
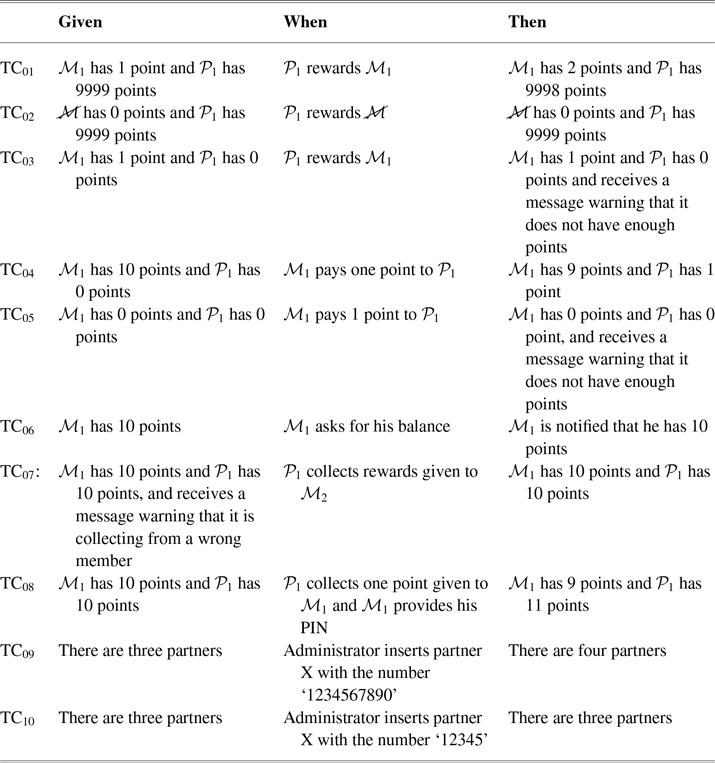
User Stories (USs) are widely used for formulating requirements; they answer three basic questions: who? what? why? The USs selected for the rewards system (Table 1) involve three types of users: partners (associated companies that provide products or services), members (persons who could receive rewards by consuming products), and administrators (who control accounts). A set of test cases (TC) was constructed to test the USs (Table 2).
4.2 Design and implementation
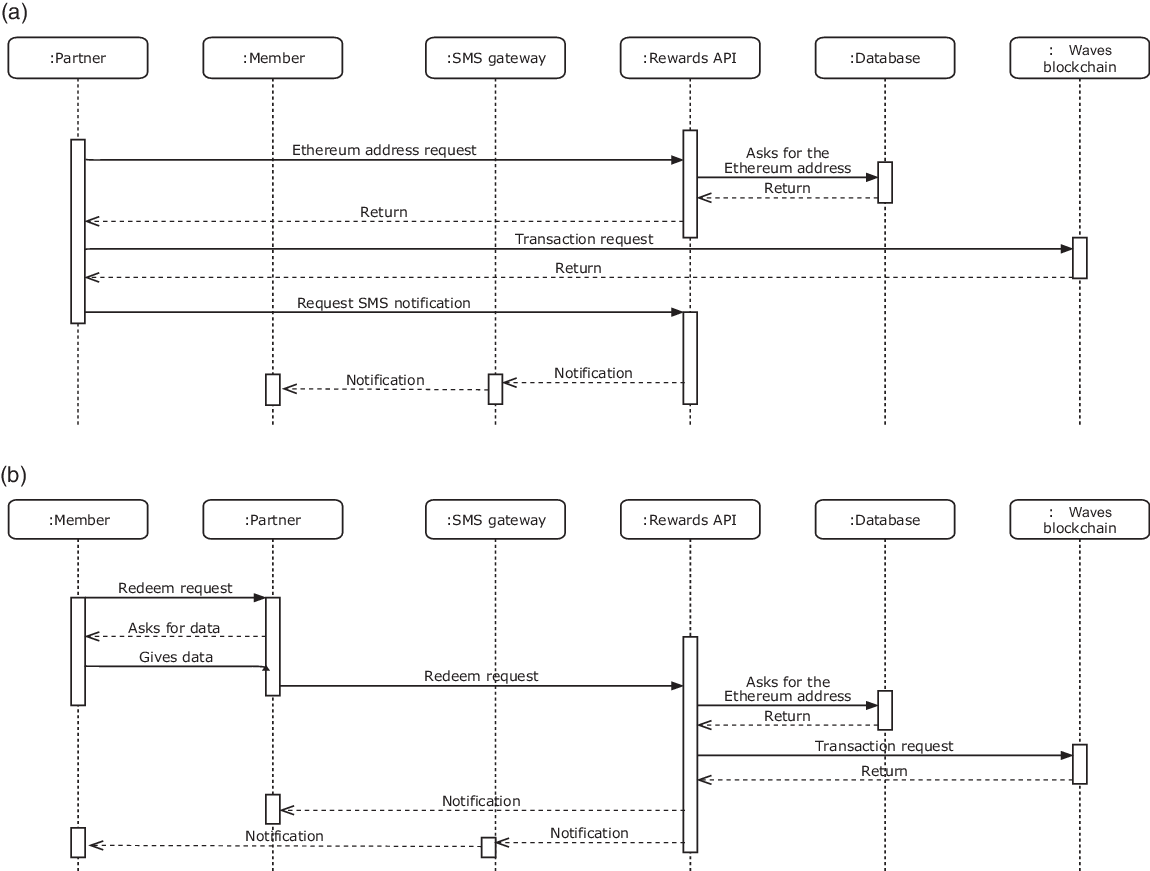
Our system has three key components: (a) a token creator in the Waves testnet, (b) a web API that provides services over the Hypertext Transfer Protocol (HTTP) and (c) a database that stores accounts and PINs. The most important USs are shown in Figure 2.
To reward points to members, a partner (that knows his own Waves address) requests the transaction by sending the number of reward points and the member’s phone number. The system sends a query to the database; to get the member’s address and if the query result is valid, it sends the transaction to the blockchain to the Waves public node. Finally, the transaction is notified to the API, the SMS gateway, and the user (Figure 2(a)).
To redeem points, partners and members agree the amount of points face-to-face. Then, the partner requests the transaction. As in previous cases, the system gets the member’s address, performs the transaction, and sends notifications to both parties (Figure 2(b)).
To make transactions between members and partners, a token is created in the Waves platform—which are compatibles and interchangeables with other Waves tokens.
Table 3 Endpoints

Table 4 Relationship between user stories and endpoints

Table 3 shows the mapping of resource-related actions with the corresponding core module (partners, members, and administrators). These actions provide the required functionality, as shown in Table 4.
Some advantages of using the Waves blockchain are (a) a public node can be used, (b) it uses PoS, (c) it has a decentralized exchange, and (d) it has fixed transaction cost.
5 Discussion and conclusions
