I. Introduction
The Tallinn Manuals represent a notable attempt by prominent international lawyers to facilitate the regulation of cyberoperations by international law.Footnote 1 This attempt constitutes part of a longstanding tradition of legal scholars and practitioners laboring to adapt existing law to new circumstances, opting to extend the law by way of interpretation and analogy rather than by developing a brand-new legal paradigm.
The approach taken in the Manuals toward the regulation of cyberattacks and other cyberoperations is based on several factual and normative premises, which underlie their attempt to reinterpret international law through the drawing of analogies between kinetic (physical) and cybernetic domains.Footnote 2 These premises include the following:
• Cyberattacks have features that are comparable to kinetic attacks, including, at times, similar consequences, such as harm to life, bodily integrity, and destruction of property.
• The cross-border aspects of cyberoperations render them amenable to regulation by international law, the only global body of law capable of comprehensively governing cross-border activity, and there is nothing in international law that would exclude its application to cyberattacks and other cyberoperations.Footnote 3
• One can draw an analogy between state sovereignty or state control over land, sea, and airspace to state sovereignty or state control over parts of the infrastructure that comprises cyberspace, which is physically present inside or passes through state territory.
• An attack from computers located in one country against computers located in another country can be regarded, under certain conditions, as an armed attack under international law, and is subject to international laws regulating the use of force.
• In the same vein, the international law of state responsibility can and should govern the attribution of responsibility to states over cyberoperations undertaken by state officials, as well as for failing to diligently address acts and omissions undertaken by private actors (individuals and non-state actors) in those areas of cyberspace over which states exercise sovereign power or effective control.
On the basis of these basic assumptions, Tallinn Manual 2.0 offers a comprehensive regulatory scheme (154 rules), laying out the general legal principles governing cyberoperations and their interaction with specialized international law regimes, such as human rights law, diplomatic law, space law, and telecommunication law. Most of the Tallinn Rules focus, however, on the interplay between cyberoperations and the use of force (addressing both jus ad bellum and jus in bello).
Both editions of the Tallinn Manual have generated considerable reaction by scholars, policymakers, and bloggers. These reactions range between indications of support, praising the initiative and its contribution to the reduction of legal uncertainty in cyberspace, to more critical comments, questioning key aspects of the Manuals, the premises on which they were constructed and even the adequacy of the drafting process itself. Reactions by states to the Tallinn Manuals also appear to be mixed. Many states seem inclined to take a “wait and see” approach toward the manner in which cyberspace ought to be regulated, maintaining, in effect, a policy of silence and ambiguity. A few states, however, publicly articulated national security doctrines or strategies applicable to cyberspace,Footnote 4 incorporating certain customary international law principles that are included in the Tallinn Manuals, while avoiding explicit references to other parts of the Manuals and, at times, rejecting some of the specific rules articulated in the Manuals.Footnote 5
In this article, we attempt to evaluate the degree to which state conduct is consistent with acceptance on their part of the Tallinn Rules as an international legal framework describing their rights and obligations in relation to cyberoperations. This evaluation is based on mapping the principal reactions to the Tallinn Rules found in the professional legal discourse (including reactions by state representatives), and on investigating a number of incidents occurring since the first Tallinn Manual was published, which appeared to invite the application of international law norms by states that fell victim to harmful cyberoperations launched from other states. Arguably, the way in which attacking and victim states actually conducted themselves throughout such incidents, overtly and covertly, may allow us to make some initial observations on state practice and opinio juris in relation to cyberoperations and on the extent to which they accept the Tallinn Rules as a normative point of reference. Furthermore, the literature survey and case studies enable us to assess the degree to which the relevant epistemic communities—academics and practitioners working in the field—regard international law, as it currently stands, as a generally acceptable framework for shaping interstate activities in cyberspace.
Our principal findings are that there appears to be limited support in state practice for certain key Rules of the Tallinn Manuals, and that it is difficult to ascertain whether states accept the Tallinn Rules and wish them to become authoritative articulations of international law governing cyberoperations. Our research also shows that several states that are heavily engaged in cyberoperations appear at this point in time to have a limited interest in promoting legal certainty regarding the regulation of cyberspace. These findings put into question the degree to which the Tallinn Rules are universally regarded as an acceptable basis for articulating the norms of international law governing cyberoperations.
The legal framework established by the Tallinn Manuals, which has been criticized by some academics as too loose (for not going far enough in limiting unilateral cyberoperations), has been criticized by some state officials as too strict (arguably for going too far in denying victim states the ability to effectively deter and respond to aggressive cyberoperations). Some states have even gone further by challenging the very applicability of international law principles found in the UN Charter and elaborated in the Tallinn Manuals to cyberoperations.Footnote 6 The gap we identify between state practice and some key Tallinn Rules is partly explained by the controversy surrounding the contents of the Rules and, at times, suggests doubts about the normative premises from which they developed.
More significantly, however, the case studies suggest that some states tend to go out of their way to avoid relying publicly and explicitly on specific rules of international law (i.e., jus ad bellum and jus in bello) in connection with cyberoperations, and opt instead for a policy of silence and ambiguity. Hence, some victim states do not acknowledge that they were attacked; when acknowledging that they were attacked, states do not tend to attribute responsibility to other states; and when attributing responsibility, most states do not explicitly invoke the right to engage in countermeasures, which the Tallinn Rules provide. In not a single case we review has a state overtly resorted to kinetic or cybernetic force in response to a cyberattack. These findings cast more doubt on whether states regard international law—not just the Tallinn Rules—as a desirable framework for regulating or justifying their cyberoperations.
It should be noted, however, that the trends identified in this article may not be fixed in time, and that, in fact, recent collective attribution claims and reactive measures resorted to by multiple states in 2017–2018 may signify a shift in the attitude of states to the role that international law can and should play to ensure stability and order in cyberspace. As will be shown below, this shift appears to be aimed at generating greater accountability through reinforcing interstate cooperation in attributing offensive cyberoperations, producing a coordinated reaction to certain cyberoperations and sanctioning the offender states. The growing interest in resorting to international law as a focal point for coordinating interstate responses to cyberoperations and for legitimizing such operations may induce states to adopt a more favorable attitude toward the Tallinn Rules, as representing a comprehensive, specific and plausible articulation of a ready-made international law framework.
At a more abstract level, the findings of our research raise interesting questions about the manner in which states operate under conditions, such as those prevalent in cyberspace, where there exists significant normative uncertainty and where effective enforcement mechanisms are absent. Our case studies reveal three interrelated strategies employed by states under such conditions: (1) Optionality—regarding the framework described in the Tallinn Manuals as optional, in the sense that the states have a choice about whether or not to invoke international law rights and obligations applicable to cyberspace; (2) Parallel Tracks—state practice in the field of cyberoperations appears to develop along two parallel tracks, acknowledged and unacknowledged, resulting in the emergence of two sets of “rules of the game”—international law rules and softer informal rules, which also limit state power. This development challenges the power of traditional sources of international law to explain and predict state conduct in cyberspace; and (3) Gradations in law enforcement—states seem to develop with regard to cyberoperations a nuanced understanding of law enforcement, distinguishing between violations likely to lead to some form of response and those unlikely to do so.
Arguably, all these strategies can be found in some form or another in other fields of international law as well, but their convergence in cyberspace, due to the prevailing conditions of secrecy and deniability, accentuates the limits of legal regulation in this particular field of interstate activity. Still, the recent interest shown by several states in moving away from the policy of silence and ambiguity—through making collective attribution claims, articulating a legal doctrine relating to cyberoperations, and publicly sanctioning wrongdoers—may suggest a need for greater clarity in the application of international law to cyberoperations. We believe that this development may not only render the Tallinn Manuals more relevant than before, it may also create greater interest in the establishment of an international attribution agency to improve collective enforcement prospects.
Part II of the article briefly introduces the Tallinn manuals and reviews the academic controversy surrounding their authority and contents, laying the ground for assessing the attitude of states toward the Tallinn Rules. Part III reviews eleven cyberoperations, potentially covered by the Tallinn Rules because of their interstate attributes, political context, seriousness of the harm caused, and, at times, the framing of the operation by the victim state as a violation of its rights under international law. This part considers how, if at all, the involved states reacted, whether they attributed responsibility to the attacking states, and whether their reactions, in acts and statements, were compatible with the Tallinn Rules. Part IV discusses the implications of the case studies for ascertaining the status of key Tallinn Rules under international law and for ascertaining the role of international law in national security policy in cyberspace. Part V concludes.
II. The Academic Controversy Surrounding the Tallinn Manuals
The Tallinn Manuals were prepared by an international group of experts convened in Tallinn, Estonia at the invitation of the NATO Cooperative Cyber Defense Center of Excellence (CCDCoE). The original group consisted of twenty-three experts (including four observers) from academia and practice, and their work was reviewed by another group of thirteen experts. This led to the publication in 2013 of the first Tallinn Manual, which focused on the laws of war (jus ad bellum and jus in bello). In response to criticisms of the limited diversity of the participating experts (the group was dominated by professionals from the Anglo-American world and by past and present ICRC officers),Footnote 7 and the group's overreliance on Western legal sources,Footnote 8 a second, more diverse group, was convened in Tallinn to revise and expand the first Manual. This time, the group consisted of twenty-one experts (including one observer) and fifty-nine reviewers (each reviewer being assigned with a part of the Manual). Both groups were led by Professor Michael Schmitt from the U.S. Naval War Academy and Exeter University Law School.
Unlike the first Tallinn Manual, the Manual 2.0 covers not only “above the threshold” cyberoperations—that is cyberoperations whose scale and effect may constitute a prohibited use of force,Footnote 9 or which are executed in the context of an existing armed conflictFootnote 10—but also “below the threshold,” i.e., cyberoperations that might violate international law norms other than the prohibition on the use of force or international humanitarian law. Such operations may cause physical damage to, or through, computerized systems, entail their loss of functionality,Footnote 11 or result in interference with or usurping of inherent government functions.Footnote 12 The limited attention such operations received in the first iteration of the Manual was perceived by some as one of its main shortcomings.Footnote 13
Although expert-driven,Footnote 14 the process of formulating the Tallinn Rules involved extensive consultations with states, providing them with the opportunity to have an active role in shaping the law codification process. Toward this end, the Dutch government launched, together with the CCDCoE, “The Hague Process”—a series of meetings held in The Hague with legal advisors from fifty states to discuss under “Chatham House Rules” the draft Tallinn Rules. Still, as subsequent parts of this article show, a number of states, involved in cyberoperations, maintained throughout The Hague Process and beyond a policy of silence and ambiguity in relation to their legal positions on the regulation of cyberoperations, with a view to preserving high levels of operational flexibility through adopting a “wait and see” approach. The reluctance by some states to take a public position on the contents of the applicable law during the drafting of Tallinn Manual 2.0 may explain the controversy that unexpectedly broke out after the issuance of the Manual, concerning the designation of the prohibition against infringement of sovereignty as a specific rule of international law.Footnote 15 Furthermore, as is shown below, the Rules’ impact on state practice and whether they consider the Rules as an acceptable basis for governing cyberoperations remains unclear due to the persistent policy of silence and ambiguity relied on by many states, as well as because of practical problems relating to the application of international law to cyberspace and ongoing challenges to the contents and authority of the Tallinn Rule.
The remainder of this part describes the academic controversy around the Tallinn Rules, which partly derives from difficulties in ascertaining state practice and opinio juris in the field because of said policy of silence and ambiguity. In turn, the criticism leveled against certain aspects of the Rules partly explains the “wait and see” approach some states have adopted vis-à-vis them after their publication. It is against the backdrop of this academic controversy that state practice is discussed in Part III and key Tallinn Rules are reevaluated in Part IV.
A. The Process of Formulating the Rules
The literature on the Tallinn Manuals is extensive, notwithstanding the short time that had passed since the publication of the first Manual in 2013 (and a fortiori since the publication of Tallinn 2.0 in 2017). It includes multiple book chapters, articles, and blog entries. This is probably indicative both of the interest and controversy surrounding the Rules and of the importance attributed to the regulation of cyberoperations in the eyes of multiple observers.
One preliminary issue raised by a number of critics relates to the authority of the Manual, i.e., whether it is reflective of existing international law, or merely the articulation of the views of international group of experts on how international law should be applied to cyberoperations (including, at times, both consensus and dissension views).Footnote 16 Some critics have noted, in this regard, the dearth of state practice, the secrecy enveloping some of the practice that does exist,Footnote 17 the vagueness and diversity of state positions on the topic,Footnote 18 and the fact that the development of cyberoperations is still in a state of flux, as factors that put into question the ripeness of the field for codification.Footnote 19
Other critics expressed concern over the extensive reliance by the international group of experts on open-ended principles and contextual factors, which create significant uncertainty in their application.Footnote 20 More specifically, it was claimed that the international group of experts assigned limited space and minimalist contents to international human rights law (IHRL) in cyberspace, when compared to the treatment given to the laws of war (jus in bello and jus ad bellum).Footnote 21
Finally, a number of critics have questioned the very suitability of international law as the principal normative framework for regulating cyberoperations, noting the “incongruity of the basic structure, design and operating protocols of the internet with traditional notions of Westphalian geography.”Footnote 22 As we show below, the concerns about the authority, contents, and adequacy of Tallinn Rules may explain the decision of some states to reserve judgment on them, as well as on the degree to which contemporary international law does and should regulate cyberoperations.
B. Discussions About Specific Rules
A significant number of writers have addressed specific aspects of the Tallinn Rules. A recurring concern raised by critics of the Tallinn Rules relates to the “use of force” threshold endorsed by the international group of experts. According to Rule 69: “A cyber operation constitutes a use of force when its scale and effects are comparable to non-cyber operations rising to the level of a use of force.”Footnote 23 The experts reached consensus that operations having consequences in the physical worldFootnote 24 (including harm to computer hardware)Footnote 25 can be regarded as potentially comparable in scale and effects to kinetic operations, but could not agree to treat operations lacking physical consequences also as potential use of force.Footnote 26 The lack of consensus on the qualification under jus ad bellum of cyberoperations without physical consequences, but which nonetheless lead to temporary suspension of operational functionality,Footnote 27 result in alteration and destruction of data or code,Footnote 28 or involve “psychological operation” and “cyber espionage,”Footnote 29 has been identified as one of the major shortcoming of the Tallinn Rules.Footnote 30
Arguably, the narrow definition of “use of force” adopted in the Tallinn Rules leads to a counterintuitive outcome, according to which certain serious intentional non-physical harms with a major disruptive potential might not be effectively prohibited, whereas other, less serious harms of a physical nature may qualify as a prohibited “use of force,” and even as an “armed attack,”Footnote 31 giving rise to self-defense action (kinetic or cybernetic).Footnote 32 Certain authors have particularly criticized the ambiguity of the consequential standard allegedly preferred by the international group of experts. They have noted the considerable difficulties of attributing multi-causal consequences to cyberoperationsFootnote 33 and challenged the pedigree of exclusive or almost exclusive reliance on a consequence-based gravity test in jus ad bellum.Footnote 34
Exacerbating concerns about what seems to be a narrow prohibition against the use of cybernetic force are concerns about the narrowness of the self-help remedies available to victim states under the Tallinn Rules—self-defense and countermeasures.Footnote 35 Under Rule 71, “[a] State that is the target of a cyber operation that rises to the level of an armed attack may exercise its inherent right of self-defense.”Footnote 36 Self-defense would only be applicable, however, to operations qualifying as uses of force, which, because of their significant scale and effect, constitute an armed attack.Footnote 37 The narrow consensus definition of what constitutes “use of force” implies necessarily an even narrower right to exercise self-defense in the face of an armed attack. True, a broader right to take responsive action is found under Rule 20, which provides that “[a] State may be entitled to take countermeasures, whether cyber in nature or not, in response to a breach of an international legal obligation that is owed by another State.”Footnote 38 Such measures are subject however to a variety of conditions, including notification and proportionality,Footnote 39 and cannot involve measures themselves amounting to a use of force.
The narrow construction of the right to exercise self-defense or undertake countermeasures under the Tallinn Rules might have derived from fears of the international group of experts that a broader construction might escalate cyberconflicts. The narrow authorization to conduct unilateral operations that generate effects in the territory of other states may also reflect the strong pro-sovereignty bias of the Rules.Footnote 40 Both of these considerations militate against a liberal self-help regime. It may be noted in this regard that although the international group of experts accepted the permissibility of preemptive cyberattacks (as a form of anticipatory self-defense), the utility of this approach has also been questioned given the practical difficulties of identifying preparations before the impending launch of cyberattacks.Footnote 41
With regard to operations falling below the use of force threshold, Tallinn Manual 2.0 posits that they may violate, under certain conditions, other rules of international law. In particular, Rule 4 stipulates that “[a] State must not conduct cyberoperations that violate the sovereignty of another State,”Footnote 42 and the international group of experts took the view that such violations involve physical damage, loss of functionality, or interference with inherent government functions.Footnote 43 Shortly before the publication of Tallinn Manual 2.0, a U.S. official expressed doubts about the notion that sovereignty constitutes a legal rule, which cyberoperations may violate.Footnote 44 Similar skepticism on the matter was recently expressed by the UK attorney general.Footnote 45 Instead, it has been proposed that sovereignty is a legal principle, which justifies and imbues the contents of other, specific legal rules, such as the prohibition against the use of force or non-intervention. According to this latter position, cyberoperations executed in the territory of another state, which do not violate any of these specific rules, do not violate international law just because of their incompatibility with abstract notions of sovereignty.Footnote 46 In concrete terms, the two sides of the debate disagree on whether or not low-scale operations directed against specific targets in other states involving, for example, temporary loss of functionality of hardware or software or tampering with data, are prohibited under international law.