It would be a very valuable information for ads agencies to know which partners you are a loyal customer; however, one of our goals here would be privacy to the customer, and having no TTP to log the user would provide confidentiality to the information.
As a matter of fact, there is one central server that let users be part of the system, we could think this system is a malicious TTP, as it is shown in Table 1, there is some associated activity for this server, the idea is to fully unbalance the protocol to the partner, and to the Waves node, this way, the end customer should transparently use our system. This also has the benefit that any key management issues about the blockchain are obviated by the end customer.
Following the decisional model shown in Figure 1, now, the decision relies entirely on the fact that, as a partner, we do not know who else is part of the reward system (only the administration server knows for management purposes). Since we would like to let the end customer to verify the number of reward points available, we preferred a public blockchain, in which only the partners are able to log their transaction.
In this paper, we describe a loyalty program implementation that uses the Waves blockchain technology. Our working system does not require a physical card for identifying customers as it associates them to their phone numbers. All of the interaction between the user and the partner is done by SMS messages, and there is no need to have a physical reward card and even your phone present for some actions. By using the Waves blockchain, we reduce the complexity of the system since there is a public node, it uses PoS technology, and we will be able to exchange tokens between other partners, if required.
Having a local blockchain node for each PoS terminal was not practical since it requires a fast broadband access, and we prefer a solution that is suitable for both big and small partners. The use of the Waves blockchain provided us with a better flexibility than Ethereum in this scenario.
The system is practical, and we expect a larger use of blockchain technology in the future for this type of loyalty card programs and other virtual currency schemes. Visit our repository https://gitlab.com/Antoniio/rewards-codes.