Another difficult issue flagged by the literature on the Tallinn Manuals is the unclear standard for placing responsibility on host states for cyberoperations originating from their territory. The “due diligence” Rule (Rule 7), “requires a State to take all measures that are feasible in the circumstances to put an end to cyber operations that affect a right of, and produce serious adverse consequences for, other States.”Footnote 47 The application of this Rule is, however, uncertain with regard to the duty of host states to prevent prospective attacks, the parallel duties of routing states (i.e., the states through which territory the operation passes), and with regard to how any “constructive knowledge” test applies to host or routing states (i.e., whether the states should have known about the operation).Footnote 48 Note however, that the due diligence rule does not impose on host states a general duty to monitor cyberactivities in their territory with a view to preventing all transboundary harm originating from it (a position informed, inter alia, by privacy concerns).Footnote 49
The open-ended nature of the obligation of the host state under the Tallinn Rules to suppress attacks against other states by non-state actors renders it difficult for the victim state to establish a right to respond to operations originating from non-state actors. This difficulty confronting victim states is further complicated by their lack of legal authority to conduct investigations in the host states or to unilaterally engage in operations against non-state actors situated in such states (unless it can be established that the host state itself breached an international obligation owed to the victim state).Footnote 50 Consequently, it has been claimed that the Tallinn Rules provide victim states with limited guidance on how to react to certain cyberoperations and leave them with relatively few legal options.Footnote 51
A final realm of uncertainty relating to the Tallinn Manuals can be found in the division of labor between different states that could have prevented cyberoperations and mitigated their consequences. The involvement of multiple states, including a number of states from whose territory the operation might have originated, the routing states, and several victim states raises difficult questions of allocating state responsibility, addressing conflict of laws (relating to criminal and civil liability), and applying the laws governing the use of force (e.g., whether one should evaluate cumulatively the scale and effect of the harm caused to different states in order to reach the threshold of harm giving rise to self-defense).Footnote 52
Proponents of the Tallinn Rules, including Professor Schmitt, have responded to most of these criticisms by way of emphasizing the distinction found in the Tallinn Manuals between lex lata and lex ferenda, and explaining that the stated aim of the international group of experts was to reflect the former and not the latter. Thus, even if the Rules elaborated in the Manuals are flawed, uncertain or excessively restrictive (or, in the eyes of some, excessively permissive), they represent the current imperfect state of the law.Footnote 53 Indeed, Schmitt himself believes that the law will gradually develop in the direction identified by some of the critics, including through encompassing data and other non-physical targets of consequential importance in the list of objectives protected by jus ad bellum and jus in bello.Footnote 54
The next part of this article looks into state practice (and, where relevant, also into manifestations of opinio juris). It explores whether lex lata as identified by the international group of experts coincides with the ways in which states actually conduct themselves in connection with cyberoperations, and whether the Tallinn Rules are regarded by them, explicitly or implicitly as an acceptable basis for regulating cyberoperations or even as relevant normative points of reference. Our discussion of state practice, the gaps we identify between the Rules and state needs, interests and expectations, and the policy of silence and ambiguity adopted by some states vis-à-vis the legal regulation of cyberoperations, lays the groundwork for our discussion in Part IV of the direction in which international law norms and institutions governing cyberoperations are likely to develop in light of the uncertain position of states toward the Tallinn Rules.
III. The Case Studies
A. Case Selection Criteria
Countless cyberoperations took place in cyberspace after March 2013, when Tallinn Manual 1.0 was published, and countless more have taken place since February 2017 when Tallinn Manual 2.0 was issued.Footnote 55 The vast majority of these operations are of little interest to the present article, which focuses on the regulation of cyberoperations carried out in an interstate context, and which would have likely attracted the attention of senior policymakers and their consideration of an adequate response. This is not the case with most cyberoperations undertaken in recent years whose source and context is unknown, or which appear to have been of a private criminal nature or involve some form of “hacktivism” not tied to any specific state or to a specific national security or political agenda. Such cyberoperations are typically dealt with by law enforcement agencies and procedures. While law enforcement responses to private cyberoperations raise complicated question of jurisdiction under domestic and international law, as well as questions relating to international coordination and enforcement capacity, those questions are beyond the scope of this article.Footnote 56
The eleven case studies discussed below (and summarized in a table in the Appendix) involve cyberoperations that possibly originate from states or state-sponsored groups or individuals (including groups or individuals who seem to operate with state acquiescence). They sometimes involve operations directed against public targets in the victim states, such as official databases, national infrastructure, and computer systems serving governmental agencies. Although the operations discussed in the case studies were all conducted in a clandestine manner, a political motive related to preexisting international conflicts or tensions can be deduced with respect to most of them on the basis of publicly available materials. Significantly, however, not a single state assumed responsibility for launching any of the cyberattacks or operations discussed in the case studies—a practice that may reflect the preference of attacking states to operate “below the radar,” as well as doubts about the ability to justify their own actions under existing international law norms.
The evidence in the case studies suggests that states targeted by cyberoperations appear to focus their response on detecting, containing, and eliminating cybersecurity breaches, while being inclined to give little publicity to the operations launched against them and to downplay their adverse effects. The tendency of victim states to minimize the publicity given to cyberoperations is probably related to fears that advertising security breaches may inspire new attackers, including “copycat” cyberattackers, and provide them with useful information on the national cyberdefense apparatus. Furthermore, drawing attention to past attacks might undermine public confidence in the government's ability to provide cybersecurity; it may also generate public pressures on governments to retaliate, even though such a retaliation might induce more aggressive cyberoperations in response, and generate significant legal or diplomatic costs.
The lack of transparency in the field—underreporting of cyberoperations and limited attribution claims—makes it difficult to identify relevant state practice. This constitutes a methodological constraint on our research, which relies exclusively on publicly available materials. Some of the data we used comes from primary sources such as press releases, official publications issued by governmental agencies, and cyber security firms’ analyses or investigative reports. Other parts of the data come from secondary sources such as press reports, which sometimes contain unofficial allegations and speculations. We do not claim to present below a full factual picture regarding the reviewed case studies; nor can we claim that they represent all major cyberoperations that have occurred since 2013. To the contrary, they are probably just the very tip of the iceberg.
In selecting case studies, we have used a two-stage process. First, we conducted an extensive web-search designed to identify cyberoperations, which appear to meet the inclusion criteria enumerated below. In this part of the research we were aided by a professional web-search company named Buzzilla (which also scans social media). We then compared the list of cases arising from our own findings with the lists found in two well-regarded depositories of known cyber incidents: the Center for Security and Intelligence Studies’ (CSIS) “list of incidents,” and the U.S. Council on Foreign Relations’ (CFR) Cyber Operations Tracker.Footnote 57 The CSIC list codes the significance of incidents on the basis of their relationship to states and the level of financial loss they caused. The Tracker list focuses primarily on operations potentially attributable to states. From this database, we selected eleven cyberoperations (some actually comprising a series of cyberoperations), which conformed to the following inclusion and exclusion criteria, and which contained relevant information about state practice or opinio juris in relation to cyberoperations:
• Inclusion –
◦ Cyberoperations alleged to have been (1) politically motivated and (2) presumably initiated or supported by a foreign state (that is, by official state entities or by proxies such as state-sponsored groups), and which (3) caused significant damage in the physical world or to strategic government assets (including, erasing or intentionally altering data in the attacked computer or database, or leaking large quantities of sensitive government data). Particular attention was given, in this regard, to cyberoperations, whose direct or indirect consequences are comparable to those of kinetic operations and that might conceivably fall under the scope of application of traditional rules of jus ad bellum or jus in bello,Footnote 58 and to cyberoperations that generated responsive acts or statements by victim states suggesting that they consider the operations conducted against them to have violated the laws of war or infringed their national sovereignty.
◦ Cyberoperations that took place during 2013 or thereafter, and which therefore allow us to explore whether the conduct of implicated states suggests that they accept and follow the 2013 or 2017 Tallinn Rules.
• Exclusion –
◦ Operations aimed exclusively at cyberespionage, given the understanding of the international group of experts that international law does not clearly prohibit espionage activities during armed conflict and in peacetime, unless they generate significant “collateral harm.”Footnote 59 Such excluded cyberoperations typically consist of intrusions aimed at gaining military, political, commercial, or industrial intelligence, and which did not prompt an overt response by the victim state.
◦ Operations appearing to constitute cybercrimes undertaken for financial gain, such as data thefts and ransom demands, unless they are perceived to be politically motivated and linked to a government.
◦ Events preceding 2013, because those events do not assist us in evaluating the degree to which the Tallinn Rules have been accepted by states and whether they refer to the Rules and follow them in their actual practices. To that end, we have excluded from the list famous cyberoperations, which would otherwise qualify as prominent case studies, such as cyberattacks in Estonia (2007)Footnote 60 and Georgia (2008),Footnote 61 and the Olympic Games operation (the Stuxnet attack) (2009–2010).Footnote 62
The case studies are grouped into six categories, according to the identity of the victim state—a categorization that helps us to establish the consistent practice of such states. Five of the cases reviewed relate to attacks against the United States. This is perhaps reflective of the many international political grievances held against it by other states as well as non-state actors, and its relative vulnerability to cyberoperations due to its high level of dependence on digital technology. The availability of information about cyberattacks against the United States may also stem from its relatively high degree of transparency in security matters, and the relative openness of government officials to discuss (at times, under condition of anonymity) cyberattacks and responses thereto. The five U.S. case studies include: (1) attacks against multiple targets in New York State resulting in serious disruption of financial services and, in one case, a potential sabotage of a water dam; (2) the stealing of exceptionally large volumes of national security data from the Office of Personnel Management (OPM), referred to by U.S. commentators as a “Cyber Pearl Harbor”; (3) destruction of multiple computers owned by the Sands Casino; (4) the stealing of data and destruction of computers owned by Sony Pictures Entertainment; and (5) multiple operations aimed at influencing the U.S. presidential election.
Other case studies reviewed in this part include a hacking of the Bundestag network, which was part of an attempt to interfere in Germany's internal affairs and prompted consideration of countermeasures and changes in the organization of the German security forces; destructive attacks against oil companies and infrastructure in Iran and in Saudi Arabia and Qatar; the downing of the Ukrainian electric grid; and two particularly destructive global cyberoperations—WannaCry and NotPetya—that have been attributed to specific source states (North Korea and Russia).
Our review does not focus on whether the attacks themselves are lawful under the Tallinn Rules (or other plausible interpretations of international law)—although many of them clearly appear to be illegal, and no state has assumed responsibility for them or attempted to publicly justify them. Instead, we focus on the reactions of victim states and consider whether they have referred to their legal rights and obligations under international law, as reflected in the Tallinn Rules, or instead maintained silence and ambiguity vis-à-vis the cyberoperations directed against them. State reactions or the absence thereof are arguably indications of state practice and/or opinio juris, which helps us identify emerging rules of customary international law, as well as evidence relating to the manner in which existing treaties should be interpreted and applied. They are also valuable indications of the extent to which the Tallinn Rules are actually regarded by states as an acceptable legal framework for regulating cyberoperations.
In assessing the legal significance of state reactions, we have followed the most recent International Law Commission (ILC) draft conclusions on the identification of customary international law, which include among indications of practice “operational conduct ‘on the ground,”Footnote 63 and among indications of opinio juris “public statements made on behalf of [the] State.”Footnote 64 It is notable in this regard that the ILC draft conclusions provide that “[f]ailure to react over time to a practice may serve as evidence of acceptance as law (opinio juris), provided that states were in a position to react and the circumstances called for some reaction.”Footnote 65 Although the conclusions are silent on the question of secret practice, it is difficult to see how covert action, which other states have little opportunity to react to, can meaningfully serve as the basis of customary international law.Footnote 66
To the extent that states invoke in statements accompanying their practice any international treaty or rely implicitly thereupon, such practice may amount to subsequent practice in the application of the treaty that could establish, over time, the parties’ agreement regarding its interpretation.Footnote 67 In none of the case studies discussed below, however, did states invoke rights under specific treaties, and only in one case (hacks relating to the presidential elections) did a state rely implicitly (and covertly) on international law doctrine.
B. Cyberoperations Against the United States
1. A sequence of cyberoperations against civilian targets in New York (2011–2013)Footnote 68
a. Principal facts
Distributed denial of service (DDoS) operations targeting the financial sector in New York (known also as the “Ababil” or Swallows operation) were conducted between late 2011 to late 2013, reaching a cumulative total of 176 days of attacks.Footnote 69 The attackers—belonging to a group named “Izz ad-Din al-Qassam Fighters”—identified themselves as Arab Muslim youth hackers. The operations were designed to crash the commercial websites of forty-six U.S. financial sector institutions, such as the Bank of America, Wells Fargo, the Nasdaq composite index, the New York Stock Exchange, AT&T, and many others.Footnote 70 The harm sustained by the American financial institutions targeted by the Ababil operation ran into tens of millions of dollars as a result of severe interruptions of the business activities of the financial institutions. Additional damage was caused to hundreds of thousands of customers denied online access to their accounts. In August and September of 2013, the same hackers also obtained unauthorized access into the Supervisory Control and Data Acquisition (SCADA) systems of the Bowman Dam, located in Rye, New York.Footnote 71
b. Attribution
The declared motive of “Izz ad-Din al-Qassam Fighters” was ideological: they demanded that YouTube remove from its website a video insulting the Prophet Muhamad. The American media and cyber experts pointed the finger at Iran, although no official American statement explicitly attributed to it responsibility for the operation. According to media speculations, Iran was seeking to retaliate for the Stuxnet cyberattack that had been conducted against its nuclear facilities by the United States and Israel,Footnote 72 as well as to establish its power of deterrence by demonstrating significant operational capabilities in the cyber domain.
The Head of FETA (Iran's cyber police), Brigadier General Seyed Kamal Hadianfar, denied reports that accused Iran of masterminding the Ababil operations,Footnote 73 and called on the United States to provide Iran, via the Interpol, with any information on the alleged Iranian involvement in the attacks. He promised to investigate such a complaint as Iran had already done in 2011 in connection with a DDoS attack against Citibank. On that occasion, the investigative authorities found no genuine connection between the attack and Iran or Iranian nationals. (The only Iranians nationals involved in the 2011 incident were users whose computers were overtaken by third parties and used as “zombie” or “slave” computers.)Footnote 74
In 2016, three years after the end of the Ababil operation, the FBI succeeded in gathering enough evidence to bring charges against seven Iranian hackers.Footnote 75 The indictments, submitted in March 2016, revealed,Footnote 76 inter alia, the following facts:
• The hackers were employees of two private computer security companies based in Iran that performed work on behalf of the Iranian government, including the Islamic Revolutionary Guard Corps. The two companies were involved in a myriad of national security operations, including in the field of military intelligence.
• One of the defendants received credit from the Iranian Government for his computer intrusion work toward completion of his mandatory military service in Iran.
• For three weeks (Aug. 28, 2013–Sept. 18, 2013), one of the defendants repeatedly obtained unauthorized remote access to the SCADA system of the Bowman Dam, allowing him to gather information regarding the water level, flow rate, and status of the sluice gate (responsible for controlling water levels and flow rates). Luckily, at the time of the actual intrusion, the sluice gate had been manually disconnected for maintenance.
Besides the firm statements made by senior law enforcement officials at the occasion of announcing the charges,Footnote 77 no official statement has ever been made by U.S. officials articulating the implications of linking the Ababil operation to an Iranian government agency or assigning legal responsibility to Iran for them.
c. Response
As far as we know, the Obama administration handled the Ababil operation in a cautious, mostly defensive matter. It had been reported in the press that a counteroperation was considered and rejected, since it would have caused “unintended consequences,” which “could invite escalatory attacks that might paralyze the networks of American businesses.”Footnote 78 Even a proposal by the then National Security Agency (NSA) Director, Keith Alexander, to shut down the computer process in Iran responsible for the DDoS attacks by a covert cyber operation seems to have been rejected because the decisionmakers “were unsure that the action could be so precise and expressed concern that affecting a server in Iran—even if in self-defense—would represent a violation of its sovereignty”Footnote 79 and cause escalation. The option of using diplomatic back-channels was also put off the table, since it was assessed that doing so might prompt the Iranians to intensify their attacks.Footnote 80 A former U.S. official was cited in this connection as commenting that they “knew that Iran had the potential to do harm … and if [the Iranians] had chosen at various moment to aim all their capabilities down a narrow pipe, they would have succeeded in bringing the [American] networks down.”Footnote 81 Apparently, the administration's policy to refrain from an immediate and firm response to stop the operation frustrated the defenseless victim-institutions, which led them to seriously discuss self-help options such as hacking back the attackers’ servers.Footnote 82
Ultimately, it looks as if the U.S. administration decided to respond in a manner that combined diplomacy with technology:Footnote 83 The State Department appealed to its counterparts in 120 countries to enable CERT-to-CERT connections, aimed at removing malicious computer code from servers used as springboards for the Ababil operation. Eventually, the operation concluded toward the end of 2013 as a result of a decision taken by the Iranian authorities, probably due to progress in the multilateral nuclear talks and the prospects of lifting economic sanctions against Iran. As indicated above, the United States supplemented its formal response to the Ababil operation by charging in absentia, in 2016, seven Iranian nationals accused of perpetrating illegal cyber activities,Footnote 84 thus indicating that the United States is aware of precisely what happened, and who was behind the operation.Footnote 85
2. Hacking the Office of Personnel Management (2014–2015)Footnote 86
a. Principal facts
In March 2014, the Department of Homeland Security (DHS) alerted the OPM that its security had been breached and that data was stolen. Since then, DHS and the OPM have monitored the attacker's activity. Despite such monitoring, another attacker succeeded in May 2014 in accessing the system as an employee of an OPM contractor (apparently in full coordination with the March attacker). Between May 2014 and June 2015, large quantities of personnel data of applicants and former and current government employees had been stolen, including their security clearance backgrounds and biometric data.Footnote 87
The motive for this cyber operation could not be determined with a high degree of certainty, although it seems that it was, at least partly, aimed to facilitate intelligence gathering. There is no doubt, however, about the seriousness of the consequences of the operation, which went farther than any previous act of cyberespionage. This led some commentators to dub the operation as a “Cyber Pearl Harbor,”Footnote 88 and “one of the most devastating breaches of U.S. government data in history.”Footnote 89 It also caused severe harm to the privacy of millions of Americans, whose personal data was included in the stolen files.
The then head of the FBI, James Comey, described it as a “very big deal from national security perspective and from a counterintelligence perspective. It's a treasure trove of information about everybody who has worked for, tried to work for, or works for the United States Government.”Footnote 90 Most likely, the operation had short-term adverse consequences for counterintelligence activities, and compromised the safety of American intelligence agents operating abroad.
b. Attribution
Identified as a politically motivated operation, likely to have been undertaken by a foreign nation, the immediate suspects were China, North Korea, and Russia. The United States has not officially blamed any of these nations for the operation, but American media and some senior U.S. politicians identified China as the major suspect.Footnote 91 Cristopher Painter, the coordinator for cyber issues at the U.S. Department of State, stated in Congressional testimony in May 2016, that this “kind of intrusion is just too big to ignore and too disruptive and it is a real concern.”Footnote 92 James Clapper, the then head of the Office of the Director of National Intelligence (ODNI), was the only senior official in the Obama adminsitration who pointed the finger at China by stating publicly that: “you have to kind of salute the Chinese for what they did.”Footnote 93 This may have been, however, a slip of a tongue, as no other statements were made to that effect by U.S. officials in the Obama administration.Footnote 94 Yet the information gathered by American security agencies over time strengthened the assessment that the attackers were Chinese,Footnote 95 and President Obama considered imposing sanctions against individuals or groups engaged in that operation.Footnote 96
China has repeatedly insisted that its government played no role in the OPM hack, and its Foreign Ministry spokesman described the unofficial accusations as “irresponsible and unscientific.”Footnote 97 Still, on December 2, 2015, it was reported that the Chinese authorities had arrested Chinese hacktivists suspected for the OPM hack, and that they would be investigated and prosecuted. The arrests took place in September 2015, a few days before a summit meeting between the leaders of the United States and China.Footnote 98 The Americans were informed about the arrests, but nothing has been published about the results of the Chinese investigation, including information on the identity of the attackers, their motives, and what became of the stolen data.
The incident was handled through bilateral diplomacy and professional channels as if it was a criminal act or an act of “hacktivism,” not a state-sponsored operation. However, this official framing of the OPM hack is improbable. In the view of William Evanina, the director of the National Counterintelligence and Security Center,Footnote 99 the prospect that another country has the stolen data in its possession is higher than the alternative (i.e., that the information is held by criminal hackers, motivated by financial profit). The director observed that those who hold the data have not yet shared it. That made him more confident “that a foreign government did take it and, from an intelligence perspective, I know they'll keep it close hold.”Footnote 100 Still, Evanina maintained the official line of refraining from publicly attributing responsibility to China.
c. Response
According to press reports, U.S. officials, including NSA director Admiral Rogers, and James Clapper, proposed taking response actions against China, such as covert cybermeasures or punitive economic sanctions, in order to deter future cyberattacks.Footnote 101 This suggests that at least two senior U.S. officials were inclined to view the operation as unacceptable—either as a violation of international law governing cyberspace or as a lawful, but exceptionally unfriendly act that violates informal rules of conduct in cyberspace—and that an overt or covert response measure was justified and even necessary for promoting deterrence against future operations. Others warned, however, against retaliating in response to what was actually an espionage operation, implying that the United States might be engaged in comparable operations.Footnote 102 Eventually, the administration did not retaliate; nor did it contest China's claim that it had opened a criminal investigation against private hackers.
In light of Evanina's statements,Footnote 103 it is highly likely that the U.S. administration took a deliberate decision to handle the OPM hack as an espionage operation and not to assign direct or indirect responsibility for it to China. Once qualified as an act of espionage, the operation is not considered under the Tallinn Rules as unlawful per se.Footnote 104 Such an act of qualification, if it indeed occurred, also limited the scope of legally permissible responses by the United States. And indeed, it appears that the U.S. response mostly constituted of undertaking necessary steps to improve defensive capacities and to reduce the adverse ramifications of the operation.
Notwithstanding the ultimate treatment of the OPM hack as a cyberespionage operation, the case was included within our list of case studies for several reasons. First, the operation appears to have had a major disruptive effect on government activities in the field of national security, including delays in the issuance of security contracts requiring background checks and undermining of trust in the ability of the United States to protect sensitive information.Footnote 105 Such operational and reputational harm exceed the scope of damage caused by “normal” interstate espionage operations. Indeed, the operation was regarded by some U.S. policymakers as tantamount to an armed attack (“Cyber Pearl Harbor”) or as a possible violation of international norms of conduct justifying response measures (e.g., economic sanctions). The case study therefore illustrates the claim that we develop later in the article that due to the uncertain and ambiguous state of international law governing cyberoperations, states exercise significant discretion in applying or dis-applying the relevant international law rules (including a choice whether or not to rely on the Tallinn Rules). What appears to be a conscious decision by U.S. officials to qualify the OPM hack as an “acceptable” act of espionage, and not as an unlawful cyberoperation, may underscore the existence of such a choice.
Second, the OPM hack has been handled by the administration and the House of Representatives with a relatively high level of transparency, as a test case for American policy toward harmful cyberoperations. This allows us to distinguish between, on the one hand, forms of response to cyberoperations that were considered at the time by U.S. decisionmakers to be within the boundaries of accepted norms of international law or other, informal, norms governing interstate relations, and, on the other hand, forms of response which were considered excessive or counterproductive. The availability of two “parallel tracks” of regulation of cyberoperations, involving formal and informal rules of conduct, and the existence of gradations in law enforcement, resulting in the treatment of certain rules of international law as virtually non-enforceable, are further discussed in Part IV of this article.
It may be observed that had the OPM data been stolen entirely, without the option of restoring it, a question could have been raised as to whether the operation should be still regarded as a mere act of espionage. At least according to some commentators, altering or permanently erasing sensitive data should be considered as an operation with a use of force or sovereignty infringement dimensions.Footnote 106
3. Cyberoperation against the Sands Casino (2014)Footnote 107
a. Principal facts
On February 10, 2014, the computer systems of the Sands Casino in Bethlehem, Pennsylvania were hacked, and major communication and computer system functions became paralyzed, adversely affecting the company's operation in a significant and long-term manner. Moreover, hard drives were wiped, and a huge quantity of essential data was permanently erased. Experts assessed that such a cyberoperation required a high level of technological capacity, most likely possessed by a state or a state-sponsored group of hackers.Footnote 108
The attackers took control of all of the Sands Casino's websites and posted on them an image of the world's map with flames coming out from the Sands Casino's worldwide locations, a snapshot of Sheldon Adelson, the majority owner of the Sands Corporation, with the Israeli prime minister, and a message condemning the use of weapons of mass destruction.
b. Attribution
The cyberoperation directed against the Sands Casino appears to have been made in response to Adelson's suggestion, offered in October 2013, to drop a small nuclear bomb on the Iranian desert in order to demonstrate U.S. strength and deter Iran from pursuing its nuclear ambitions. Only one year later, on February 2, 2015, a seemingly spontaneous comment was made by the then U.S. Director of National Intelligence, James Clapper, relating to the Sands Casino operation. During a meeting with the U.S. Senate Armed Services Committee, Clapper noted that the operation was the first destructive cyberattack launched by a foreign state, in that case Iran, aimed at an American private company on U.S. soil.Footnote 109
c. Response
The incident was reported to the FBI, which began to investigate it in conjunction with the local state police. No further action has been reported; nor were any further details about the investigation and its findings ever released.
4. Hacking Sony Pictures EntertainmentFootnote 110
a. Principal facts
“The Interview” is a Sony Pictures Entertainment (SPE) comedy film, which describes a plot to assassinate the North Korean dictator, Kim Jong-un. The movie's premier was scheduled for December 18, 2014, with wider release scheduled for Christmas Day 2014. Six months earlier, the North Korean regime tried to stop the distribution of the film by taking measures such as sending an official letter sent to the UN secretary-general, labeling the movie the most “undisguised sponsoring of terrorism, as well as an act of war,”Footnote 111 and threatening to act with “decisive and merciless countermeasure (if) the US administration tacitly approves or supports” the release of the film. The North Korean minister of foreign affairs further published a statement objecting to the release of the movie, using expressions such as “terrorism,” and “a war action” and threatening “decisive and merciless countermeasure.”Footnote 112
On November 24, 2014, a hacking group, identifying itself as the “Guardians of Peace” (GoP), exfiltrated confidential data from SPE's servers. It then gradually released stolen data, over a period of three weeks. The stolen data included, inter alia, information about new film productions that had not yet been released, and a huge quantity of personal information relating to the company's executives, including emails and confidential correspondence among themselves and with celebrities in the movie industry. Following consultations with government officials and private consultants, SPE decided to release the original version of the film as planned.Footnote 113 Although the first GoP emails to SPE management and employees included a general demand for monetary compensation, the real motive of the operation appears to have been an attempt to prevent the film's global distribution as well as an attempt to deter SPE and other studios from insulting the North Korean regime.
On December 16, 2014, the GoP released a written message threatening to commit terror attacks against theaters screening the movie. The message included reference to the terror attacks of 9/11: “The world will be full of fear. Remember the 11th of September 2001. We recommend you to keep yourself distant from the places at that time (If your house is nearby, you'd better leave).”Footnote 114
The cyberoperation directed against SPE did not confine itself solely to data theft, but also comprised destructive malware that caused serious harm to SPE's computer infrastructure. More than 70 percent of its computers were melted down by malware and the company had to invest tens of millions of dollars in IT infrastructure repairs. Additionally, the hack exposed SPE to legal risks due to allegations of negligence in securing its data, and to loss of anticipated income for leaked unreleased films.
b. Attribution
The initial tendency of U.S. officials was to attribute the SPE operation to a foreign state, and the immediate suspect was North Korea. Later, suspicions were also raised vis-à-vis China or Russia and toward groups of hackers sponsored by these states.Footnote 115 Not surprisingly, no state assumed responsibility for the attack; to the contrary, each suspected nation denied any involvement therein. Cybersecurity experts were divided as to whether North Korea was indeed the culprit as the FBI has insisted, or whether another state, or a group of private hackers did it.Footnote 116 Some have even raised the possibility that the hack was carried out by a company insider.Footnote 117
The FBI, which led the investigation in conjunction with other law enforcement and intelligence agencies, had concluded that the Sony hack was attributable to North Korea. This conclusion was based on classified intelligence that could not be disclosed, and on circumstantial evidence, such as the technical similarity of the tools, methods, and infrastructure used in the Sony hack and other cyberoperations linked to North Korean actors that were directed, mainly, against South Korean sites.Footnote 118 On January 2, 2015, the U.S. administration officially announced that it holds North Korea responsible for the Sony hack.Footnote 119 Another U.S. senior official stated that North Korea crossed a threshold from “website defacement and digital graffiti” to an attack on computer infrastructure.Footnote 120
It is worth noting that an investigation conducted jointly by Kaspersky Labs and AlienVault Labs also concluded that the SPE hackers were linked to hackers who have undertaken similar cyberactivities during 2015–2016, mostly against South Korean targets (including a South Korean nuclear power plant operator and Samsung).Footnote 121 Similar findings can also be found in the “Blockbuster Report” issued by another private cybersecurity company, Novetta.Footnote 122 Those technical findings support the FBI's conclusion attributing the operation to North Korea.
c. Response
The immediate response of SPE to the operation directed against it was the cancellation of the planned premier screening and distribution of the movie. This response was criticized publicly for incentivizing future cyber attackers, and for allowing foreign entities to impose their political agenda and to harm the application of the First Amendment on U.S. soil.Footnote 123
Secretary of State John Kerry condemned North Korea for the Sony hack, stating that “these lawless acts of intimidation demonstrate North Korea's flagrant disregard for international norms.”Footnote 124 When President Obama was asked in an interview whether the Sony hack was an act of war, he responded: “No, it was an act of cyber vandalism that was very costly.” He added: “We will respond proportionally, and we'll respond in a place and time and manner that we choose.”Footnote 125 He also indicated that he would review whether to put North Korea back on the state-sponsored terror list, mentioning this as one of the potential responses to be discussed and decided upon. Senator John McCain criticized the president's timid approach, claiming that the president failed to understand that this is “a manifestation of a new form of warfare.”Footnote 126
On January 2, 2015, the U.S. administration announced the imposition of new sanctions with respect to North Korea as the “first aspect of the (American) response” for creating “destructive financial effects on a US company and … [threatening] artists and other individuals with the goal of restricting their right to free expression.”Footnote 127 The sanctions were imposed on ten individuals and three entities associated with the North Korean government. In addition, their entry into the United States and dealings with American entities were prohibited. The presidential order also included the seizing of property held by those individuals and entities in the United States. It has been remarked, however, that the seizure was mostly symbolic because few, if any, assets of targeted individuals or entities were likely to be located inside the United States.Footnote 128 It is not clear what specific evidence the U.S. administration had to connect the ten sanctioned individuals and entities to the Sony hack.
On December 24, 2014, North Korea's internet network was shut down for nine hours and connectivity became intermittent for the next two days. The disruption of internet service has been assumed be a covert response to the Sony hack,Footnote 129 based on the Obama administration's strategy, which included covert actions as part of the U.S. response to hostile cyberoperations.
It is interesting to note that Admiral Rogers, the NSA director at the time, noted that he advised the president to strike back against North Korea, and stressed the need for “creating costs” for hackers in order to build up deterrence.Footnote 130 This is consistent with the position he expressed in connection with the OPM hack, according to which it is essential to adopt measures of deterrence against the escalating risk of cyberattacks.
5. The U.S. presidential campaign/Democratic National Committee hack (2016)Footnote 131
a. Principal facts
In May 2016, six months before U.S. election day, the Democratic National Committee (DNC) invited a cyber security firm (CrowdStrike) to investigate a suspected breach of its network. The investigation team identified intrusions by two well-known hacking actors in cyberspace, the “Cozy Bear” (also referred to as Cozy Duke or APT 29) and the “Fancy Bear” (also known as Fancy Duke, Sofacy or APT 28). Both “Bears” had already established a reputation for being “some of the best adversaries out of all the numerous nation-state, criminal, and hacktivist/terrorist groups … .”Footnote 132 Cozy Bear intruded into the DNC computer system in the summer of 2015, and Fancy Bear had breached the system in April 2016. The investigation team did not find collaboration between the two intruders, or even mutual awareness of each other's activities.
On July 22, 2016, large quantities of written materials were published by WikiLeaks (almost 20,000 emails and 8,000 attachments written by key staff members of the DNC, dating to the period between January 2015 and May 2016). WikiLeaks did not reveal its source of data; still, a new hacker dubbed “Guccifer 2.0” claimed responsibility for the exfiltration (and denied any link to the Russian government). In parallel, the Gmail account of John Podesta, chairman of Clinton's campaign, was breached in March 2016 and thousands of emails were stolen from him. That exfiltration has also been investigated by cybersecurity experts, and “Fancy Bear” was identified as the offender. The stolen data was released gradually by WikiLeaks, from October 2016 until election Day (November 9, 2016).
The DNC hack had the essential components of an “influence cyberoperation” intended to modify attitudes and shape opinions through the dissemination of information and messages.Footnote 133 No significant harm was caused to any computer system (perhaps because indications of harm could lead to early detection of the data theft).Footnote 134 Still, the Obama administration regarded the operation as a serious provocation, with considerable national security implications. This assessment of the gravity of the operation was further compounded by revelations that parts of the operation sought to manipulate the election process itself, with a view to influencing the final tally.Footnote 135
Indeed, a highly classified intelligence report dated May 5, 2017, which was obtained recently by the Intercept (an online news site),Footnote 136 sheds further light on key cyberactivities conducted at the final stage of the election campaign, aimed at influencing the results of the election. The report claims that Russian Military Intelligence executed a cyberoperation against at least one U.S. voting software supplier and sent spear-phishing emails to more than one hundred local election officials in thirty-nine states, between October 27 to November 1, 2016 (shortly before Election Day).
Jeanette Manffra, the head of cybersecurity at the Department of Homeland Security, confirmed that the Russians' cyber penetration efforts during the 2016 presidential campaign targeted twenty-one states and that an “exceptionally small number of them were actually successfully penetrated.”Footnote 137 In the same vein, Michael Daniel, the former White House Cyber Security Coordinator, told a Senate Intelligence Committee hearing held on June 20, 2018, that since June 2016 it was understood that a Russian cyberoperation has been underway with the aim of influencing the elections, inter alia, through targeting the electoral infrastructure.Footnote 138 Daniel opined that it is highly likely the Russians scanned the electoral facilities in all fifty states, and that “it was more likely that we hadn't detected it than it didn't occur.”Footnote 139
The information revealed about the scope of the cyberoperation, the nature of the political data that was exfiltrated, and the way and the timing in which such data was exploited did not leave much room for speculation as to the political motives underlying the operation: to harm the Democratic campaign and reduce Hillary Clinton's chances of being elected. This conclusion was explicitly endorsed in a U.S. Intelligence Community Assessment Report (ICA)Footnote 140 submitted to the president and president-elect, on January 6, 2017 and reaffirmed in the initial findings published by the Senate Select Committee on Intelligence (SSCI) on July 3, 2018.Footnote 141 The question whether the cyberoperation has actually had any impact on the election results is still a hotly disputed issue in the United States political system.Footnote 142
b. Attribution
An investigative team commissioned by CrowdStrike at the request of the DNC to investigate the breach concluded that the “Bears” have engaged in extensive cyberespionage operations, targeting defense, energy, finance, government, and media sectors, mostly in the United States, but also in other countries around the world.Footnote 143 The team also considered the lack of collaboration between the Bears alongside with the responsibility claimed by Guccifer 2.0, but did not find it sufficient to negate the overwhelming indications suggesting Russian responsibility for the intrusions. It explained that such disorder is typical in the Russian Intelligence Community (RIC).Footnote 144 According to this line of thinking, Guccifer 2.0's claim of responsibility was false, and was induced by elements related to RIC in order to deflect responsibility away from Russia. Ultimately, the team concluded that Russia was behind the DNC hack through its proxies, the “Bears,” who “are believed to be closely linked to the Russian government's powerful and highly capable intelligence services.”Footnote 145 Other research cybersecurity firms such as Mandiant and ThreatConnect reached the same conclusions.Footnote 146 Based on sources affiliated with the FBI and Robert Mueller's special counsel investigation, the Daily Beast recently reported that Guccifer 2.0 slipped up and inadvertently exposed itself as an officer of the Russian military intelligence agency (GRU), working out of the agency's headquarters in Moscow.Footnote 147
On October 7, 2016, the U.S. Intelligence Community (USIC) published a Joint StatementFootnote 148 expressing its confidence that “the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations … .” On December 9, 2016, President Obama directed the USIC to conduct a full review and produce a comprehensive intelligence report assessing Russian activities and intentions in recent U.S. elections. A report was prepared and submitted to the president and the president-elect separately, and a declassified version of it was published on January 6, 2017.Footnote 149 The key finding of the report was that President Putin himself ordered a Russian multifaceted influence campaign to “undermine public faith in the US democratic process.”Footnote 150
Two specific points are particularly noteworthy in this regard: First, the USIC identified and analyzed the technical footprints found in the specific hacks in question and reached unanimous conclusions. As indicated before, this outcome conforms to the findings and conclusions of numerous private cybersecurity firms that investigated the same intrusions. Second, the ICA did not include classified evidence that would clearly attribute responsibility to Russia for the cyberoperation. Still, despite this, the USIC was able to attribute responsibility for the operation, explicitly and with a high degree of confidence, to Russian intelligence services.
Russia has regularly denied any involvement in the presidential campaign hacks and has challenged the United States to publicly present evidence establishing its involvement and responsibility. In a news interview published shortly before the elections, President Putin expressed the Russian position emphasizing that: (1) Russian officials did not have enough of an understanding of American politics to successfully compromise the election even if they wished to; (2) “[O]n a State level Russia has never done this,” and this is probably the work of private hackers, who may have deliberately left marks of others in order to camouflage their activities; and (3) “The important thing is the content that was given to the public … . There's no need to distract the public's attention from the essence of the problem by raising some minor issues connected with the search for who did it.”Footnote 151
c. Response
The first leak of emails through WikiLeaks occurred on July 22, 2016, and the first official attribution of the intrusions to Russia was made in the Joint Statement of the USIC on October 7, 2016.Footnote 152 Both occurred during the election campaign, inflaming tensions between the different political camps. Given the concern that the election infrastructure itself, i.e., the voting system, would be targeted,Footnote 153 it was reported that a senior advisor to Obama urged him to send an ultimatum to Putin containing the following message: “Mess with the vote and we will consider it an act of war.”Footnote 154 According to the same report, the president did not want to inflame an already tense situation. Therefore, in September 2016, when Obama met Putin during the G20 summit in China, he did not use the term “act of war.” Instead, he warned the Russian leader “to cut it out,” and that there were going to be “serious consequences if he didn't.”Footnote 155 In fact, it is alleged that there was no subsequent tampering with the election process.Footnote 156 Obama explained later that by sending out a warning, he prevented Russian hacking into the election infrastructure that could compromise the integrity of the voting process.
In retrospect, it appears that even if President Obama's warning in September 2016 prevented a disruption of the voting process itself, it had little impact on the broader Russian influence campaign. First, the “Bears” ended their intrusive activities at least four or five months prior to Election Day, and the director of Homeland Security “assesse[d] that the types of systems [they] targeted or compromised were not involved in vote tallying.”Footnote 157 Second, the leakage of information and resort to other means designed to influence the election outcomes continued even more intensively as Election Day approached despite American warnings.Footnote 158
It has been reported that the White House asked the CIA in October 2016 to prepare options for a covert cyberoperation designed to harass and embarrass the Russian leadership. Vice President Biden reportedly expressed support for such a counteroperation, designed to send “a message” to Putin, hinting that “it will be at the time of our choosing, and under the circumstances that will have the greatest impact.”Footnote 159 Arguably, the vice president implied that a clandestine operation was being considered or is underway.Footnote 160 It has been alleged, in this regard, that Admiral (ret.) James Stavridis, the former NATO supreme allied commander Europe, called for a proportional covert response in cyberspace, such as interfering with Russia's ability to censor internal internet traffic and exposing Putin's financial dealings, with a view to embarrassing the Russian leadership and influencing Russian public opinion.Footnote 161 In his view, if the United States were not to respond to the Russian cyberoperation, it would lose its power of deterrence and suffer from more serious cyberattacks in the future.
Still, some policy advisers to the White House reportedly opposed the idea of a covert response, preferring instead the use of more conventional responsive measures, such as economic sanctions. For example, an unnamed former senior CIA official was quoted as being critical of engaging in covert cyber counteroperations: “anything the U.S. can do[,] … the Russian can do in response.”Footnote 162 Michael Morell, the former CIA deputy director, noted that covert attacks on computer networks initiated by the United States would set a bad precedent for other countries who may seek to imitate it, including when operating against the United States.Footnote 163
Apparently, the internal debate ended on October 31, 2016, with the president's decision to use the “red phone” to stop Russian cyberactivities.Footnote 164 It was reported that Obama sent out an urgent, written warning emphasizing, inter alia, that “international law, including the law for armed conflict, applies to actions in cyberspace.”Footnote 165 The practical meaning of the warning and its allusion to the law for armed conflict, appears to have been that if Russia would interfere in the American election process, by hacking the voting infrastructure or through other means, the United States might consider it as an armed attack and might exercise the right to defend itself. As explained below, such a warning, if indeed given, suggests that the United State was ready to adopt an interpretation of international law applicable to cyberoperations that goes beyond the provisions of the Tallinn Rules that insist on the occurrence of kinetic harm for triggering an armed conflict.
On December 15, 2016, when President Obama was asked about the policy he implemented to tackle the Russian cyber interference in the election process, he responded as follows:
Our goal continues to be to send a clear message to Russia or others not to do this to us because we can do stuff to you. But it is also important for us to do that, in a thoughtful methodical way. Some of it we do publicly. Some of it we will do in a way that they know but not everybody will … . So at a point in time where we've taken certain actions that we can divulge publicly, we will do so. There are times when the message will be directly received by the Russians and not publicized.Footnote 166
It is difficult to ascertain on the basis of open source intelligence whether and how the reported “red phone” warning affected the Russian cyberoperation. As noted above, there are some indications that there were continued cyberoperations directed against the U.S. election process, even after October 31, 2016, although there is a scarcity of information about their precise source.Footnote 167 There is also no publicly available information about any covert U.S. counteroperation against Russia.
On December 29, 2016, President Obama issued an Executive OrderFootnote 168 assuming additional authority for responding to certain cyberactivities that seek to interfere with or undermine election processes and institutions.Footnote 169 Using this new source of authority, nine Russian entities were subject to economic sanctions, two Russian compounds in Maryland and New York that had been used by Russian personnel for intelligence-related purposes were shut down, and thirty-five Russian intelligence operatives were declared persona non grata. In addition, Homeland Security and the FBI released declassified technical information on the cyberactivities of various Russian civilian and military intelligence services, in order to assist cybersecurity experts in the United States and abroad to identify, detect, and disrupt Russia's global campaign of covert cyberoperations.
Obama ended his December 29 press release with the following statement:
These actions are not the sum total of our response to Russia's aggressive activities. We will continue to take a variety of actions at a time and place of our choosing, some of which will not be publicized … [T]he United States and friends and allies around the world must work together to oppose Russia's efforts to undermine established international norms of behavior, and interfere with democratic governance.Footnote 170
This statement appears to suggest that the United States may be open to regard influence campaigns as running contrary to international law governing cyberoperations, thus lending support for an expansive reading of the rule of non-intervention, or for accepting the position of the Tallinn Manuals that international law prohibits operations that violate state sovereignty. Such an interpretation of President Obama's statement would seem to support a move away from the United States’ previous policy of legal ambiguity toward the contents of international law governing cyberoperations, as a first possible step toward imposing sanctions against Russia by the United States and its allies.
Alternatively, the allusion in the president's statement to “international norms of behavior” may suggest that the United States only took that the position that the Russians violated informal norms governing state conduct in cyberspace barring “interference with democratic governance,” without expressing a view on whether specific international law norms were also violated. Under this alternative construction of the statement, the policy of ambiguity toward the contents of international law in cyberspace and the status of the Tallinn Rules was maintained after all.
On February 16, 2018, the U.S. Department of Justice (DOJ) announced that thirteen Russians and three Russian companies have been indicted by a grand jury for committing federal crimes
while seeking to interfere in the United States political system, including the 2016 Presidential election.Footnote 171 The defendants allegedly conducted what they called “information warfare against the United States,” with the stated goal of “spread[ing] distrust towards the candidates and the political system in general.”Footnote 172
According to the indictment,Footnote 173 the defendants conspired, from 2014 onward, to defraud the United States by “impairing, obstructing, and defeating the lawful functions of government … ”Footnote 174 through interference with the American political and electoral processes. Their operation was facilitated by Internet Research Agency (IRA), a Russian company based in St. Petersburg, Russia, which employed twelve out of the thirteen defendants, and through two other Russian companies with many subsidiaries and affiliates, funded and controlled by their owner, Yevgeniy Prigozhin, a well-connected Russian billionaire, dubbed “the Kremlin's Chef.” Prigozhin was included in July 2017 on the list of Russians sanctioned by the presidential executive order and was indicted in February 2018. He is presumed to be the person behind Russia's internet “troll factories.”Footnote 175
The IRA allegedly employed hundreds of people for online and offline activities and controlled an annual budget of millions of dollars to fund those activities. It established and operated—under covert American identities (stolen or fictitious)—hundreds of accounts within U.S. social networks such as Facebook, Instagram, and Twitter. These accounts were used to communicate with the American audience, to sow political discord, and to foster certain political activities. The deputy attorney general emphasized that none of the Americans cooperating with the indicted Russians did it with a mindset of promoting foreign interests and reiterated the position that the charges did not imply that Russian activities actually influenced the outcome of the elections.Footnote 176
On July 13, 2018, the special counsel, Robert S. Mueller III, indicted twelve Russian GRU intelligence officers for hacking into Democratic Congressional Campaign Committee (DNCC) and DNC computers, stealing vast quantities of emails and documents, and staging their release with a view to influencing the U.S. presidential election.Footnote 177 The indictment alleges that the GRU officers were behind the leaks made by “DCLeaks” and “Guccifer 2.0.” They were also charged with identity theft, and using cryptocurrencies for money laundering purposes. Two Russian officers were indicted for hacking computers charged with administering the 2016 elections, with a view to stealing voter data and other information. Indicting Russian nationals who acted directly and indirectly on behalf of the Russian government, knowing that they would, most probably, never be extradited, conforms to the U.S. policy of “naming and shaming” applied in other cyberoperation cases.
Finally, it is worth noting that in March and April 2018, the U.S. administration imposed sanctions on Russian government hackers known as “trolls,” on Russian organizations such as the IRA, GRU, FSB (the successor of the KGB), and on seventeen senior Russian government officials from Putin's inner circle. Those measures were undertaken pursuant to the Countering America's Adversaries Through Sanctions Act (CAATSA) as retaliation for Russia's destabilizing activities, including the meddling with the 2016 US election, the NotPetya attack, and additional cyberoperations targeting U.S. critical infrastructure facilities and striving to destabilize Ukraine.Footnote 178
C. Cyberoperations Against Germany
1. Hacking the Bundestag Network (2015)Footnote 179
a. Principal facts
In May 2015, the Bundestag was reportedly hacked by the APT28 Russian hacking group (“Fancy Bear”/“Sofacy”) linked to GRU. Over 20,000 accounts were breached, and much data having strategic importance was stolen. Following the attack, the internal Bundestag network was shut down for several days as a precaution against additional attacks. Other cyberattacks against German political and public targets have followed, including attacks against German lawmakers, ministers, the Christian Democratic Union party, and foundations (think-tanks) affiliated with Germany's ruling coalition parties.
The motive for these cyberoperations, which did not cause long-term physical damage, appears to have been political: the gathering of political data, including data on the personal life of senior officials, which could be used for influencing public opinion and/or delegitimizing the democratic processes.Footnote 180
b. Attribution
Bruno Kahl, the head of Germany's Foreign Intelligence Service, did not attribute the responsibility directly to Russia. He stated, however, that while attributing an attack to “a State agent is technically difficult … there is some evidence that this is at least tolerated or desired by the State.”Footnote 181 He also added that his office has indications that the attacks came from the Russian region.Footnote 182 By contrast to that cautious approach, Hans-Georg Maassen, the head of the Federal Office for the Protection of the Constitution (BfV—the German equivalent to the FBI), attributed the hacking campaign to Russia,Footnote 183 accusing its intelligence agencies of involvement in obtaining the data and in acts of sabotage.Footnote 184 Reacting to cyberoperations, which took place after the Bundestag hack, he claimed that Russia had tried to conduct an influence campaign in Germany, comparable to the one it has undertaken in connection with the U.S. presidential elections.Footnote 185 The head of the BfV thus put the Bundestag hack in a strategic context—global Russian influence operations conducted in order to further Russian interests through interference in the internal affairs of another state. A similar view was recently expressed by Theresa May, the UK prime minister, who cited the Bundestag hack and other cyberattacks conducted in different European nations as examples of Russian influence campaigns against Western democracies,Footnote 186 and strongly criticized this Russian modus operandi. Footnote 187
c. Response
Based on the views expressed by the heads of German security agencies, German Chancellor Angela Merkel stated that “such cyberattacks, or hybrid conflicts as they are known in Russian Doctrine, are now part of daily life and we must learn to cope with them.”Footnote 188 Germany thereafter took several measures designed to strengthen its military capacity to thwart and respond to cyberoperations, including hacks into strategic assets, and to generate greater deterrence against attackers. A new military cyber command was established to strengthen German capabilities in cyberspace, including offensive capabilities. The German defense minister stated in this regard: “As soon as an attack endangers the functional and operational readiness of combat forces, we can respond with offensive measures.”Footnote 189 Furthermore, legal changes have been discussed in Germany, including the authorization of “hack-backs”—allowing professional cyber units to hit back and remove or destroy attacking servers, if internet providers and server owners “are not ready to ensure that they are not used to carry out attacks.”Footnote 190 According to government officials, this method of operation would be utilized to respond to attacks on an electricity grid or future attacks on the Bundestag.Footnote 191
Although the Bundestag hack might be viewed as an intelligence gathering operation, it was also regarded by senior German officials as part of a broader campaign of Russian cyber influence operations, which seeks to undermine democratic governments. It also resulted in the creation of new military structures with offensive and defensive capacities in cyberspace and in the consideration of far-reaching legal responses (hack-backs). It is for these reasons that we decided to include it in the list of the case studies as an example of a low-scale strategic operation that may nonetheless be regarded as sovereignty-infringing.
It is also worth noting in this regard that the UK prime minister stated in November 2017 that “Russian interference threatens to undermine the international order and Western institutions.”Footnote 192 She also sent a strong message to Russia: “We know what you are doing. And you will not succeed. Because you underestimate the resilience of our democracies, the enduring attraction of free and open societies, and the commitment of western nations to the alliances that bind us. The UK will do what is necessary to protect ourselves, and work with our allies to do likewise.”Footnote 193 Such a response coincides with the U.S. criminal investigations and economic sanctions imposed following the Russian influence operations during the 2016 presidential elections. These developments suggest that cyber influence operations are increasingly being viewed as unacceptable forms of external interference in internal affairs, which might run contrary to international law norms, or at least to informal norms of state conduct applicable to cyberspace.
D. Cyberoperations Against Iran
1. A string of fires and explosions in Iranian oil and gas facilities (2016)Footnote 194
a. Principal facts
On July 6, 2016, fire broke out at the Bouali petrochemical plant in Northern Iran. It took three days to put out the fire. The fire and the toxic clouds of smoke it generated put at risk a population of several hundreds of thousands of people. No fatalities were registered, but the damage caused to the plant was estimated in the tens of millions of dollars. In the same week, a gas pipeline exploded in Marun Oil (in southwestern Iran), causing the death of a worker. At the end of the same month, another fire broke out in the Bisotoon petrochemical plant in the western Iranian city of Kermanshalah. A week later, on August 6, two more incidents occurred within hours of each other: The first was an explosion in a gas pipeline near Gonaveh (in southwest Iran), killing a worker and injuring three more; several hours later, another fire broke out in the Imam Khomeini petrochemical plant (situated near the Marun Oil facility). On September 14, 2016, a gas leak and fire broke at the Mobin Petrochemical Factory that services the South Pars gas field. Four workers were injured.Footnote 195
The Iranian official response issued in July 2016 rejected the possibility that the incidents were caused by a cyberattack. The Iranian Oil Minister explained they were caused due to technical faults and human error. A week later, when the “errors” and “failures” seemed to be recurring with exceptionally high frequency, the Iranian Supreme National Cyberspace Council sent a special team to the sites to investigate the incidents.
b. Attribution
Brigadier General Gholam Reza Jalali, who heads an Iranian military unit in charge of combatting cyber sabotage, put the blame for the leaks, fires, and explosions on faulty equipment components imported into Iran and installed in the different gas production and conveyance facilities, denying that Iran was the subject of a cyberattack.Footnote 196 Indeed, it may be the case that the sanctions imposed on Iran by the international community limited its ability to acquire high-quality parts for industrial manufacturing from Western states, and this could explain some incidents. At the same time, the dependence of Iran on a small number of external equipment suppliers might have also been exploited for launching a cyberattack against its industrial facilities, using imported spare parts from a short list of suppliers for introducing malicious malware into targeted computer systems.
Notwithstanding the official position of the government of Iran, international media quoted a cybersecurity expert who pointed out similarities between the methods that may have been used in the 2016 attacks and in the Stuxnet operation and expressed his firm view that the incident were caused by a state-sponsored cyberoperation.Footnote 197
c. Response
The Iranian regime has not changed its official approach, which denies being subject to a cyberoperation on a significant scale with serious effects. However, it is quite plausible that the Shamoon 3, Shamoon 4, and the Triton operations described below served as Iranian covert retaliation attacks against Saudi Arabia and its allies for their suspected involvement in cyberoperations against the Iranian oil and petrochemical facilities.
E. Cyberoperations Against Saudi Arabia and Qatar
1. The Shamoon cyberattacks (2012–2017) and the Triton attack (2017)
a. Principal facts
I. Shamoon 1 – On August 15, 2012, a malware dubbed “Shamoon” attacked the computer hardware infrastructure of Saudi-Aramco, the world's largest oil company. An unknown group named “Cutting Sword of Justice” claimed responsibility for the attack, which it alleged was a “retaliation against the Al-Saud regime for the ‘crimes and atrocities taking place in … Syria, Bahrain, Yemen, Lebanon [and] Egypt.’”Footnote 198 The malware was designed to replace data on hard drives with an image of a burning American flag, and more than 30,000 computers—three quarters of the workstations of the company—had their memory simultaneously wiped out. The network was put offline, and it took ten days to put it back to operation. Moreover, it took several months to complete replacing all infected computers. The economic harm caused by the attack was enormous, and the then U.S. Defense Secretary, Leon Panetta, described it as “the most destructive attack that the private sector has seen to date.”Footnote 199
II. Shamoon 2 – Two weeks later, RasGas, the Qatari oil company, was attacked in a manner similar to the attack against Saudi-Aramco, compelling it to shut down its network and stop its online activities for several days.Footnote 200 The Qatari authorities did not confirm that they were attacked by the same malware as the Saudis (i.e., Shamoon malware), and they refrained from providing further information about the attack and the damage it caused. It was later reported that the attackers had indeed used the same Shamoon malware and that the attacks resulted in the destruction of computer and data belonging to RasGas.Footnote 201 It may be noted, that both Aramco and RasGas are joint ventures of local and American oil companies.
III. Shamoon 3 Footnote 202 – On November 17, 2016, a version of Shamoon malware was used in an operation against crucial Saudi government agencies, including the transportation sector. Infected computers had their hard drives erased, and they displayed a photograph of the body of Alan Kurdi, the 3-year-old Syrian boy, who had drowned fleeing his country's civil war. Thousands of computers at the headquarters of the General Authority of the Civil Aviation were damaged, critical data was erased, and the operations of the Authority were halted for several days.Footnote 203 The Saudi authorities controlled the publication of information relating to the attack and declared that, although the operation was like Shamoon 1, its impact was “much smaller” and did not disrupt transportation or aviation services.Footnote 204
IV. Shamoon 4 – On January 23, 2017, a digital time bomb, set in advance to explode at a specific time, hit governmental and private institutions in the Saudi Kingdom, including the Labor Ministry and multiple petrochemical companies, such as the National Industrialization Company, Tasnee, and the Sadara Chemical Company, a joint venture between Saudi Aramco and Dow Chemical (an American company).Footnote 205 Like in the case of Shamoon 3, the attacked computers displayed the photograph of the dead Alan Kurdi, after erasing their hard drives.Footnote 206 Recovery took months.
V. The Triton attack – A malware dubbed “Triton” or “Trisis” or “HatMan”Footnote 207 was designed to interact with Triconex Safety Instrumented System (SIS) Controllers, manufactured by Schneider Electric and commonly used in thousands of critical infrastructure plants around the globe, including nuclear, water, gas, oil, and chemical plants to ensure their safe operation. The operation was detected on August 29, 2017, when the controlling system in the attacked plant was shut down as an emergency protective procedure. Several private cybersecurity firms such as FireEye, Dragos, and Symantec along with the DHS, FBI, NSA, and the Pentagon's Defense Advanced Research Projects Agency have been investigating this particularly dangerous attack. No official information has been released about the victim company and the culprit. It was reported unofficially that the malware originated in computers outside Saudi Arabia and targeted a chemical plant in Saudi Arabia, and that it was designed not just to destroy data or shut down the plant but “to sabotage the firm's operations and trigger an explosion.”Footnote 208 The goal has not been achieved due to a bug in the attackers’ computer code that prematurely activated the protective measure for shutting down the plant's production systems.
b. Attribution
The prevailing theory among commentators is that the Shamoon operations were executed by a group of hackers sponsored by Iran.Footnote 209 Then U.S. Secretary of Defense Leon Panetta opined that the cyberattacks directed against Saudi Aramco and RasGas (Shamoon 1 + 2), required a technological capacity that only a few countries in the world had at the time.Footnote 210 The immediate suspect for these operations was Iran,Footnote 211 who may have had a particular interest in targeting U.S. joint ventures, as a form of retaliation for the alleged U.S./Israeli “Olympic Games” operation (aka Stuxnet) conducted against its nuclear facilities.Footnote 212 In addition, Iran may have had other political and ideological reasons to carry out cyberoperations against Saudi Arabia, as the two states are entangled in a religious and geopolitical conflict over hegemony in the Arabian/Persian Gulf, juxtaposing Shiite Muslim states, led by Iran, and rival Sunni Muslim states, led by Saudi Arabia (and supported by Qatar at the time).
The Shamoon operations were not officially and publicly attributed by Saudi Arabia to any state or state-sponsored group, but the prevailing opinion among experts is that Iran was behind these operations, and that the Shamoon 3 and 4 operations were acts of retaliation for the attacks on its gas and oil industry facilities, carried out a few months earlier.Footnote 213 It is notable that both operations were attributed to Iran by U.S. Director of National Intelligence Daniel R. Coates in his Worldwide Intelligence Assessment Report of the U.S. Intelligence Community, submitted to the House Intelligence Committee in February 2018.Footnote 214
Although the Triton operation was more sophisticated and dangerous than previous cyberoperations in the region, and despite indications that it was launched by a state or a state-sponsored group of hackers, no attribution claim was made in this connection. Once again, Iran was named in the media as a possible culprit due to its capabilities in cyberspace and presumed motive to harm Saudi Arabia, with some observers suggesting that it may have cooperated in carrying out the attack with another state.Footnote 215 Interestingly, the Saudi foreign minister stated on February 18, 2018, on the sidelines of the Munich Security Conference, that: “Iran is the only country that has attacked us repeatedly and tried to attack us repeatedly. In fact, they tried to do it on a virtually weekly basis.”Footnote 216
c. Response
No specific attribution claim was made by Saudi Arabia in relation to the Shamoon 3 and 4 and Triton operations, and there are no reports of a response to any of these operations. This conforms to the tendency of both Iran and Saudi Arabia to refrain from attributing cyberoperations in what looks like an ongoing cyberconflict or a string of “tit for tat” operations. Instead, both states seem to opt for covert counteroperations. Hence, the 2016 cyberattacks on Iranian petrochemical facilities may have been acts of retaliation by Saudi Arabia or its allies for the Shamoon 1 and 2 operations (or for kinetic attacks on Saudi Arabia undertaken by Iranian proxies in Yemen),Footnote 217 and Shamoon 3 and 4 and the Triton operations might have been acts of retaliation for the Iranian petrochemical facilities attacks. The lack of reports about further responses may suggest that they took place in a completely covert manner, or that one or more of the parties to the cyberconflict made a policy decision to refrain from further reacting in order to de-escalate the situation.
F. Cyberoperations Against Ukraine
1. Cyberattacks against Ukraine power grid (2015–2016)
a. Principal Facts
Since the Russian invasion of the Crimean Peninsula in 2014, the armed conflict between Ukraine, Russia, and secessionist regions has spilled over to cyberspace where destructive cyberoperations have been undertaken by state-sponsored groups of hackers from both sides of the conflict.
I. Black-Energy 1 – On December 23, 2015, the Ukraine power grid was attacked by hackers who interfered with the functioning of three distribution companies in the western regions of Ukraine. As a result, hundreds of thousands of people had their electricity cut off for several hours.Footnote 218 The hackers succeeded in infiltrating into the control centers of the three companies, replacing their original firmware with malicious malware—KillDisc—which wiped or overwrote data in essential system files. This caused the infiltrated computers to crash. Although electric supply was resumed by means of switching to manual control, it took several months to bring the control centers back to full operation. It was the first time a cyberoperation has been used to cause power outage in a large urban area.Footnote 219
II. Black-Energy 2 – A second outage took place between December 17–18, 2016. This time, a power distribution station near Kiev was switched off and the Northern part of the city was cut off electricity for an hour, reducing by about 20 percent the city's nighttime energy consumption. Senior researchers in two cybersecurity firms (ESET and Dragos Inc.) identified a malware dubbed “Industroyer” or “Crash Override” as the cause of the blackout.Footnote 220 The malware, which was a variation of Stuxnet, was more sophisticated than the one used in the 2015 outage, because it featured a malicious code that could cause the blackout more quickly, on a greater scale, and with the involvement of far fewer attackers. Like Stuxnet, Industroyer/Crash Override could be programmed to run without operator control even in a network that is disconnected from the internet, i.e., it could be used as a “logic/time bomb” programmed to automatically detonate at a predetermined point in time. It could also destroy all files on systems infected to cover its tracks.
b. Attribution
The “Sandworm” hacker group,Footnote 221 also known as “Voodoo Bear” and “Telebots,” was identified by cybersecurity experts as involved in both operations against the Ukrainian power grid.Footnote 222 The same group was identified by cybersecurity firms as responsible for numerous cyberoperations directed since 2015 against almost every sector of Ukrainian society, destroying hundreds of computers of media companies, deleting or encrypting terabytes of governmental data and paralyzing vital infrastructure.Footnote 223
Ukrainian investigators, in conjunction with their U.S. counterparts from the FBI and DHS, concluded that the Black-Energy 1 operation started six months before the actual power outage, as a reconnaissance/espionage operation. Later on, it moved to the stage of weaponizing, i.e., setting the tools of action and getting prepared to launch a cyberoperation against the computer system controlling the electric grid. The investigators’ other conclusion was that the attackers chose not to exhaust their destructive capabilities. Thus, the damage was deliberately limited in scope. Both conclusions led to a third one: the 2015 attack originated from a state or a state-sponsored group, and was primarily designed to send a warning, not to cause destruction on a large scale.
Naturally, Russia became the immediate suspect, as it had several reasons to send such a political message to Ukraine, and senior Ukrainian officials did not hesitate to blame it for the operations. For example, Petro Poroshenko, the Ukrainian president, stated that the 2016 outage (Black-Energy 2) was conducted with the “direct and indirect involvement of secret services of Russia which have unleashed a cyberwar against our country.”Footnote 224 The Kremlin repeatedly denied these allegations.Footnote 225
c. Response
The operations directed against the Ukrainian power grid are considered to be the first cyberoperations conducted within the framework of an armed conflict and aimed at critical infrastructure. Ukraine along with cybersecurity experts from the United States and other NATO member states investigated the operations with a view to drawing the necessary lessons, including reinforcing cybersecurity in order to reduce the risk of recurrence.
As for retaliation, it appears that the parties to the conflict in Ukraine continue to embrace ambiguity and to deny any responsibility for concrete cyberoperations allegedly undertaken by hacktivists or “patriot hackers,” Ukrainians, or Russians trying to retaliate for wrongs committed by the other party.
G. Cyberoperations with Global Effects
Since May 2017, two large-scale cyberoperations have been carried out using leaked NSA hacking tools that exploit vulnerabilities in existing computer networks. Those tools had been stolen and leaked online by a group called “Shadow Brokers,” which is reportedly affiliated with Russia.Footnote 226
1. WannaCry
a. Principal facts
On May 12, 2017, the WannaCry malware spread like wildfire, affecting hundreds of thousands of computers of companies, government agencies, and individuals in more than 150 countries, including Russia, the United States, China, Germany, Ukraine, and the UK (whose National Health Service was particularly affected). The WannaCry malware exploited a hole in the Windows Operating System identified in stolen NSA tools to infect the master boot record, encrypt the hard drive's file system table, and prevent Windows from booting. The affected computers had all data stored in them encrypted and displayed a message demanding payment of a ransom of $300 (later doubled to $600) in Bitcoins within three days in order to unlock the computer. Otherwise, access to the data would be permanently lost.Footnote 227 In August 2017 it was reported that 52.2 Bitcoins (at the time, around $143,000) were withdrawn from online wallets for depositing the ransom payments. It turned out, however, that paying the ransom did not ensure unlocking the computer.Footnote 228
The motivation of those behind the WannaCry operation remains unclear. Ostensibly, it looked like a large-scale criminal ransom operation intended to raise cash. Still, the global manner in which it was executed and the fact that computers remained locked even after the ransom was paid has raised doubts about the true nature of the perpetrators’ motives. One possibility is that the operation was designed to draw attention to the NSA's stockpile of cyberweapons, which exploit undisclosed vulnerabilities in popular software.Footnote 229 Alternatively, it might just have been “meant to cause havoc and destruction” as Tom Bossert, a U.S. Homeland Security advisor put it recently.Footnote 230
b. Attribution
Cybersecurity firms succeeded, within a few days, in identifying the technical footprints of the hackers group (“Lazarus”), which has been linked to North Korea.Footnote 231 A few weeks later it was published that the NSA assesses with “moderate confidence” that North Korea is responsible for the WannaCry operation.Footnote 232 The UK government was the first government to officially announce that North Korea is behind the WannaCry attack. The announcement was made by Ben Wallace, the minister of state for security and economic crime,Footnote 233 relying on the British intelligence community and other knowledgeable sources in the cybersecurity industry.Footnote 234 This assessment was endorsed by Microsoft's President, Brad Smith, stating in a press interview that “all observers in the know have concluded that WannaCry was caused by North Korea using cybertools or cyberweapons that were stolen from the National Security Agency in the United States.”Footnote 235
In late 2017, Tom Bossert, the U.S. Homeland Security advisor to the White House, attributed officially and publicly the WannaCry attack with high confidence to North Korea.Footnote 236 The attribution was based on the investigation's findings and was endorsed by private cybersecurity firms and by five other governments: Australia, the UK,Footnote 237 Canada, New Zealand, and Japan. Bossert was asked about the long time it took to reach the conclusion and replied that time was needed to definitely attribute responsibility.Footnote 238
c. Response
Notwithstanding the attribution of responsibility to North Korea by multiple states, no act of retaliation has been reported. The UK Security Minister merely called on Western nations to develop a “doctrine of deterrent” to prevent further cyberattacks.Footnote 239 Microsoft's president further called on governments “to come together as they did in Geneva in 1949 and adopt a new Digital Geneva Convention that makes clear that these cyberattacks against civilians, especially in times of peace, are off-limits and a violation of international law.”Footnote 240
The U.S. Homeland Security advisor stated that clear attribution is the first step toward holding North Korea accountable, although he did not point to a specific response measure that would actually impose accountability.Footnote 241 Simultaneously, in what seems to have been a coordinated statement, Lord Ahmad, the UK Foreign Office minister for cyber, stated that international law applies online as it does offline and that the UK is determined to respond and to impose costs on those who attack it in cyberspace.Footnote 242 He continued by emphasizing the UK's commitment to strengthening coordinated international efforts to uphold a secure cyberspace. UK officials also remained silent about any measures that were taken or would be taken against the attackers.
It may be noted, however, that Microsoft, Facebook, and other major tech companies did act independently against the North Korean hackers. They shut down the accounts used to launch attacks and remedied their own cyber vulnerabilities, which were exploited in the WannaCry operation.Footnote 243
2. Petya/NotPetyaFootnote 244
a. Principal facts
“Petya,” a ransomware program targeting Microsoft Windows operated computers, was first revealed in March 2016.Footnote 245 On June 27, 2017, a new variant of Petya malware—dubbed “NotPetya” (to distinguish it from the first variant)—was launched against computer systems in Ukraine, using the leaked NSA tool that had already been exploited a month earlier in the WannaCry operation. The tool was employed, however, in a particularly sophisticated manner. NotPetya used an auto-update feature of specific software for tax calculation, which was required from any company operating in Ukraine, to infect many Ukrainian companies, institutions, and facilities, including banks, energy companies, governmental agencies, airports, metros, and even the radiation monitoring equipment within the Chernobyl nuclear power plant. The malware spread promptly and globally, and affected many companies, institutions, and facilities in more than sixty countries including, Russia, Poland, the United States, Germany, UK, Israel, Italy, Netherlands, and others. Almost 80 percent of affected companies were, however, Ukrainian. The malware encrypted all data on the infected systems and demanded a ransom of $300 in bitcoin for decrypting the files.
NotPetya turned out to be a wiper malware like the Stuxnet and Shamoon. Thus, the damage it caused was irreversible as it did not have the capacity to decrypt the files it had encrypted.Footnote 246 NotPetya caused the victim companies unprecedented losses—for instance, the U.S. pharmaceutical giant Merck reported a loss of over $310 million, the courier firm FedEx reported a loss of $300 million, and the shipping firm Maersk reported a loss of $200 million.Footnote 247
b. Attribution
The tactics, techniques, and procedures (TTPs) of NotPetya operators, as analyzed by cybersecurity experts, lead with high confidence to the conclusion that Russia was behind this operation and that it was related to the ongoing armed conflict in Ukraine.Footnote 248 The fact that the operation was launched on the eve of the holiday marking Ukraine's adoption of its first constitution in 1996, and on the same day in which a top Ukrainian military intelligence officer was assassinated in Kiev, also does not seem to be a pure coincidence.Footnote 249 Indeed, Ukraine was the first state to point the finger at Russia for orchestrating the NotPetya operation. The Ukraine Security Service (SBU) stated that the operation was intended to destroy important data and to spread panic, and that it was conducted by the same hackers who attacked the power grid in December 2016.Footnote 250 Russia dismissed these statements as “unfounded blanket accusations.”Footnote 251
The fact that the malware spread out of Ukraine, harming companies, institutions and facilities in other states, including Russian targets, was explained by commentators through two alternative explanations. The attackers might have “underestimated the malware's spreading capabilities … [and it simply] went out of control.”Footnote 252 Or, it may be that, although the hackers could have directed the operation only at victims using Ukrainian IP addresses or shielded from infection computers using Russian IP addresses, they refrained from doing so in order to complicate attribution efforts, and to convince global observers that the operation was a “regular” cybercrime, executed by criminal hackers and not by a foreign state or its proxies.Footnote 253
Initially, no states affected by NotPetya (except Ukraine) came out with a clear, direct, and public attribution claim. Still, on February 15, 2018, the White House press secretary published a direct and official attribution, claiming that the Russian military launched NotPetya to destabilize Ukraine and it turned to be “the most destructive and costly cyberattack in history.”Footnote 254 The statement depicted the attack as “reckless and indiscriminate,” promising to “be met with international consequences.”Footnote 255 Gavin Williamson, the UK defense minister, simultaneously made a similar attribution claim, blaming the Russian military for conducting an indiscriminate attack masqueraded as a criminal hack but targeting primarily Ukrainian financial, energy, and governmental targets, before spreading and affecting many others across the world. The British Minister added that: “Russia is ripping up the rulebook by undermining democracy … targeting critical infrastructure and weaponising information … . We must be primed and ready to tackle these stark and intensifying threats.”Footnote 256 Australia joined the United States and the UK and published a similar statement, attributing to Russia the responsibility for the operation.Footnote 257
c. Response
Some official statements made by senior politicians and practitioners in connection with the NotPetya operation are noteworthy. At the outset of the operation, the U.S. National Security Council stated that the United States is “determined to hold those responsible accountable.”Footnote 258 It took eight months, however, for U.S. authorities to publicly attribute responsibility to the Russian government. It remains to be seen what might be the “international consequence” of holding Russia accountable for the attack.
Jens Stoltenberg, the NATO secretary general, raised at the time of the NotPetya operation the possibility of direct involvement by NATO, and recalled that members of the Alliance agreed the previous year that a cyberattack could trigger Article 5 of the North Atlantic Treaty in the same way it can be triggered in the case of a conventional military assault, and promised more help to Ukraine to bolster its own cyber defenses.Footnote 259 In parallel, the then British defense secretary, Michael Fallon, publicly expressed his concern about the increasing militarization of cyberspace and emphasized British readiness to retaliate militarily if targeted by cyberattacks. ”Footnote 260
On March 14, 2018, the U.S. administration imposed sanctions on the FSB and GRU and six of its senior officials in response to the NotPetya attack.Footnote 261
IV. Analyzing the Empirical Findings—Do States Accept the Tallinn Rules?
Before discussing our main findings and conclusions concerning the relationship between the Tallinn Rules and recent trends in state practice and relating to opinio juris it is worth reiterating three important caveats in our analysis. First, all of the information our research relies on is open source material. Thus, it encompasses only the small part of the perceptible “tip of the iceberg” that states have publicly acknowledged or that the media was able to uncover. We are not able to gauge undisclosed state practice or to fully understand the implications of overt acts and omissions, which are part of a broader set of covert acts and omissions.
Second, states often maintain silence with relation to their activities in cyberspace. This is because a high degree of transparency might expose their vulnerabilities, adversely affect their offensive or defensive capabilities, and weaken their power of deterrence. Thus, states tend to act in cyberspace, offensively or defensively, in a clandestine manner. Although lack of transparency or limited transparency is not exceptional in international law, especially in areas of activities involving proxies and intelligence agencies, the unique features of cyberoperations—e.g., limited or delayed impact in the kinetic world, the extensive use of private proxies, and technological masking capabilities—create exceptionally secretive conditions in relation to an ever-expanding area of interstate activity. As a result of these considerations, our findings and conclusions should be considered with caution, since they are premised on information that paints only a partial, and at times deliberately misleading, picture of reality.
Finally, we have encountered particular difficulties in ascertaining the principled position of states involved in cyberoperations. Considering the sensitivity of national security matters relating to cyberspace, internal discussions within governments and their agencies regarding their overall cyberstrategies and derivative policy choices for specific situations are mostly classified. Furthermore, given their doubts about the adequacy and workability of the existing international law framework, states tend to maintain ambiguity about the legal doctrine guiding their conduct in cyberspace. It is only a handful of public documents and occasional statements made by current or former senior officials that provide us with some opportunity to learn some (but not all) of the factors that actually guide policymakers and comprise part of their cyberstrategy.
A. The Attribution of State Responsibility
In the kinetic world, when an attack occurs for which no one has claimed responsibility, victim states are expected to try to establish, as soon as possible, international responsibility for the attack, so as to enable them to react against the responsible state, or to make demands from the state in whose territory the attack originated. Under the ILC Articles of State Responsibility, a state is responsible for every international wrongful act or omission that is attributable to it, and which constitutes a breach of its international obligations.Footnote 262 Wrongful omissions comprise situations in which a state had failed to act pursuant to obligations stemming from relevant norms of international law, including a due diligence obligation to prevent the use of its sovereign territory for launching attacks against other states.Footnote 263
The unique characteristics of cyberspace, including the ability to act with full anonymity in ways that are difficult to discern across borders, make it difficult, and at times nearly impossible, to clearly attribute responsibility for unlawful cyberoperations. This is, especially the case when the attackers and their collaborators exploit those characteristics to mask their identity. Such difficulties are further compounded by the following features of cyberoperations:
• Unlike kinetic attacks that are typically noticed at the moment of impact (or before impact), permitting an immediate or almost immediate response, cyberoperations, especially those involving “logic/time bombs,” “Trojan horses,” and “trap doors” often take more time to detect.Footnote 264 Moreover, it may take a great deal of time (sometimes even years) to gather the forensic digital and non-digital information that might allow to attribute responsibility to any specific state. As a result, the attributing process very rarely ends promptly with a definite conclusion about attribution that can serve as the basis for timely responsive action.Footnote 265
• The ability of hackers to infiltrate into cyberinfrastructure control systems and execute through them cyberoperations against third states, makes it even more difficult to reliably assign responsibility.
• Although cyberoperations leave trails in the form of TTPs (notwithstanding the attackers’ efforts to mislead their potential trackers), such footprints are usually not sufficient in and of themselves to hold a state accountable for breaching its international obligations. This is because a separate process of legal attribution is needed in order to establish the requisite links between state officials and the attackers, or to show that the state failed to take reasonable measures to curb their operations.
• There is no established body of international law of evidence that clearly defines the legal criteria and standards of proof governing a determination of whether a given cyberoperation should be attributed to individuals, groups, or nations.Footnote 266 Although states are expected to adhere to a standard of reasonableness in attributing responsibility, and absolute certainty is not and cannot be required,Footnote 267 they are not compelled to present the intelligence they relied upon when making the attribution determination. Nor is there an internationally accepted mechanism for legally attributing cyberoperations that victim states can resort to. Thus, they often act as their own judge of the facts, based on loose legal criteria, with very limited oversight over their decisions.Footnote 268
• While classified intelligence might enable the attribution of state responsibility with full, or almost full confidence, at times even rather quickly, national security interests, such as protecting intelligence sources or preserving the secrecy of technological capacities, might induce policymakers to refrain from making a public attribution claim or specifying its basis.Footnote 269 Note that both the United States and the UK have claimed in this regard that international law does not require full transparency as a precondition for attribution responsibility.Footnote 270
All of these considerations encourage victim states and third states to adopt a cautious approach toward publicly attributing state responsibility, consisting of silence and ambiguity. Unfortunately, however, this may convey a message of impunity to other would-be cyberattackers. It may also result in victim states reacting in a clandestine manner—that is, responding to a cyberoperation without making public allegations against any specific state, or even without acknowledging that operation ever happened, so as to reduce any suspicion that could be directed against it for involvement in any future counterattack. Such dynamics push cyberoperations further “below the surface,” using proxies and other unacknowledged operational methods, leading to a more polarized and less accountable threat environment.Footnote 271 These practical considerations reinforce the tendency of states to adopt a “wait and see” approach toward the Tallinn Rules, as lack of ability to publicly and credibly attribute cyberoperations limits the utility of invoking rules that are premised on the ability to attribute responsibility for their violation.
The case studies discussed above flesh out the difficulties in attributing responsibility for cyberoperations. In almost half of the cases (five out of the eleven cases), no official attribution was made, although in several of the cases there were media reports, based mainly on investigations conducted by cybersecurity firm, that indicated at least the nationality of the attackers. In some of these cases, the findings appear to have been sufficient to attribute responsibility to a certain state, if not for its deliberate action, then for omission (violating the principle of due diligence)—that is, knowingly or unreasonably enabling the execution of cyberoperations in or from its sovereign territory. For example, although the U.S. administration appears to have had classified and declassified intelligenceFootnote 272 that should have been sufficient to attribute responsibility for the Ababil operation against the New York financial sector and the Bowman Dam,Footnote 273 and the Sands Casino operation,Footnote 274 there has been no such official attribution claim. Such an outcome may simply reflect the absence of hard evidence tying the attacks to the Iranian regime, but it may also reflect a deliberate policy choice of silence and ambiguity and not publicly assigning responsibility to Iran.
A U.S. policy choice not to publicly attribute attacks to Iran may be explained through a number of possible considerations that illustrate the limited propensity to make attribution claims: there may have been geopolitical considerations, as attribution might have had immediate adverse impacts on the diplomatic efforts, including American efforts, to achieve an international agreement with Iran regarding its nuclear program. Attribution might also have put political pressure on the U.S. administration to overtly react against Iran, although such a course of action might have created legal difficulties in justifying any use of force (kinetic or cybernetic) in response to a cyberoperation that might be regarded as falling short of an armed attack.Footnote 275 Even if the retaliatory operation were to be executed covertly, it might nonetheless have resulted in an undesired escalation, exposing the United States to further and more harmful cyberattacks by Iran.Footnote 276 Public attribution might also have compromised the secrecy of American intelligence sources and revealed its technological capabilities vis-à-vis Iran. In the same vein, resort to American cyberweapons for a covert retaliation operation would have exposed them and rendered the technology accessible to everyone, including to America's adversaries. This is in fact what occurred with Stuxnet, whose success has been emulated since 2012 by other destructive malwares, many of them used against American targets.Footnote 277 Furthermore, drawing more attention to the pattern of reciprocal cyberoperations in U.S.-Iran relations (the Ababil operation was considered by some to constitute an Iranian retaliation for the Stuxnet attacks), might have limited the United States’ ability to deny its involvement in future covert operations against Iran.
Finally, making an explicit claim for attribution of state responsibility for a cyberoperation might limit the ability of the attributing state to maintain silence and ambiguity in respect of its legal policy and operational practices in cyberspace. Attribution claims constitute part of state practice, and they divulge, at times, opinio juris. Thus, they may generate international law that could restrict the ability of states to engage themselves in similar practices in the future. It may be speculated that considerations of such a nature may have led the United States to refrain from publicly attributing responsibility to Iran and China in the Ababil, Sands Casino, and OPM operations.
In most cases in which some form of attribution was made—the Sony hack, the DNC hack, the Bundestag hack, the Ukrainian power outages, and the WannaCry and NotPetya operations—claims of attribution were made after a significant delay. Only in four cases (Sony hack, DNC hack, WannaCry, and NotPetya), was the attribution made in a clear and official manner.Footnote 278 In two cases (Sony and DNC hacks), such attribution was followed by public sanctions, which might have been accompanied by covert cyber-counteroperations.Footnote 279 In some cases, such as the Bundestag and the OPM hacks, attribution was explicitly made to Russian and Chinese hackers, respectively, while avoiding the assignment of responsibility to the relevant government, despite the strong indications that the operations were state-sponsored.Footnote 280 Such a partial act of attribution may also stem from the interest of the relevant victim states in maintaining ambiguity about the precise content of international law regulating cyberoperations.
The attribution process in the case of WannaCry and NotPetya operations was unique in that it resulted in a public, direct, and official attribution by a group of affected states, albeit seven to eight months since the attacks were launched. This time gap was explained by the need of decisionmakers to reach a high level of confidence in the evidence before making attribution, even when based on undisclosed intelligence.Footnote 281 It can be presumed that the process of formulating a joint position on attribution was also time-consuming, and that the length of this process explains part of the delay. Only in the case of operations against Ukraine itself (the attacks on its power grid and the NotPetya operation) was prompt and unambiguous attribution made by Ukrainian officials. This is, however, a non-surprising outcome given the armed conflict context in Ukraine, in which Russia is heavily involved. In this latter context, attribution may serve the need to expose violations of jus in bello, and to generate some accountability.Footnote 282 Still, it appears as if, in practice, the reliance on international law by Ukraine in both cases was minimal and that the process of attribution was largely perfunctory.
Ultimately, attribution is a prerequisite for invoking state responsibility under international law (as reflected, arguably, by the Tallinn Rules), and for justifying an overt reaction that is consistent with international law norms. Such a reaction may consist of acts of retorsion, countermeasures (in response to unlawful cyberoperations falling below the required scale and effect threshold which would constitute an armed attack), and even use of force in self-defense (in response to operations constituting an armed attack). However, technological difficulties typical to cyberspace—the ability to act with full anonymity or through proxies across international borders—and the lack of an internationally acceptable attribution mechanism, might limit the ability of the victim state to publicly make a successful and credible attribution claim that would permit it to undertake countermeasures or use force in self-defense. The practical difficulties of making attribution claims raise difficult questions regarding the requisite standard of proof under international law governing cyberspace, and about the extent to which information underlying attribution claims should be transparent. The international group of experts did not purport to resolve these questions, and they remain governed by general international law principles on evidence.Footnote 283 The legal uncertainty surrounding the attribution process may also tip the balance, at times, toward maintaining silence and ambiguity concerning cyberoperations.
Furthermore, the decision whether or not to assign responsibility or respond to a cyberoperation never relies exclusively on technical forensic findings or legal arguments. There are a variety of political and strategic considerations that decisionmakers are likely to consider prior to making the decision whether and how to react to cyberoperations. Such a decision-making process raises many practical challenges,Footnote 284 and has been characterized as “an art as well as a science,”Footnote 285 multi-layered and “more nuanced, more common, and more political.”Footnote 286 In any event, political and strategic considerations may provide an additional explanation for the prevailing policy of silence and ambiguity.
Still, recent collective attribution claims and public measures taken in response to cyberoperations might indicate a shift in state approach to attribution of responsibility. For the first time ever, a group of states joined together to clearly assign responsibility for destructive cyberattacks (WannaCry and NotPetya) to specific nations (North Korea and Russia, respectively) and to carry out punitive measure (constituting acts of retorsion). This may signify the beginning of a coordinated Western effort to seriously address the threat to world order posed by global cyberoperations. The greater interest shown by some states in making attribution claims may encourage the development of new international norms on evidence relating to cyberoperations, as well as the creation of new international attribution mechanisms. It may also require states to reexamine their policy of silence and ambiguity vis-à-vis the Tallinn Rules.
Interestingly enough, the recent collective claims and measures largely coincided with the UK's retaliation against Russia for its use of a chemical weapon against a former Russian spy on British territory.Footnote 287 In the aftermath of the incident, more than 150 Russian diplomats were expelled from almost thirty states, including the United States, the UK, Germany, and France. Such an unprecedented response was undertaken collectively following a string of Russian provocations, viewed as aimed at destabilizing democratic nations. Consistent with the same proactive approach, the United States and the UK have also held Russia accountable for cyberoperations directed against British and American energy grids, as well as for hacking into global network infrastructure devices like routers and switches.Footnote 288 Once responsibility was assigned, U.S. authorities imposed an additional round of sanctions against Russia.
B. Use of Force
The use of force threshold is a key element of the jus ad bellum regulation of the response to cyberoperations by victim states, separating their right to resort to countermeasures falling short of the use of force from their right to resort to kinetic or cybernetic force used in self-defense.Footnote 289 As the literature survey above shows, this is one of the more controversial aspects of the Tallinn Rules, with the failure to clearly include DDoS attacks and destruction of data under the purview of use of force (and, by necessary implication, under the purview of armed attack) being subject to intense criticism.Footnote 290 In response, proponents of the Tallinn Manuals have claimed that the Rules merely represent the current legal situation (lex lata), and that the eight nonexclusive factors, which the Manuals list for the purpose of defining the use of force threshold best approximate the jus ad bellum criteria applicable in the kinetic domain.Footnote 291 Applying the Tallinn standards, it has been recently claimed by one author that no cyberoperation has yet risen to the level of a use of force;Footnote 292 by contrast, the international group of experts that composed the Tallinn Manuals have identified the Stuxnet attack as meeting the required threshold of use of force, and some experts believed it even met the higher scale and effect threshold of an armed attack.Footnote 293
The uncertainty and controversy surrounding the question of what constitutes a cyberoperation prohibited by Article 2(4) of the UN Charter seems to stem in part from the methodological limits of drawing analogies from kinetic and cybernetic domains, and accommodating the ever-growing role that cyberspace plays in the lives of individuals, groups and states.Footnote 294 They also reflect longstanding policy disagreements relating to the application of legal norms to new technology,Footnote 295 with some policymakers preferring, when applying law to new policy challenges, to err on the side of restraint (refraining from acknowledging new legal rights and obligations), and others preferring to err on the side of greater operational flexibility (rejecting old restrictions on the application of new capabilities).Footnote 296
The eleven case studies examined above support the proposition that states have been so far more inclined to opt for a cautious approach toward the circumstances under which cyberoperations would qualify as a prohibited use of force. In no case has a victim state claimed publicly to have been the target of a prohibited use of force or an armed attack—an outcome that can only be partly explained through the difficulties of attribution of attacks to states or to the legal uncertainty as to whether Articles 2(4) and 51 of the UN Charter regulate the activities of non-state actors who may have launched some of the attacks in question.Footnote 297 Furthermore, the reluctance to make jus ad bellum claims appears to cut across the different definitions of use of force and armed attack discussed in the Tallinn Manuals. While it is perhaps not surprising that no such claims were made with respect to cyberoperations clearly falling below the Tallinn Rules use of force threshold, it is remarkable that no jus ad bellum claims were made with respect to incidents that appear to have crossed this threshold (putting aside the question of whether or not they met or should have met a higher Nicaragua armed attack threshold in order to justify an act of self-defense).Footnote 298
For example, no jus ad bellum claims were made in connection with the Ababil operation, which was designed to have a kinetic effect (interference with the Bowman Dam)Footnote 299 and also caused significant cybernetic harm to the financial industry, and with regard to the attacks on the petrochemical industry in Iran (which are the only known cyberattacks so far resulting in loss of life) and Saudi Arabia. Even the attacks on Ukraine, which had a direct kinetic effect on the local electric network, were not discussed in jus ad bellum terms, although this may be related to the fact that an armed conflict already existed in Ukraine at the time.
The case studies suggest that states do not denounce cyberoperations without physical consequences as running contrary to the prohibition on the use of force.Footnote 300 Yet, there is no indication that they treat very differently cyberoperations with actual or potential kinetic consequences. Nor do we have indications in the information before us supporting the proposition that a series of pin-prick attacks (such as the Ababil operation or Iranian petrochemical industry attacks), or attacks affecting multiple states (such as WannaCry and NotPetya) have been analyzed by states as crossing, cumulatively, the various gravity thresholds.Footnote 301 Here too, the dominant strategy resorted to by states appears to be silence and ambiguity, avoiding thereby the need to limit their concrete policy options in relation to cyberoperations that already occurred as well as to associate themselves with any particular interpretation of international law with regard to future cyberoperations.
Of course, the decision how to respond to any specific cyberoperation (including whether or not to respond to it diplomatically or militarily, in an overt or covert manner, using cybernetic or kinetic counterforce) is predominantly a political rather than legal decision, which factors in a variety of considerations, including the possible interest in maintaining legal ambiguity vis-à-vis the regulation of cyberspace. Thus, the fact that certain attacks have been met by victim states with silence as to whether or not they involve a violation of the prohibition against the use of force does not mean they could not treat them such in the future. Nor does it mean that states have actually decided to reject the Tallinn Rules on the use of force. Rather, our findings are consistent with the proposition that states maintain a “wait and see” approach toward the Tallinn Rules, and that their policy of silence of ambiguity may be one explanation for their limited reliance on the Rules in circumstances in which their jus ad bellum provisions could have been invoked.
C. Sovereignty
As indicated above in Part III, cyberoperations that do not qualify as a use of force or an armed attack may nonetheless violate other rules of international law. According to Tallinn Manual 2.0,Footnote 302 they might violate the sovereignty of another state if their consequences are significant enough (physical damage, loss of functionality, or other forms of infringement that interfere with inherent government functions).Footnote 303 Yet the notion that there actually exists a rule prohibiting a violation of sovereignty that applies over and beyond the specific legal rules that derive from the national sovereignty principle, such as the prohibition against the use of force and the non-intervention rule, has been challenged recently.Footnote 304 Specifically, it has been questioned whether international law bars cyberoperations other than those that reach the scale and effect of a use of force, or that coercively impinge on the inherent functions of other governments, thus violating the non-intervention rule.Footnote 305
The eleven case studies reviewed above do not fully clarify this point of contention. The muted public response to the Ababil, Sands Casino, Shamoon, and Triton operations, as well as to the operations directed against the Iranian petrochemical facilities could either qualify as use of force or a violation of the victim states’ sovereignty if attributable to another state, perhaps suggest a restrictive interpretation of the relevant legal framework consistent with the “sovereignty as principle” approach. On the other hand, the dire warning reportedly issued by President Obama to President Putin in connection with the DNC hack, the diplomatic and law enforcement reactions to the OPM hack, the relatively strong reaction to the Sony hack (which appears to have included a covert response), and the move to develop legislation authorizing “hack-backs” in response to the Bundestag hack, all responses to cyberoperations involving tampering with data, may be indicative of support for a broad application of the sovereignty rule in line with the more expansive views taken by some members of the international group of experts.Footnote 306
It is also interesting to note that none of the attacking states that were allegedly behind the eleven cyberoperations that resulted in harm in the sovereign territory of another state has assumed responsibility for the operation, including when it resulted in relatively minor consequences. While there are obvious political and operational reasons for denying involvement in offensive cyberoperations, the denial of all forms of involvement is consistent with the legal proposition that states do not consider themselves as having a clear right to undertake cyberoperations with consequences in the territory of other states due to the conflict it generates vis-à-vis the sovereignty rule.
Finally, it should be noted that the reactions following the operations directed against the Sands Casino, the Ukrainian electric grid, and the WannaCry and NotPetya operations are less telling about the status of sovereignty in cyberspace than the previous examples just discussed. The Sands Casino operation was directed against a purely private business and may be regarded for this reason to fall outside the scope of the sovereignty rule provided for in Tallinn Manual 2.0.Footnote 307 As explained before, the lack of attribution of responsibility to Iran for the operation, or for failing to exercise due diligence to stop it, may be explained by other policy considerations (e.g., U.S. interest in maintaining ambiguity about relevant due diligence standards and the nuclear disarmament negotiations). At the same time, the operations against Ukraine and the global cyberoperations could have been regarded as a clear violation of the non-intervention rule (and perhaps also of the prohibition on the use of force), which could have warranted a legal response under all approaches to sovereignty infringement. In any event, the statements attributing responsibility to North Korea and Russia for the WannaCry and NotPetya operations did not explicitly refer to infringements of sovereignty, or any specific rule derived thereof. Such statements are thus largely consistent with the policy of maintaining ambiguity vis-à-vis the regulation of cyberspace pursuant to the Tallinn Rules and the notion of sovereignty included therein.
D. Non-intervention
The non-intervention rule, which is derived from the sovereignty principle,Footnote 308 has been referred to in the Tallinn Manuals as part of customary international law.Footnote 309 Rule 66 reads: “A State may not intervene, including by cyber means, in the internal or external affairs of another State.”Footnote 310 According to the International Court of Justice (ICJ) Nicaragua judgment, coercion is a requisite component of the non-intervention rule,Footnote 311 and the Tallinn Manual 2.0 stipulates that coercion is “an affirmative act designed to deprive another state of its freedom of choice, that is, to force that State to act in an involuntary manner or involuntarily refrain from acting in a particular way.”Footnote 312
Arguably, the coercive aspect of intervention is not confined to operations curbing governmental powers and policies, but also to the freedom of choice exercised by the people of a state.Footnote 313 Interventions in election campaigns or referenda (e.g., the U.S. 2016 presidential campaign, Brexit, and allegedly also in 2017 campaigns in France, Germany, and the Netherlands)Footnote 314 might thus be regarded under certain conditions as unlawful coercive interventions. Such coercive intervention might be confined to remote altering of voting results or comparable acts, directly affecting the voting system and elections outcome. Such an operation appears to be proscribed under international law,Footnote 315 as suggested by President Obama's harsh warning to the Russians to refrain from tampering the election process.Footnote 316 Harold Koh and other scholars have taken a more expansive view, arguing that a foreign influence operation using covert activities such as spreading fake news and using social media networks to influence voters may also constitute illegal coercive intervention, which restricts the choice exercised by the voting population.Footnote 317 Still, the covert nature of such practices complicates the ability to identify, in real time, the true scale and coercive attributes of the operations in question.Footnote 318
The non-intervention rule might be violated even in the absence of coercion when the activity in question usurps essential governmental functions.Footnote 319 Arguably, the election process implicates one of most important functions in a democracy. The U.S. Intelligence Community Assessment did not initially support the view that Russia usurped the U.S. election process by meddling with vote tallying,Footnote 320 but new data revealed in May 2017Footnote 321 and in February 2018Footnote 322 supports the claim that there may have been at least an attempt to usurp the process, and that such an attempt could qualify as contrary to the non-intervention rule even in the absence of coercion. The application of criminal indictments by the United States against Russian nationals involved in the influence operation, which came on top of diplomatic sanctions, and the recent public comments of the UK attorney general on manipulation of elections as a form of coercive intervention,Footnote 323 do seem to suggest a tendency to view such operations as violating both national and international law, and a move away from the policy of silence and ambiguity relating to the position of states on the status under international law of cyber influence operations. Such a move brings states closer to embracing the approach taken by the Tallinn Rules regarding the unlawfulness of cyberoperations that infringe state sovereignty. Still, it remains uncertain whether states accept in full the approach taken by the international group of experts relating to sovereignty as a direct source of a prohibition against certain cyberoperations.
Another possible approach to the non-intervention rule in the cyber domain is to encompass within it acts of interference aimed at seriously disrupting and affecting the internal affairs of a foreign state.Footnote 324 It is possible to regard the aforementioned U.S. and UK reactions to influence operations as glossing over the distinction between non-intervention and non-interference, which the Tallinn Manual 2.0 endorses,Footnote 325 thereby lending support to a broad reading of the non-intervention rule under international law.
It is noteworthy, however, that the United States is the only country that has so far undertaken acts qualifying acts of retorsion against foreign states implicated in influence operations. Since acts of retorsion do not necessarily presume that a violation of international law had occurred, they preserve a degree of ambiguity about the contents of international law that the offensive cyberoperation might have violated. Countries other than the United States have tended, instead, to invest in reinforcing cybersecurity perhaps out of fears that resorting to reactive steps might escalate the situation.
E. Due Diligence
Another important element in the normative edifice constructed by the Tallinn Manuals is the due diligence rule, which imposes positive obligations on states to prevent their territory from being exploited to affect the rights of other states in a manner that produces serious adverse consequences.Footnote 326 Although the threshold of “serious adverse consequences” is unclear,Footnote 327 it is safe to assume that operations that would comprise, were they to be directly undertaken by a state, “over the threshold” of international law rules on use of force and non-intervention that would entail state responsibility were they to be directly undertaken by a foreign state would also trigger the host state's rules obligations to prevent such activities undertaken by non-state actors operating from within its territory.
Recent developments suggest, however, that the positions of states on this point have been developing toward less stringent standards of legal obligation. For example, the 2015 report of the Group of Governmental Experts (UN GGE) provided that: “States must not use proxies to commit internationally wrongful acts using [Information and Communication Technologies (ICTS)], and should seek to ensure that their territory is not used by non-State actors to commit such acts.”Footnote 328 This has been perceived as falling short of the must exercise due diligence formulation used in Tallinn Manual 2.0.Footnote 329 Multiple reports about the continued use of proxies by states to conduct cyberoperations, including in the case studies discussed above, and the limited response taken by victim states against host states in this connection are further indications of the limited reliance on the due diligence rule by states in their actual practice.Footnote 330 Experts in the field also appear to have little appetite for construing the Tallinn Rules as requiring permanent monitoring of “national” areas of cyberspace.Footnote 331
Indeed, the case studies discussed in this article illustrate the limited reliance of states on the due diligence rule in formulating their demands against the host states from which the operations emanated. For example, the phased-out nature of the Ababil operation (extending over more than a year), and its serious adverse consequences (damage in the millions of dollars and a risk to the operations of a water dam), could have clearly invited the application of the due diligence rule. This is especially the case after criminal charges were laid against private Iranian actors (albeit with links to the Iranian Revolutionary Guards). But despite the duration of the operation and indications that they emanated from Iranian nationals operating on Iranian territory, the U.S. administration did not overtly make a demand for the involvement of the Iranian authorities (who, at least after being out on notice, should have taken preventive measures that were “reasonably available and practicable”).Footnote 332 In the same vein, other incidents ostensibly involving private actors, the OPM and Bundestag hacks, did not lead the victim states, the United States and Germany, to invoke publicly the due diligence against the putative host states (China and Russia). On the other hand, the DNC hack (which implicated two private groups of Russian hackers) and the Sony hack (which implicated North Korean group of hackers) were responded to, reportedly, at the interstate level. These latter examples can be regarded as an implicit endorsement of the due diligence rule, since the responses were carried out in the face of denials by the host states of direct involvement in the offensive cyberoperations.
The difficulty in assessing state practice in this field and their position vis-à-vis the relevant Tallinn Rules is intimately tied to the problem of attribution discussed above and to the prevailing policy of silence and ambiguity. The ability to claim state responsibility for lack of due diligence often requires that the violating state be confronted with evidence tying the operation in question to its territory, and, even more so, establishing, as a factual and legal matter, its actual or constructive knowledge thereof, and support or acquiescence.Footnote 333 Victim states may be reluctant for a variety of reasons to break their silence and share such evidence with those states that may have been directly or indirectly involved in the operations against them. Making specific demands from the host states on the basis of their international law obligations might also require the victim state to move away from its policy of ambiguity and present a specific understanding of due diligence obligations relating to cyberoperations.
Finally, the availability of information tying the cyberoperation in question to the host state (i.e., establishing an attack by proxy) renders the due diligence rule largely irrelevant, since one would be dealing in such cases with direct state responsibility. Arguably, in the high-profile cases discussed above, deliberate use of proxies appears to have been the rule, not the exception. This reality renders those parts of the Tallinn Rules dealing with due diligence less relevant to state practice, regardless of whether or not they actually support the contents of the Rules comprising these parts.
F. Countermeasures
Countermeasures, involving reactive measures falling short of the use of force, play an important role in the Tallinn Manuals legal framework, as complementing the right to self-defense.Footnote 334 Victim states may resort to countermeasures falling short of the use of force even if by doing so they violate the non-intervention or sovereignty rule (to the extent that it can be recognized as a stand-alone rule), if the state from whose territory the operation originated was implicated in the first-in-time operation, directly or indirectly (through a breach of the due diligence rule). If it cannot be shown that the cyberoperation violated international law, then it seems that only acts of retorsion, which do not in themselves violate international law, including “under the threshold” cyberoperations (e.g., DDoS attacks entailing temporary loss of functionality with a limited disruptive effect), can be taken against the private actor that initiated the first-in-time operation and/or against the state from whose territory the operation originated.Footnote 335
It is hard to deduce from the eleven case studies that state practice follows the provisions of Tallinn Manual 2.0 in connection with the application of countermeasures. There is no indication that the Ababil and Sands Casino operations and OPM and Bundestag hacks led to any countermeasures, overt or covert, despite their significant consequences. By contrast, the DNC hack did result in overt and covert threats of countermeasures or even a threat of use of force if the violations would not stop; it did eventually lead to the actual imposition of diplomatic sanctions. These steps must have been premised on the possibility of attributing the hack directly or indirectly to Russia and on qualifying the hack as a violation of a rule of international law (most probably, the non-intervention rule). Another case potentially featuring a resort to countermeasures is the Sony hack case, which allegedly led to the temporary disruption of internet service in North Korea. Without a public statement on this matter, it is however difficult to deduce the precise legal position taken by the United States on the matter (especially since the Sony hack did not appear to violate the non-intervention rule and was at the low end of the scale for the purposes of finding a violation of sovereignty).
The cyberoperations directed against Saudi Arabia and Iran did not follow the rules of countermeasures and it looks as if both states have been engaged in a covert cyberconflict with one another, with little concern for the legal requirements attendant to the law of countermeasures. Finally, it is useful to mention in this regard the interest shown by German law enforcement authorities in passing a hack-back law following the Bundestag hack, which would allow for countermeasures against the direct source of the foreign cyberoperation. Such an initiative has not become, as of yet, official state policy.
The reluctance to publicly claim the right to apply countermeasures and to follow up thereon, may suggest that states are either not interested in clarifying the state of the law in the field or are uneasy about the stringent conditions associated with its application (including the need to notify the other state and to minimize collateral harm).Footnote 336 It is also likely the case that states rely on mostly non-legal policy considerations (such as fear of escalation or loss of an operational surprise effect) when shaping their reactions to cyberoperations. In the U.S.-Iran context, the cautious approach of the Obama administration, and the lack of a robust overt or covert response, which may relate to political and strategic considerations, has been nonetheless criticized in similar terms as eroding American deterrence.Footnote 337 The pursuance of criminal proceedings against the direct culprits (albeit with limited prospects of actually gaining custody over them) may have been designed to offset some of the concern of being regarded as “soft on cyber.”
G. Distinction and Proportionality
Although our focus in discussing the case studies was on the regulation of the use of kinetic and cybernetic force in self-defense or the use of countermeasures in response to aggressive cyberoperations, they also raise serious questions regarding the compatibility of the measures taken with international humanitarian law, as applied to cyberspace.Footnote 338 The cyberattacks that have been conducted within the framework of an ongoing armed conflict in Ukraine failed to adhere to basic principles of distinction and proportionality. In the same vein, in the case of NotPetya, the attackers seem to have intentionally chosen an indiscriminate and disproportional method of operation (since they failed to confine the operation to specific IP addresses in Ukraine). Interestingly enough, public reactions to these operations have not focused largely on their indiscriminate and disproportionate nature, even though the White House depicted NotPetya in one statement as “reckless and indiscriminate,” and “the most destructive and costly cyber-attack in history.”Footnote 339
In the same vein, it appears as if the operations directed against the petrochemical and oil industry in Iran and the Shamoon and Triton operations against Saudi Arabia were conducted in violation of both jus ad bellum and jus in bello rules, with little regard for the rights of uninvolved civilians. In both cases, silence on the part of the involved states does not allow for an adequate analysis of the way in which they interpret relevant jus in bello terms, such as what constitutes an “attack,” “military object,” or “collateral damage,” or how to apply the proportionality rule in cyberspace. Nonetheless, the lack of acknowledgement and attribution of the operations and the serious effects they had on civilian populations and property might be indicative of a limited interest in upholding international humanitarian law principles, as reflected in the Tallinn Rules. This state of affairs may, in turn, also suggest that although the Tallinn Manuals contributed to closing the gap between international humanitarian law (IHL) and new forms of conduct of hostilities, the analogy to the kinetic world has its practical limits, and that, as a result of the limited fit between the law and its field of application and the tendency of states to opt for a policy of silence and ambiguity in respect of the norms of IHL too, the Tallinn Rules actually offer limited protection to civilians.Footnote 340
H. General Implications for International Law
At a more abstract level, the findings of our research provide interesting insights about the manner in which international law develops and functions under conditions of significant normative uncertainty and in the absence of effective enforcement mechanisms. Such conditions are found in cyberspace, where the law on the books and its application in practice are unclear and where, because of the problem of attribution and other considerations that lead states to refrain from openly resorting to countermeasures and other response measures, international law is chronically underenforced. Still, while cyberspace may represent an extreme example of the application of law in circumstances of legal uncertainty, many of the dilemmas confronting states in this domain have also been encountered in other fields. Hence, our case studies may offer relevant lessons to all students of international law and invite further research into the implications of state conduct in cyberspace for general international law theory.
To be clear, even states skeptical of the Tallinn Rules do not regard cyberspace as a norm-free zone. Certain non-binding rules of conduct have emerged out of state practice and national strategy statements.Footnote 341 Some of them were broadly endorsed by the 2015 Report of the UN GGE,Footnote 342 and states have started to accept them through multilateral statements,Footnote 343 and international agreements regarding cybersecurity cooperation.Footnote 344 Over time, several of these non-binding rules are likely to consolidate into customary international law. Nevertheless, the case studies suggest that a significant normative gap exists in relation to the regulation of interstate cyberoperations. This is because the combination of silence and ambiguity in state practice and their reluctance to articulate their official policy in cyberspace prevents or, at least, slows the development of global norms of conduct.
The Tallinn Rules can play a potentially important role in this field as normative points of reference, around which customary international law and treaty interpretation can further coalesce.Footnote 345 Their existence inspires states and commentators to engage in a process of legal translation—a good faith effort to translate existing legal norms to the new circumstances of cyberspace.Footnote 346 Still, the process of establishing new rules of international law or accepting the applicability of existing rules requires a certain level of interstate communication and public diplomacy, which the aforementioned policy of silence and ambiguity undercut.Footnote 347
I. Optionality
The reluctance of states to invoke the Tallinn Rules in relation to cyberoperations in which they find themselves involved as the attacking or victim state may stem not only from uncertainty as to whether the Tallinn Rules accurately reflect international law, but also from deeper doubts as to whether international law should govern all activities in cyberspace. Such doubts, in turn, may encourage states to develop a policy of optionality toward the application of international law, that is to adopt a deliberate strategy of treating the applicable international law framework as optional, in the sense that states may choose whether or not to invoke the legal discourse of international rights and obligations in their mutual interactions in cyberspace. Indeed, the case studies show that state tend to embrace a policy of silence and ambiguity, but that even when they acknowledge that they were victims of cyberoperations directed against them, the rhetoric they use to describe the operation and their planned reaction thereto tends not to include legal arguments or references to specific norms of international law.
Optionality is particularly relevant for those states that have the greatest capacity to operate covertly in cyberspace and to protect their national security interests outside the framework of international law.Footnote 348 Paradoxically, the decision of states with advanced technological capacity to refrain from invoking international law in relation to the cyberoperations in which they are involved implies that their contribution to the development of customary international law norms in this field might be smaller in some respects than that of states with more limited capacity, which may have no choice but to conduct themselves within the existing legal framework.
One illustration of optionality can be found in President Obama's reaction to the Sony hack, which promised a U.S. response in the place and time and manner that it chooses,Footnote 349 and which manifested itself, probably, in an unacknowledged and possibly extralegal cyberoperation against the North Korean internet infrastructure. The same approach also characterized the Obama administration's reaction to the DNC hack, which similarly promised a clandestine response (though referring obliquely to “Russia's efforts to undermine established international norms of behavior, and interfere with democratic governance”).Footnote 350 The lack of explicit reference to an international law framework when addressing the operations conducted against the United States and the anticipated response thereto, appears to reflect a deliberate policy choice to deal with the operation outside the four corners of the international law framework.
The choice of whether or not to invoke international law norms is even more apparent in those cases in which victim states did not acknowledge being attacked or refrained from attempting to attribute the attack to another states, thus consciously choosing not to facilitate the application of international law to the situation at hand. At the same time, the interest shown recently by multiple states in collectively attributing international responsibility for global cyberoperations, such as WannaCry and NotPetya, may reflect a conscious decision on their part to invoke an international law framework, with a view to facilitating a coordinated overt response, which could enjoy broad international legitimacy. We therefore seem to find ourselves in a critical juncture for the development of international law regulating cyberoperations in which national security considerations militating in favor of maintaining operational latitude through silence and ambiguity may be gradually giving way to the communicative and norm-consolidation imperatives of collective action and applying the pressures of public diplomacy, which seem to affect the policies even of these states with the most advanced capacity in cyberspace.
The availability of a choice as to whether or not to conduct certain international interactions pursuant to an international law framework is not unique to the field of cyberoperations. It can be found in other areas where states are ambivalent as to whether international law properly serves their interests, or whether they should clearly express themselves on its contents. For example, the failure of several states, including the United States, France, Turkey, and Israel, who have been involved in recent years in use of force action in and around Syria,Footnote 351 to enunciate a clear legal rationale for their activities, suggests a policy of optionality in this field as well. Such a policy can only succeed, however, if a significant number of states with international clout cooperate with it, and do not hold to account states operating outside the four corners of the law.
J. Parallel Tracks
A second feature of state practice in the field of cyberoperations, which the case studies seem to reveal, is the development of parallel tracks of interstate interaction, comprising acknowledged and unacknowledged practices, with each track governed by separate “rules of the game.” Specifically, we believe that the fact that aggressive cyberoperations have resulted, up until now, in limited loss of life and injury, and the fact that the damage inflicted in cases such as the Black-Energy operations in Ukraine appears to have been contained by design, suggest that attacking states are actually adhering to certain restraining norms. In the same vein, one may find restraint in the measured nature of covert responses taken by victim states to cyberoperations. President Obama's allusion to proportionality in responding to the Sony hack,Footnote 352 while promising that some of the response will be covert, underscores the notion that operating outside the international law framework (through exercising a politically available option to do so) does not imply operating in a completely norm-free “track.”
Here too, the situation in cyberspace finds analogies in the physical world. In fact, international law doctrine has long distinguished between usage—stable patterns of state conduct shaped by practice without the sense of a legal obligation—and custom, where practice is backed by opinio juris.Footnote 353 Arguably, norms of an extralegal nature govern the contents of non-legally binding usages. Furthermore, there are several important areas of international relations where interactions are governed by legitimate expectations of conduct, which are not directly regulated by international law, and that exist in parallel to international law frameworks. For example, the informal rules governing the work of regional groupings in international organizations are often adhered to far more scrupulously than the formal rules of the organization in which the members of the groupings participate.Footnote 354
The preference of states to operate in a parallel track, subject to norms other than the rules of international law may even lead them, in certain contexts, to create by way of an international agreement a regulatory framework that operates as an alternative to existing international law frameworks. For example, the Final Act of the 1975 Helsinki Conference, which laid down important norms for the conduct of international relations, was explicitly formulated in a manner that would not ostensibly affect the rights and obligations of the parties to the Accords under international law.Footnote 355 The framing of the Joint Comprehensive Plan of Action on Iran as comprising voluntary measures, not legal undertakings,Footnote 356 is also reflective of the utility in the eyes of certain states of creating a parallel, not strictly legal, track.
The institution of retorsion, which largely operates without an international law framework but nonetheless appears to be subject to notions of proportionality,Footnote 357 is another parallel track measure that supplements and even supplants international law-regulated countermeasures. This latter point is underscored by our case studies in which overt U.S. responses to cyberoperations were typically undertaken in the form of retorsions.Footnote 358 In fact, the resort to acts of retorsion may be reflective of the difficulty of states to choose between the conflicting policy imperatives of silence and ambiguity, on the one hand, and legal transparency, on the other hand. While public in nature, the application of retorsions, unlike countermeasures, does not depend upon the adoption of a clear position on the contents of international law and on the question whether it was violated.
What is exceptional about the “parallel track” of state conduct developed in connection with cyberoperations is its secretive nature, which complicates efforts to identify the norms governing it. The deniability of cyberoperations and counteroperations, and the attendant problem of attribution, adversely affects the power of all norms—formal international law norms and informal “parallel” norms—to guide and explain state conduct. Moreover, whereas adherence to informal rules cannot be normally relied upon to justify a violation of formal rules, in the “below the radar” world of cyberspace, the boundaries between formal and informal may not always be respected. It is this shadowy aspect of cyberoperations, which induces a comparison between such operations and espionage, another field of activity that appears to be operating primarily under informal rules.Footnote 359 Indeed, our findings suggest that one key dilemma confronting states in this field is whether or not to regard cyberoperations as a form of espionage. One can mention in this connection the debate within U.S. circles around the question of whether or not the OPM hack exceeded the expectations from a “normal” case of data theft for intelligence purposes.Footnote 360
K. Gradations in Law Enforcement
Finally, it may be noted that the timid reaction of victim states to cyberoperations directed against them or against third states may suggest that even if the Tallinn Rules reflect in the eyes of states existing international law, they regard the Rules as a rather weak body of law, which do not lend themselves to robust enforcement measures. Such an approach may, in turn, stem from doubts about the utility of invoking international law in response to offensive cyberoperations, given the limited self-help tools it offers victim states and due to the aforementioned attribution challenges. Note that the latter difficulty is further compounded by the absence of an international attribution agency, which could enable states to obtain an internationally authoritative holding on the attribution of responsibility to state or non-state actors, and which could serve as a legitimate basis for collective sanctions against the law violating state.Footnote 361 Yet the limited nature of the responsive measures adopted by victim states may also reflect an interest on their part in maintaining legal ambiguity, which would allow them to engage in due course, if they so wish, in offensive cyberoperations, and to challenge at a subsequent point in time the contents of the Tallinn Rules.
The notion that the enforceability of some international law rules is gradated, that is, that some legal norms are subject to weaker enforcement action than others because of deep ambivalence of states about their utility and precise contents is, again, not unique to the field of cyberoperations. Situations indicative of little appetite to enforce certain international law norms may be found in fields as diverse as humanitarian intervention, where states exercising force in such controversial circumstances have been able to mostly avoid international censure and sanctions,Footnote 362 and the active duty to peacefully resolve disputes,Footnote 363 which is often honored in the breach without direct legal consequences. Chronic underenforcement in such fields may be indicative of the interest of states in maintaining flexibility in relation to the actual application of controversial international norms.
Although all three strategies—optionality, parallel track, and gradated enforcement—can be found in other fields of international law as well, their convergence in the law governing cyberoperations accentuates the particular challenge of regulating this particular field. It is the combination of contested rules and low enforcement prospects that renders cyberspace exceptionally difficult to regulate. As we have discussed above, the Tallinn Rules, which attempted to flesh out an existing regulatory framework, have been challenged as unfit to fully address the risks of cyberoperations, oblivious to important state interests, and non-reflective of the views held by all states. Furthermore, given the problem of attribution, the actual ability of states to effectively rely on international law in this field remains limited.
Hence, the regulation of cyberspace confronts a “perfect storm” of challenging circumstances, resulting in states choosing to operate outside legal frameworks, developing a non-transparent parallel regulatory track offering limited predictability and stability, and accepting chronic conditions of underenforcement. We are of the view that such difficult background conditions for promoting the rule of law in cyberspace put in question the long-term sustainability of the Tallinn Rules as an authoritative articulation of international law governing cyberoperations.
Still, recent developments and the elaboration of international law doctrines applicable to cyberoperations by some government officials suggest that under certain conditions states may be incentivized to apply international law to cyberoperations and to reduce the attendant legal ambiguity. This implies that the utility of enhanced coordination and increased legitimacy may tip the balance in favor of opting for reliance on international law (without necessarily rejecting other measures taken under “parallel tracks”) and for moving to exact a price from the offending state by enforcing the law against it. The Tallinn Rules may play a useful role as a normative focal point for such reliance and enforcement attempts.
V. Conclusion
The criticism directed at the suitability of certain aspects of the Tallinn Rules, and the loose relationship between the Tallinn Rules and post-Tallinn state practice, invite an evaluation of the degree to which states have accepted, or are interested in accepting, the five premises of the Tallinn Rules noted in the introduction to this article, i.e., that harm caused by cyberoperations is comparable to that caused by kinetic attacks; that international law governs cyberoperations; that states exercise sovereignty or control over parts of cyberspace; that cyberattacks are regulated by analogous jus ad bellum and jus in bello rules to those applicable in the kinetic sphere; and that states may incur responsibility over private cyberoperators. The failure of the UN GGE to reaffirm in 2017 the applicability of international law to cyberspace underscores the “wait and see” approach adopted by several states involved in cyberoperations in respect of key aspects of the regulatory framework described in the Tallinn Manuals,Footnote 364 as does the tendency of some states to maintain a policy of silence and ambiguity vis-à-vis international law governing cyberoperations. Although the Tallinn Rules have been criticized by some commenters as not going far enough in limiting the ability of states to conduct cyberoperations in cyberspace, we are seeing some states claiming the opposite, and some going even farther than that by challenging the very suitability of jus ad bellum and jus in bello to cyberoperations.
At the bottom of these disagreements, we find deep uncertainty about the treatment of cyberspace as just another physical space, like land, air, or sea—over which states may exercise sovereignty or control. Such treatment is indeed controversial given the description of cyberspace as “virtual lands.”Footnote 365 Interactions and communities formed in this virtual space are often deterritorialized,Footnote 366 and subject to greater regulatory control by global technological corporations, such as Google, Apple, Facebook, Amazon, and Microsoft, than by states.Footnote 367 Although the presence of physical infrastructures inside state territory does allow states to exercise some degree of control over end-users, routing stations, servers, data-flows, and the like, such control is hard to implement, and is rarely invoked in liberal democracies, since it is largely an anathema to basic human rights and to principles of privacy, freedom of expression and association, and free market economy.
Given the doubts that many state officials seem to have as to the contents of regulation that would best serve the interests of states who find themselves involved in cyberoperations, the uneven capacities of states in this field, and the lack of effective international institutions for attributing responsibility and applying international law norms, it is not surprising that efforts to regulate cyberspace through translating traditional concepts of statehood, including sovereignty, territorial integrity, and international responsibility meet some skepticism and resistance, and shape only to a limited degree state practice. Most significantly, our eleven case studies do not show that states generally accept or rely on the normative categories used in the Tallinn Rules—armed attack, use of force, violations of sovereignty, and violations of due diligence obligations—to draw meaningful legal distinctions in their reactions to cyberoperations. Although states may decide for a variety of reasons not to invoke the rights due to them under international law and prefer instead to pursue a policy of selective reliance on international law (optionality), it is still remarkable that there is so little in the practice of victim states to indicate that they actually guide their conduct when confronted by cyberoperations pursuant to the Tallinn Rules. Statements by senior officials in the United States and the UK questioning some important elements of the regulatory scheme provided in Tallinn Manual 2.0, as well as the aforementioned failure by the UN GGE to agree on the applicability of international law to cyberspace, also cast doubt on whether such elements coincide with contemporary opinio juris.
The uneasy “fit” between traditional international law principles governing the exercise of state power inside and outside its territory, and the regulation of a deterritorialized cyberspace, provides one explanation for the preference given by some states involved in cyberoperations to retaining silence and maintaining ambiguity in relation to their legal position. Since they are not certain that the Tallinn Rules adequately protect their long-term interests, they may be reluctant to formally endorse them or push strongly for their enforcement. And even those states that may be interested in relying on the Tallinn Rules may not be able to publicly do so, in the absence of credible and effective processes for assigning international responsibility, such as an international attribution mechanism. The upshot is that, at this point in time, states seem to prefer to engage in cyberoperations and counteroperations “below the radar,” and to retain, for the time being, some degree of stability in cyberspace by developing “parallel tracks” of restricted attacks, covert retaliation, and overt retorsion, subject to certain notions of proportionality.
This does not mean, however, that no international law regulation of cyberoperations is possible or desirable. For example, there appears to be no reason to allow under international law unprovoked cyberattacks by states against other states, or cyberoperations that deliberately harm civilians not involved in armed activities or criminal enterprises, to the extent that states are able to control the effects of such attacks. Furthermore, one cannot assume that the current policy of silence and ambiguity will remain a dominant strategy in state practice. In fact, recent developments relating to the need of certain states to join forces and respond collectively to cyberoperations and to utilize public diplomacy in this regard may render the Tallinn Rules more relevant than before and could create a greater interest in the establishment of an international attribution agency to improve collective enforcement capabilities.
Ultimately, the approach taken by the Tallinn Manuals represents, like in other fields of international law, a policy choice, which may reflect fully justified professional anxieties of international lawyers about addressing a new field of interaction not contemplated by past lawmakers. The approach taken by the Tallinn Rules drafters has the advantage of avoiding a regulatory void. However, it does expose the Rules, and subsequent attempts to regulate the field on their basis, to academic criticism, due to the imperfect analogy between the regulation of kinetic and cybernetic operations, and puts them under pressure the more states deviate from them or refrain from accepting them because of gaps between the contents of the Rules and what they consider to be their national security interests.
Appendix: Table of Case Studies
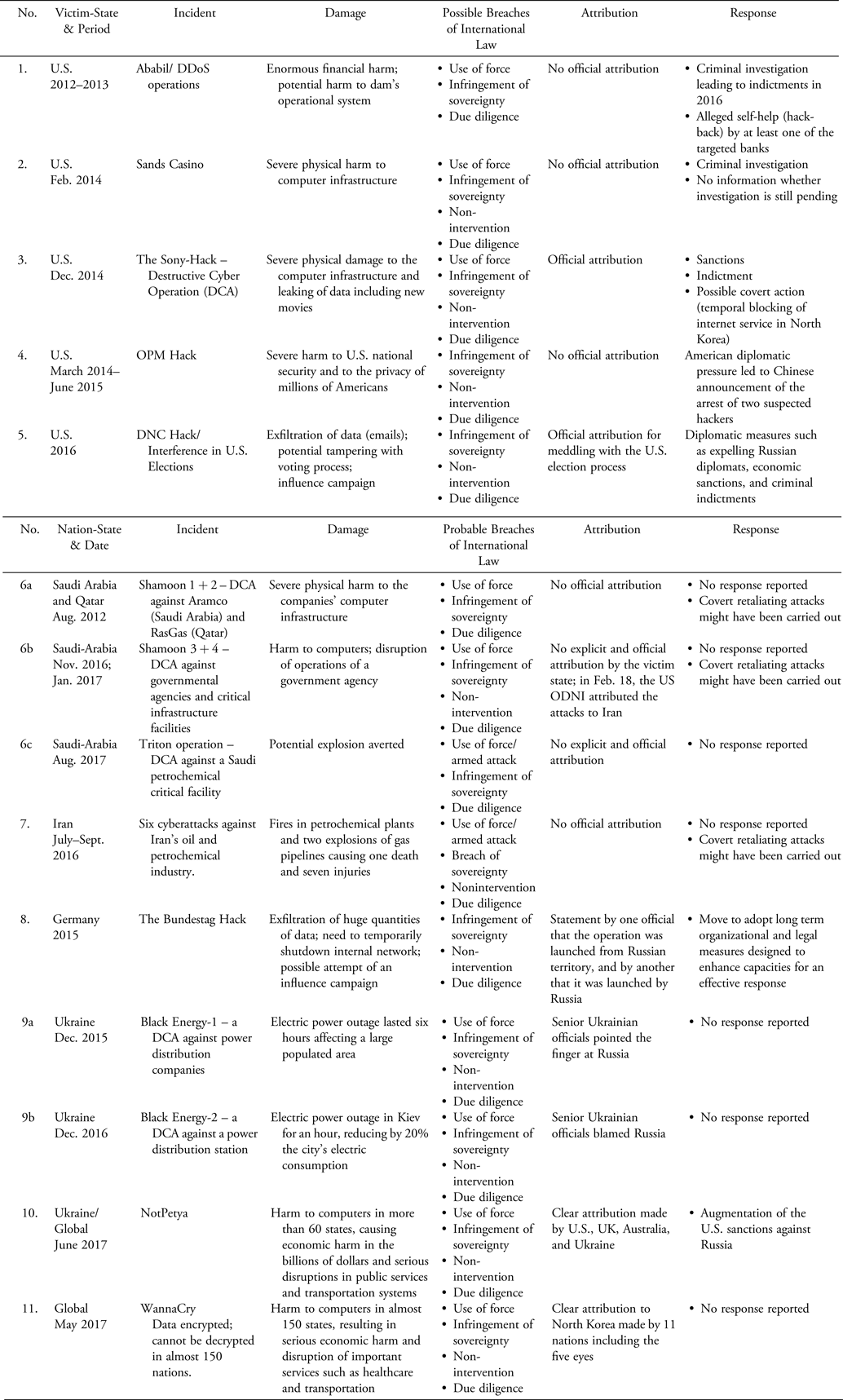




Target article
A Rule Book on the Shelf? Tallinn Manual 2.0 on Cyberoperations and Subsequent State Practice
Related commentaries (5)
Lex Lata comes with a Date; or, What Follows from Referring to the “Tallinn Rules”
On the Shelf, But Close at Hand: The Contribution of Non-State Initiatives to International Cyber Law
The Elephant in the Room: Coercion
The Slow Process of Normativizing Cyberspace
War Without Words